In a latest undertaking, we have been tasked with designing how we might substitute a
Mainframe system with a cloud native software, constructing a roadmap and a
enterprise case to safe funding for the multi-year modernisation effort
required. We have been cautious of the dangers and potential pitfalls of a Huge Design
Up Entrance, so we suggested our shopper to work on a ‘simply sufficient, and simply in
time’ upfront design, with engineering in the course of the first part. Our shopper
preferred our method and chosen us as their companion.
The system was constructed for a UK-based shopper’s Knowledge Platform and
customer-facing merchandise. This was a really complicated and difficult activity given
the dimensions of the Mainframe, which had been constructed over 40 years, with a
number of applied sciences which have considerably modified since they have been
first launched.
Our method is predicated on incrementally shifting capabilities from the
mainframe to the cloud, permitting a gradual legacy displacement moderately than a
“Huge Bang” cutover. So as to do that we wanted to determine locations within the
mainframe design the place we may create seams: locations the place we are able to insert new
conduct with the smallest doable modifications to the mainframe’s code. We are able to
then use these seams to create duplicate capabilities on the cloud, twin run
them with the mainframe to confirm their conduct, after which retire the
mainframe functionality.
Thoughtworks have been concerned for the primary yr of the programme, after which we handed over our work to our shopper
to take it ahead. In that timeframe, we didn’t put our work into manufacturing, nonetheless, we trialled a number of
approaches that may allow you to get began extra rapidly and ease your personal Mainframe modernisation journeys. This
article offers an outline of the context through which we labored, and descriptions the method we adopted for
incrementally shifting capabilities off the Mainframe.
Contextual Background
The Mainframe hosted a various vary of
companies essential to the shopper’s enterprise operations. Our programme
particularly centered on the info platform designed for insights on Shoppers
in UK&I (United Kingdom & Eire). This specific subsystem on the
Mainframe comprised roughly 7 million traces of code, developed over a
span of 40 years. It supplied roughly ~50% of the capabilities of the UK&I
property, however accounted for ~80% of MIPS (Million directions per second)
from a runtime perspective. The system was considerably complicated, the
complexity was additional exacerbated by area duties and considerations
unfold throughout a number of layers of the legacy surroundings.
A number of causes drove the shopper’s resolution to transition away from the
Mainframe surroundings, these are the next:
- Modifications to the system have been gradual and costly. The enterprise subsequently had
challenges retaining tempo with the quickly evolving market, stopping
innovation. - Operational prices related to operating the Mainframe system have been excessive;
the shopper confronted a industrial danger with an imminent value enhance from a core
software program vendor. - While our shopper had the mandatory ability units for operating the Mainframe,
it had confirmed to be laborious to seek out new professionals with experience on this tech
stack, because the pool of expert engineers on this area is proscribed. Moreover,
the job market doesn’t supply as many alternatives for Mainframes, thus individuals
are usually not incentivised to discover ways to develop and function them.
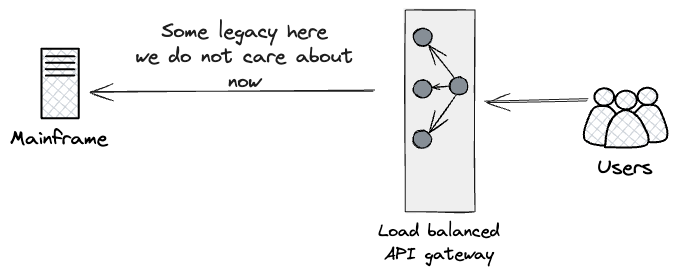
Excessive-level view of Shopper Subsystem
The next diagram exhibits, from a high-level perspective, the varied
parts and actors within the Shopper subsystem.
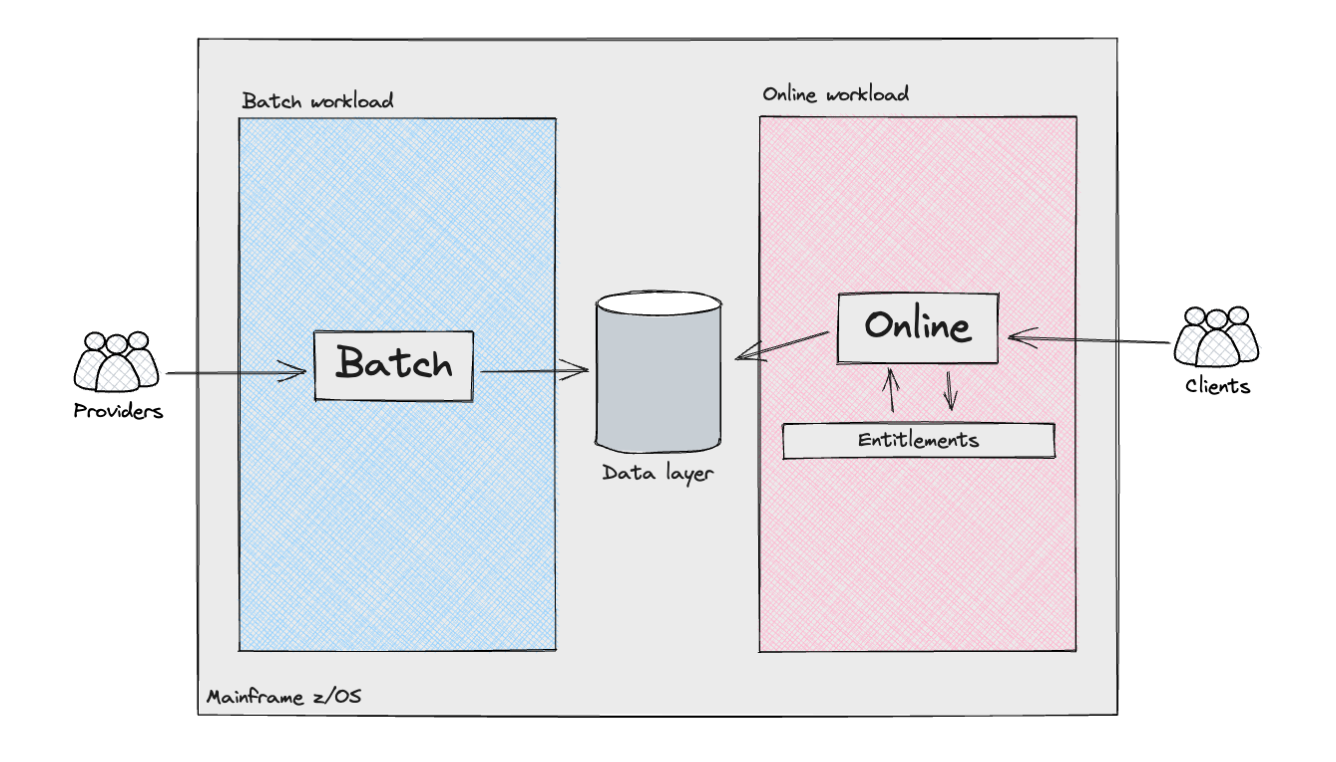
The Mainframe supported two distinct kinds of workloads: batch
processing and, for the product API layers, on-line transactions. The batch
workloads resembled what is often known as an information pipeline. They
concerned the ingestion of semi-structured information from exterior
suppliers/sources, or different inside Mainframe methods, adopted by information
cleaning and modelling to align with the necessities of the Shopper
Subsystem. These pipelines included varied complexities, together with
the implementation of the Id looking logic: in the UK,
not like the USA with its social safety quantity, there is no such thing as a
universally distinctive identifier for residents. Consequently, corporations
working within the UK&I need to make use of customised algorithms to precisely
decide the person identities related to that information.
The web workload additionally introduced vital complexities. The
orchestration of API requests was managed by a number of internally developed
frameworks, which decided this system execution movement by lookups in
datastores, alongside dealing with conditional branches by analysing the
output of the code. We should always not overlook the extent of customisation this
framework utilized for every buyer. For instance, some flows have been
orchestrated with ad-hoc configuration, catering for implementation
particulars or particular wants of the methods interacting with our shopper’s
on-line merchandise. These configurations have been distinctive at first, however they
possible turned the norm over time, as our shopper augmented their on-line
choices.
This was applied via an Entitlements engine which operated
throughout layers to make sure that clients accessing merchandise and underlying
information have been authenticated and authorised to retrieve both uncooked or
aggregated information, which might then be uncovered to them via an API
response.
Incremental Legacy Displacement: Ideas, Advantages, and
Issues
Contemplating the scope, dangers, and complexity of the Shopper Subsystem,
we believed the next rules can be tightly linked with us
succeeding with the programme:
- Early Threat Discount: With engineering ranging from the
starting, the implementation of a “Fail-Quick” method would assist us
determine potential pitfalls and uncertainties early, thus stopping
delays from a programme supply standpoint. These have been: - End result Parity: The shopper emphasised the significance of
upholding final result parity between the present legacy system and the
new system (It is very important word that this idea differs from
Characteristic Parity). Within the shopper’s Legacy system, varied
attributes have been generated for every shopper, and given the strict
business laws, sustaining continuity was important to make sure
contractual compliance. We would have liked to proactively determine
discrepancies in information early on, promptly handle or clarify them, and
set up belief and confidence with each our shopper and their
respective clients at an early stage. - Cross-functional necessities: The Mainframe is a extremely
performant machine, and there have been uncertainties {that a} resolution on
the Cloud would fulfill the Cross-functional necessities. - Ship Worth Early: Collaboration with the shopper would
guarantee we may determine a subset of essentially the most crucial Enterprise
Capabilities we may ship early, making certain we may break the system
aside into smaller increments. These represented thin-slices of the
general system. Our aim was to construct upon these slices iteratively and
incessantly, serving to us speed up our general studying within the area.
Moreover, working via a thin-slice helps cut back the cognitive
load required from the group, thus stopping evaluation paralysis and
making certain worth can be persistently delivered. To attain this, a
platform constructed across the Mainframe that gives higher management over
shoppers’ migration methods performs an important function. Utilizing patterns equivalent to
Darkish Launching and Canary
Launch would place us within the driver’s seat for a clean
transition to the Cloud. Our aim was to attain a silent migration
course of, the place clients would seamlessly transition between methods
with none noticeable affect. This might solely be doable via
complete comparability testing and steady monitoring of outputs
from each methods.
With the above rules and necessities in thoughts, we opted for an
Incremental Legacy Displacement method together with Twin
Run. Successfully, for every slice of the system we have been rebuilding on the
Cloud, we have been planning to feed each the brand new and as-is system with the
similar inputs and run them in parallel. This enables us to extract each
methods’ outputs and examine if they’re the identical, or at the very least inside an
acceptable tolerance. On this context, we outlined Incremental Twin
Run as: utilizing a Transitional
Structure to help slice-by-slice displacement of functionality
away from a legacy surroundings, thereby enabling goal and as-is methods
to run briefly in parallel and ship worth.
We determined to undertake this architectural sample to strike a stability
between delivering worth, discovering and managing dangers early on,
making certain final result parity, and sustaining a clean transition for our
shopper all through the period of the programme.
Incremental Legacy Displacement method
To perform the offloading of capabilities to our goal
structure, the group labored intently with Mainframe SMEs (Topic Matter
Specialists) and our shopper’s engineers. This collaboration facilitated a
simply sufficient understanding of the present as-is panorama, when it comes to each
technical and enterprise capabilities; it helped us design a Transitional
Structure to attach the present Mainframe to the Cloud-based system,
the latter being developed by different supply workstreams within the
programme.
Our method started with the decomposition of the
Shopper subsystem into particular enterprise and technical domains, together with
information load, information retrieval & aggregation, and the product layer
accessible via external-facing APIs.
Due to our shopper’s enterprise
function, we recognised early that we may exploit a serious technical boundary to organise our programme. The
shopper’s workload was largely analytical, processing principally exterior information
to provide perception which was offered on to shoppers. We subsequently noticed an
alternative to separate our transformation programme in two components, one round
information curation, the opposite round information serving and product use circumstances utilizing
information interactions as a seam. This was the primary excessive stage seam recognized.
Following that, we then wanted to additional break down the programme into
smaller increments.
On the info curation facet, we recognized that the info units have been
managed largely independently of one another; that’s, whereas there have been
upstream and downstream dependencies, there was no entanglement of the datasets throughout curation, i.e.
ingested information units had a one to at least one mapping to their enter recordsdata.
.
We then collaborated intently with SMEs to determine the seams
inside the technical implementation (laid out beneath) to plan how we may
ship a cloud migration for any given information set, ultimately to the extent
the place they might be delivered in any order (Database Writers Processing Pipeline Seam, Coarse Seam: Batch Pipeline Step Handoff as Seam,
and Most Granular: Knowledge Attribute
Seam). So long as up- and downstream dependencies may alternate information
from the brand new cloud system, these workloads might be modernised
independently of one another.
On the serving and product facet, we discovered that any given product used
80% of the capabilities and information units that our shopper had created. We
wanted to discover a completely different method. After investigation of the way in which entry
was offered to clients, we discovered that we may take a “buyer section”
method to ship the work incrementally. This entailed discovering an
preliminary subset of consumers who had bought a smaller proportion of the
capabilities and information, decreasing the scope and time wanted to ship the
first increment. Subsequent increments would construct on prime of prior work,
enabling additional buyer segments to be minimize over from the as-is to the
goal structure. This required utilizing a unique set of seams and
transitional structure, which we talk about in Database Readers and Downstream processing as a Seam.
Successfully, we ran an intensive evaluation of the parts that, from a
enterprise perspective, functioned as a cohesive entire however have been constructed as
distinct components that might be migrated independently to the Cloud and
laid this out as a programme of sequenced increments.
Seams
Our transitional structure was principally influenced by the Legacy seams we may uncover inside the Mainframe. You
can consider them because the junction factors the place code, packages, or modules
meet. In a legacy system, they might have been deliberately designed at
strategic locations for higher modularity, extensibility, and
maintainability. If so, they are going to possible stand out
all through the code, though when a system has been beneath growth for
quite a lot of a long time, these seams have a tendency to cover themselves amongst the
complexity of the code. Seams are significantly precious as a result of they will
be employed strategically to change the behaviour of functions, for
instance to intercept information flows inside the Mainframe permitting for
capabilities to be offloaded to a brand new system.
Figuring out technical seams and precious supply increments was a
symbiotic course of; prospects within the technical space fed the choices
that we may use to plan increments, which in flip drove the transitional
structure wanted to help the programme. Right here, we step a stage decrease
in technical element to debate options we deliberate and designed to allow
Incremental Legacy Displacement for our shopper. It is very important word that these have been constantly refined
all through our engagement as we acquired extra data; some went so far as being deployed to check
environments, while others have been spikes. As we undertake this method on different large-scale Mainframe modernisation
programmes, these approaches shall be additional refined with our freshest hands-on expertise.
Exterior interfaces
We examined the exterior interfaces uncovered by the Mainframe to information
Suppliers and our shopper’s Clients. We may apply Occasion Interception on these integration factors
to permit the transition of external-facing workload to the cloud, so the
migration can be silent from their perspective. There have been two sorts
of interfaces into the Mainframe: a file-based switch for Suppliers to
provide information to our shopper, and a web-based set of APIs for Clients to
work together with the product layer.
Batch enter as seam
The primary exterior seam that we discovered was the file-transfer
service.
Suppliers may switch recordsdata containing information in a semi-structured
format through two routes: a web-based GUI (Graphical Consumer Interface) for
file uploads interacting with the underlying file switch service, or
an FTP-based file switch to the service straight for programmatic
entry.
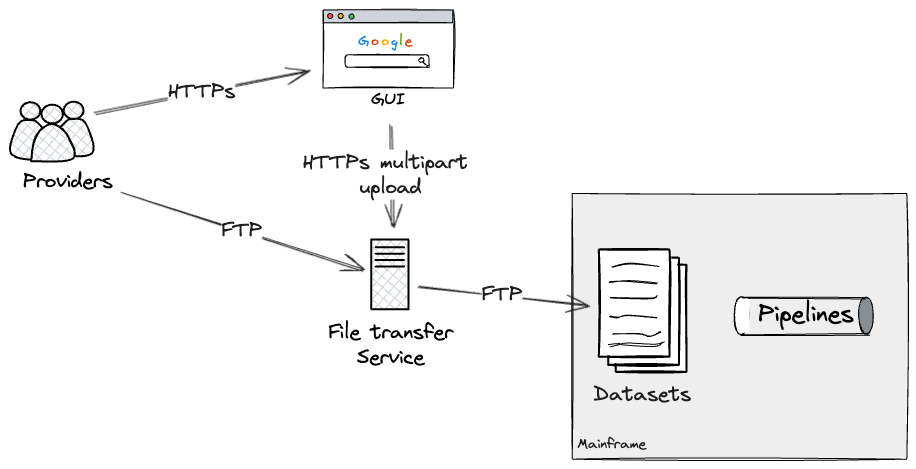
The file switch service decided, on a per supplier and file
foundation, what datasets on the Mainframe ought to be up to date. These would
in flip execute the related pipelines via dataset triggers, which
have been configured on the batch job scheduler.
Assuming we may rebuild every pipeline as an entire on the Cloud
(word that later we are going to dive deeper into breaking down bigger
pipelines into workable chunks), our method was to construct an
particular person pipeline on the cloud, and twin run it with the mainframe
to confirm they have been producing the identical outputs. In our case, this was
doable via making use of extra configurations on the File
switch service, which forked uploads to each Mainframe and Cloud. We
have been capable of take a look at this method utilizing a production-like File switch
service, however with dummy information, operating on take a look at environments.
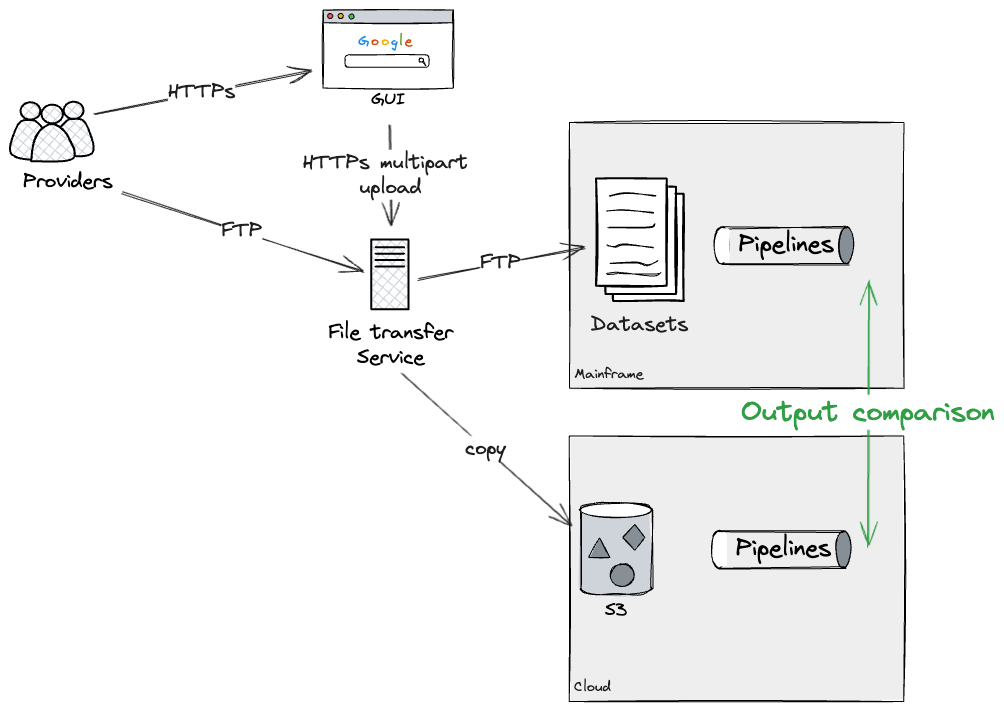
This is able to enable us to Twin Run every pipeline each on Cloud and
Mainframe, for so long as required, to achieve confidence that there have been
no discrepancies. Ultimately, our method would have been to use an
extra configuration to the File switch service, stopping
additional updates to the Mainframe datasets, subsequently leaving as-is
pipelines deprecated. We didn’t get to check this final step ourselves
as we didn’t full the rebuild of a pipeline finish to finish, however our
technical SMEs have been accustomed to the configurations required on the
File switch service to successfully deprecate a Mainframe
pipeline.
API Entry as Seam
Moreover, we adopted an identical technique for the exterior dealing with
APIs, figuring out a seam across the pre-existing API Gateway uncovered
to Clients, representing their entrypoint to the Shopper
Subsystem.
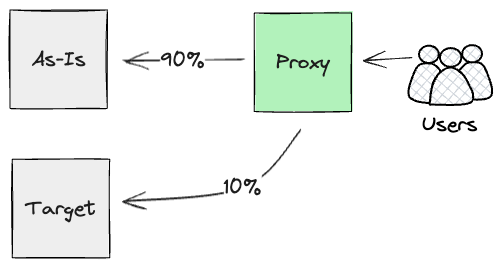
Drawing from Twin Run, the method we designed can be to place a
proxy excessive up the chain of HTTPS calls, as near customers as doable.
We have been searching for one thing that would parallel run each streams of
calls (the As-Is mainframe and newly constructed APIs on Cloud), and report
again on their outcomes.

Successfully, we have been planning to make use of Darkish
Launching for the brand new Product layer, to achieve early confidence
within the artefact via intensive and steady monitoring of their
outputs. We didn’t prioritise constructing this proxy within the first yr;
to take advantage of its worth, we wanted to have nearly all of performance
rebuilt on the product stage. Nevertheless, our intentions have been to construct it
as quickly as any significant comparability exams might be run on the API
layer, as this part would play a key function for orchestrating darkish
launch comparability exams. Moreover, our evaluation highlighted we
wanted to be careful for any side-effects generated by the Merchandise
layer. In our case, the Mainframe produced uncomfortable side effects, equivalent to
billing occasions. Consequently, we might have wanted to make intrusive
Mainframe code modifications to stop duplication and be sure that
clients wouldn’t get billed twice.
Equally to the Batch enter seam, we may run these requests in
parallel for so long as it was required. Finally although, we might
use Canary
Launch on the
proxy layer to chop over customer-by-customer to the Cloud, therefore
decreasing, incrementally, the workload executed on the Mainframe.
Inside interfaces
Following that, we carried out an evaluation of the inner parts
inside the Mainframe to pinpoint the particular seams we may leverage to
migrate extra granular capabilities to the Cloud.
Coarse Seam: Knowledge interactions as a Seam
One of many main areas of focus was the pervasive database
accesses throughout packages. Right here, we began our evaluation by figuring out
the packages that have been both writing, studying, or doing each with the
database. Treating the database itself as a seam allowed us to interrupt
aside flows that relied on it being the connection between
packages.
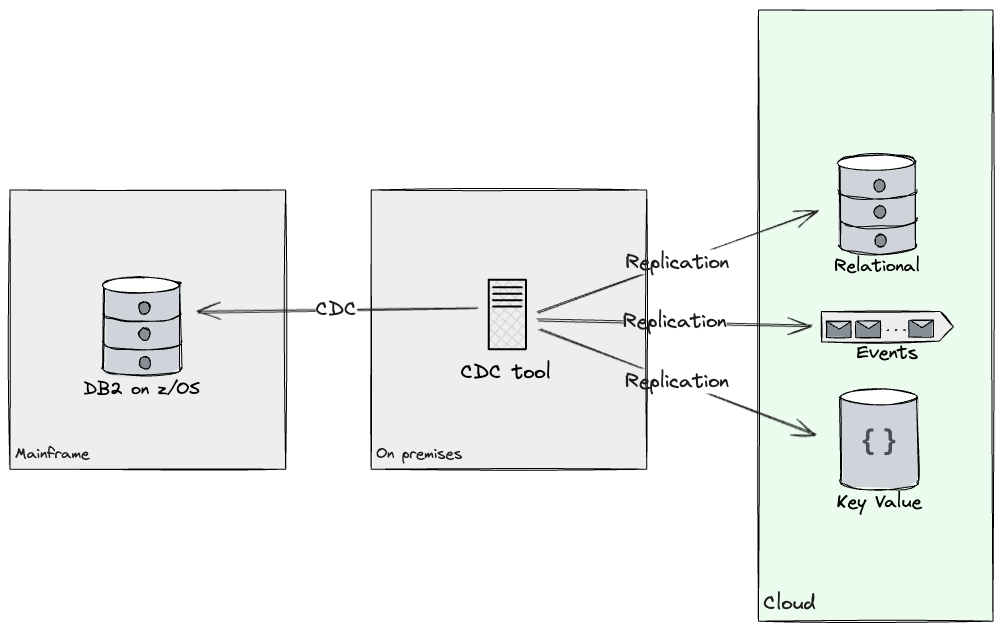
Database Readers
Relating to Database readers, to allow new Knowledge API growth in
the Cloud surroundings, each the Mainframe and the Cloud system wanted
entry to the identical information. We analysed the database tables accessed by
the product we picked as a primary candidate for migrating the primary
buyer section, and labored with shopper groups to ship an information
replication resolution. This replicated the required tables from the take a look at database to the Cloud utilizing Change
Knowledge Seize (CDC) methods to synchronise sources to targets. By
leveraging a CDC software, we have been capable of replicate the required
subset of knowledge in a near-real time trend throughout goal shops on
Cloud. Additionally, replicating information gave us alternatives to revamp its
mannequin, as our shopper would now have entry to shops that weren’t
solely relational (e.g. Doc shops, Occasions, Key-Worth and Graphs
have been thought-about). Criterias equivalent to entry patterns, question complexity,
and schema flexibility helped decide, for every subset of knowledge, what
tech stack to duplicate into. Throughout the first yr, we constructed
replication streams from DB2 to each Kafka and Postgres.
At this level, capabilities applied via packages
studying from the database might be rebuilt and later migrated to
the Cloud, incrementally.
Database Writers
With regard to database writers, which have been principally made up of batch
workloads operating on the Mainframe, after cautious evaluation of the info
flowing via and out of them, we have been capable of apply Extract Product Strains to determine
separate domains that would execute independently of one another
(operating as a part of the identical movement was simply an implementation element we
may change).
Working with such atomic items, and round their respective seams,
allowed different workstreams to begin rebuilding a few of these pipelines
on the cloud and evaluating the outputs with the Mainframe.

Along with constructing the transitional structure, our group was
chargeable for offering a variety of companies that have been utilized by different
workstreams to engineer their information pipelines and merchandise. On this
particular case, we constructed batch jobs on Mainframe, executed
programmatically by dropping a file within the file switch service, that
would extract and format the journals that these pipelines have been
producing on the Mainframe, thus permitting our colleagues to have tight
suggestions loops on their work via automated comparability testing.
After making certain that outcomes remained the identical, our method for the
future would have been to allow different groups to cutover every
sub-pipeline one after the other.
The artefacts produced by a sub-pipeline could also be required on the
Mainframe for additional processing (e.g. On-line transactions). Thus, the
method we opted for, when these pipelines would later be full
and on the Cloud, was to make use of Legacy Mimic
and replicate information again to the Mainframe, for so long as the aptitude dependant on this information can be
moved to Cloud too. To attain this, we have been contemplating using the identical CDC software for replication to the
Cloud. On this situation, data processed on Cloud can be saved as occasions on a stream. Having the
Mainframe eat this stream straight appeared complicated, each to construct and to check the system for regressions,
and it demanded a extra invasive method on the legacy code. So as to mitigate this danger, we designed an
adaption layer that may remodel the info again into the format the Mainframe may work with, as if that
information had been produced by the Mainframe itself. These transformation capabilities, if
easy, could also be supported by your chosen replication software, however
in our case we assumed we wanted customized software program to be constructed alongside
the replication software to cater for added necessities from the
Cloud. It is a widespread situation we see through which companies take the
alternative, coming from rebuilding current processing from scratch,
to enhance them (e.g. by making them extra environment friendly).
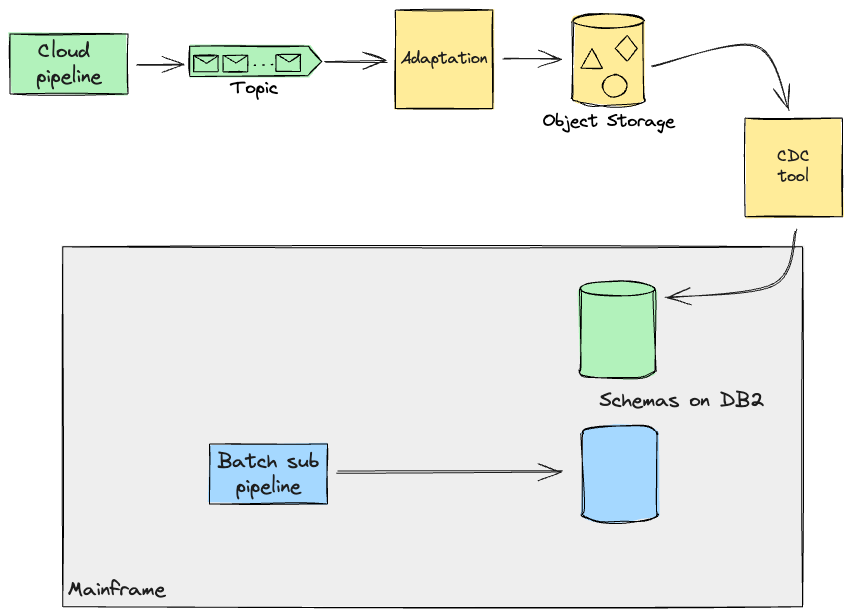
In abstract, working intently with SMEs from the client-side helped
us problem the present implementation of Batch workloads on the
Mainframe, and work out different discrete pipelines with clearer
information boundaries. Notice that the pipelines we have been coping with didn’t
overlap on the identical data, because of the boundaries we had outlined with
the SMEs. In a later part, we are going to look at extra complicated circumstances that
we have now needed to cope with.
Coarse Seam: Batch Pipeline Step Handoff
Doubtless, the database gained’t be the one seam you’ll be able to work with. In
our case, we had information pipelines that, along with persisting their
outputs on the database, have been serving curated information to downstream
pipelines for additional processing.
For these situations, we first recognized the handshakes between
pipelines. These consist normally of state persevered in flat / VSAM
(Digital Storage Entry Methodology) recordsdata, or probably TSQs (Non permanent
Storage Queues). The next exhibits these hand-offs between pipeline
steps.
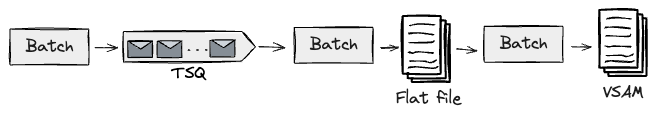
For example, we have been taking a look at designs for migrating a downstream pipeline studying a curated flat file
saved upstream. This downstream pipeline on the Mainframe produced a VSAM file that may be queried by
on-line transactions. As we have been planning to construct this event-driven pipeline on the Cloud, we selected to
leverage the CDC software to get this information off the mainframe, which in flip would get transformed right into a stream of
occasions for the Cloud information pipelines to eat. Equally to what we have now reported earlier than, our Transitional
Structure wanted to make use of an Adaptation layer (e.g. Schema translation) and the CDC software to repeat the
artefacts produced on Cloud again to the Mainframe.
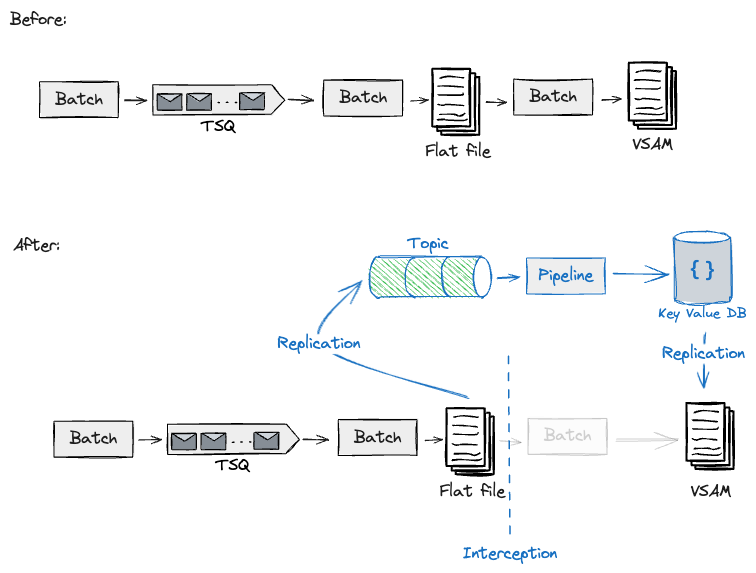
Via using these handshakes that we had beforehand
recognized, we have been capable of construct and take a look at this interception for one
exemplary pipeline, and design additional migrations of
upstream/downstream pipelines on the Cloud with the identical method,
utilizing Legacy
Mimic
to feed again the Mainframe with the mandatory information to proceed with
downstream processing. Adjoining to those handshakes, we have been making
non-trivial modifications to the Mainframe to permit information to be extracted and
fed again. Nevertheless, we have been nonetheless minimising dangers by reusing the identical
batch workloads on the core with completely different job triggers on the edges.
Granular Seam: Knowledge Attribute
In some circumstances the above approaches for inside seam findings and
transition methods don’t suffice, because it occurred with our undertaking
because of the measurement of the workload that we have been trying to cutover, thus
translating into larger dangers for the enterprise. In one in all our
situations, we have been working with a discrete module feeding off the info
load pipelines: Id curation.
Shopper Id curation was a
complicated house, and in our case it was a differentiator for our shopper;
thus, they may not afford to have an final result from the brand new system
much less correct than the Mainframe for the UK&I inhabitants. To
efficiently migrate the complete module to the Cloud, we would want to
construct tens of id search guidelines and their required database
operations. Due to this fact, we wanted to interrupt this down additional to maintain
modifications small, and allow delivering incessantly to maintain dangers low.
We labored intently with the SMEs and Engineering groups with the intention
to determine traits within the information and guidelines, and use them as
seams, that may enable us to incrementally cutover this module to the
Cloud. Upon evaluation, we categorised these guidelines into two distinct
teams: Easy and Advanced.
Easy guidelines may run on each methods, supplied
they ate up completely different information segments (i.e. separate pipelines
upstream), thus they represented a chance to additional break aside
the id module house. They represented the bulk (circa 70%)
triggered in the course of the ingestion of a file. These guidelines have been accountable
for establishing an affiliation between an already current id,
and a brand new information document.
However, the Advanced guidelines have been triggered by circumstances the place
an information document indicated the necessity for an id change, equivalent to
creation, deletion, or updation. These guidelines required cautious dealing with
and couldn’t be migrated incrementally. It’s because an replace to
an id might be triggered by a number of information segments, and working
these guidelines in each methods in parallel may result in id drift
and information high quality loss. They required a single system minting
identities at one cut-off date, thus we designed for a giant bang
migration method.
In our authentic understanding of the Id module on the
Mainframe, pipelines ingesting information triggered modifications on DB2 ensuing
in an updated view of the identities, information data, and their
associations.
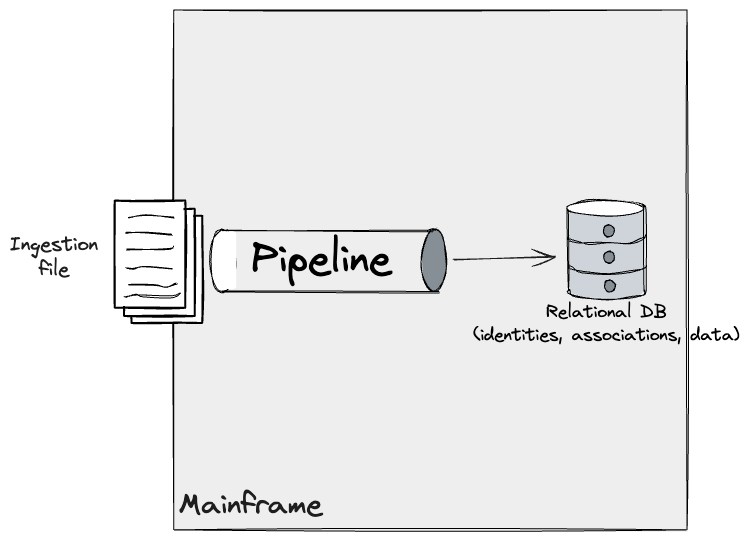
Moreover, we recognized a discrete Id module and refined
this mannequin to replicate a deeper understanding of the system that we had
found with the SMEs. This module fed information from a number of information
pipelines, and utilized Easy and Advanced guidelines to DB2.
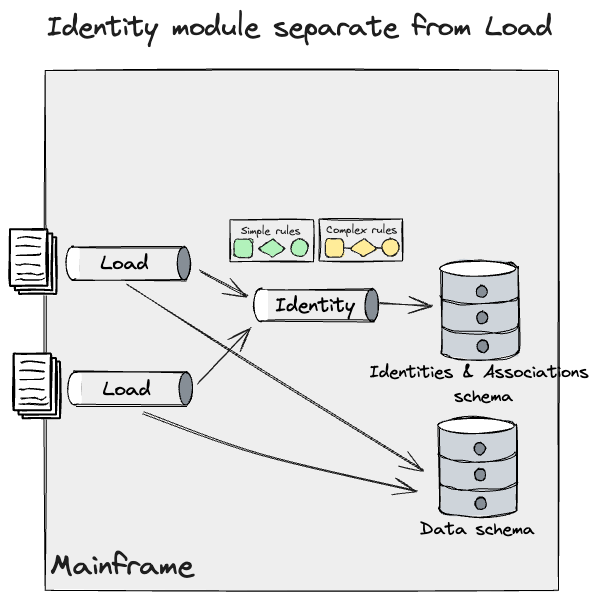
Now, we may apply the identical methods we wrote about earlier for
information pipelines, however we required a extra granular and incremental
method for the Id one.
We deliberate to deal with the Easy guidelines that would run on each
methods, with a caveat that they operated on completely different information segments,
as we have been constrained to having just one system sustaining id
information. We labored on a design that used Batch Pipeline Step Handoff and
utilized Occasion Interception to seize and fork the info (briefly
till we are able to affirm that no information is misplaced between system handoffs)
feeding the Id pipeline on the Mainframe. This is able to enable us to
take a divide and conquer method with the recordsdata ingested, operating a
parallel workload on the Cloud which might execute the Easy guidelines
and apply modifications to identities on the Mainframe, and construct it
incrementally. There have been many guidelines that fell beneath the Easy
bucket, subsequently we wanted a functionality on the goal Id module
to fall again to the Mainframe in case a rule which was not but
applied wanted to be triggered. This regarded just like the
following:
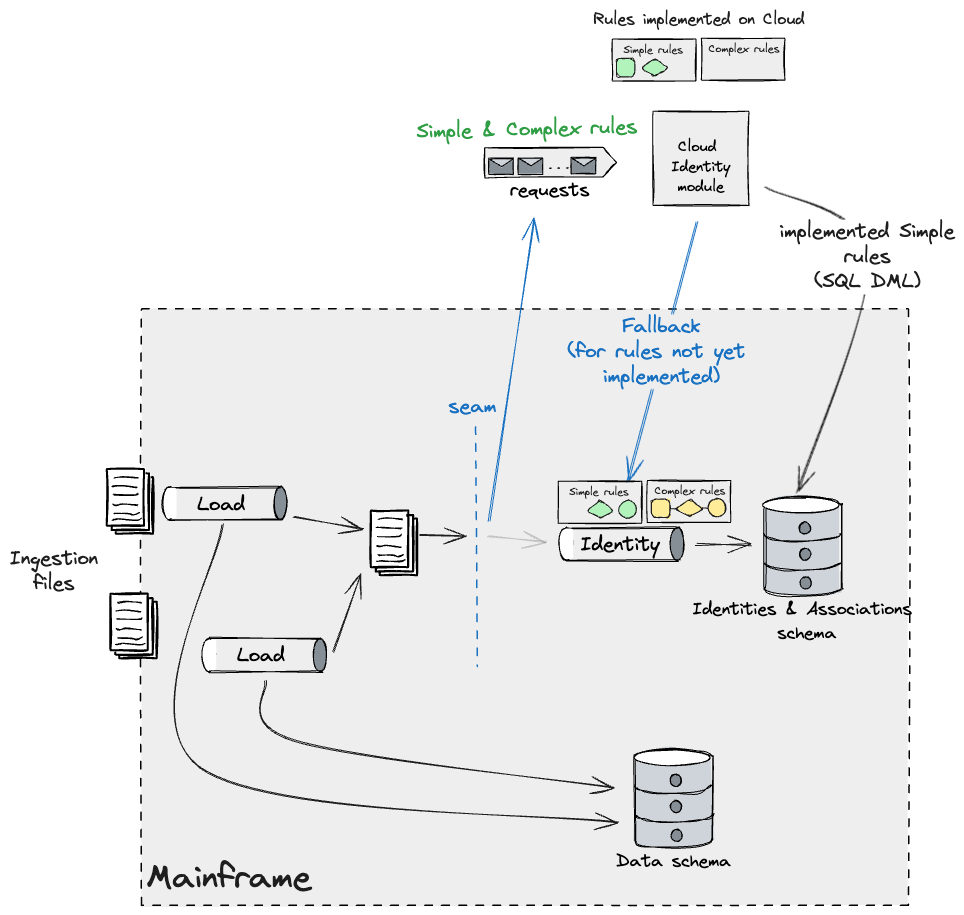
As new builds of the Cloud Id module get launched, we might
see much less guidelines belonging to the Easy bucket being utilized via
the fallback mechanism. Ultimately solely the Advanced ones shall be
observable via that leg. As we beforehand talked about, these wanted
to be migrated multi function go to minimise the affect of id drift.
Our plan was to construct Advanced guidelines incrementally in opposition to a Cloud
database duplicate and validate their outcomes via intensive
comparability testing.
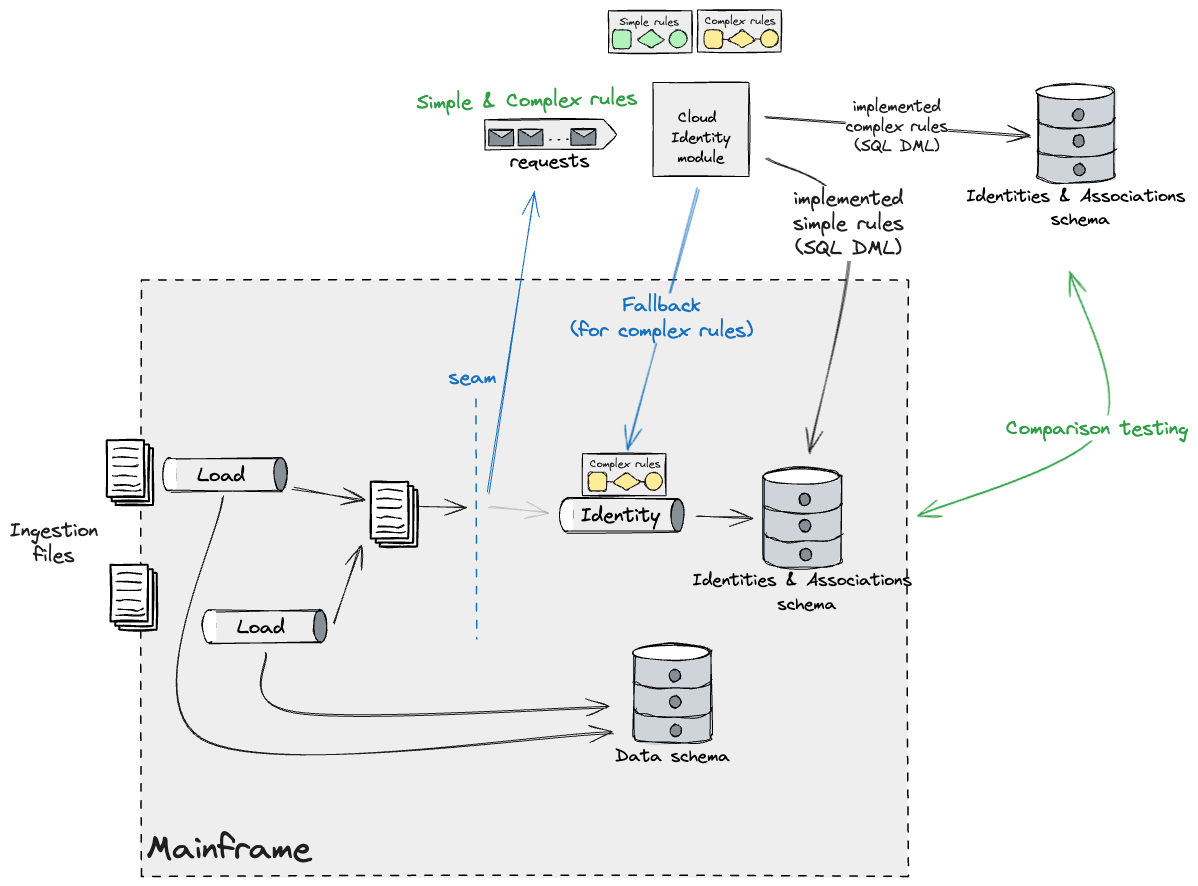
As soon as all guidelines have been constructed, we might launch this code and disable
the fallback technique to the Mainframe. Keep in mind that upon
releasing this, the Mainframe Identities and Associations information turns into
successfully a duplicate of the brand new Main retailer managed by the Cloud
Id module. Due to this fact, replication is required to maintain the
mainframe functioning as is.
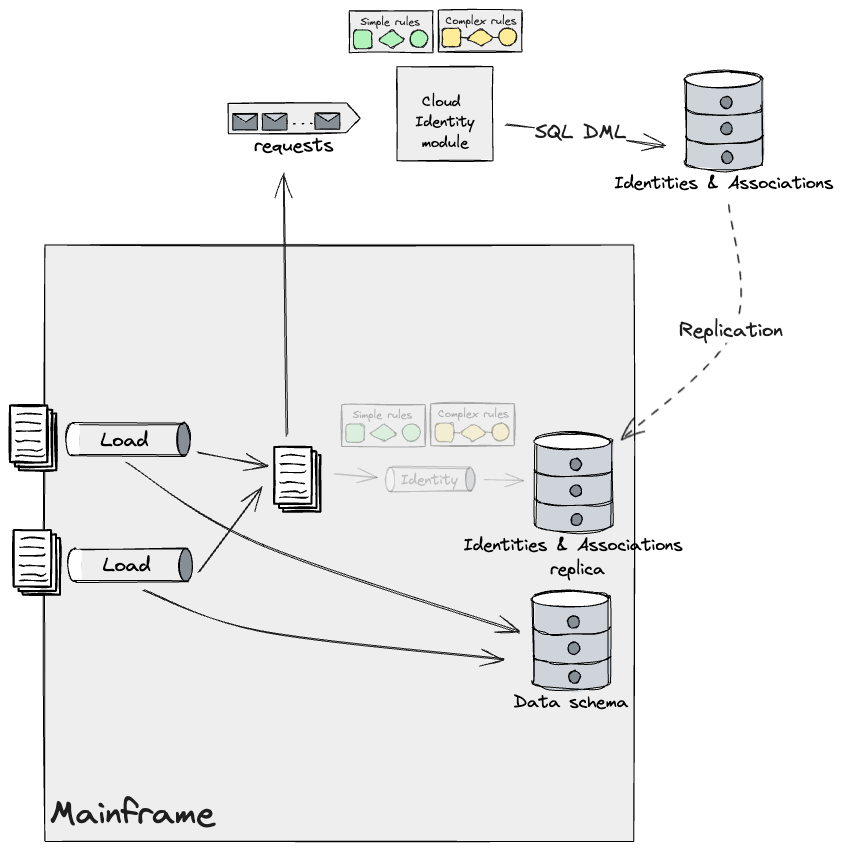
As beforehand talked about in different sections, our design employed
Legacy Mimic and an Anti-Corruption Layer that may translate information
from the Mainframe to the Cloud mannequin and vice versa. This layer
consisted of a collection of Adapters throughout the methods, making certain information
would movement out as a stream from the Mainframe for the Cloud to eat
utilizing event-driven information pipelines, and as flat recordsdata again to the
Mainframe to permit current Batch jobs to course of them. For
simplicity, the diagrams above don’t present these adapters, however they
can be applied every time information flowed throughout methods, regardless
of how granular the seam was. Sadly, our work right here was principally
evaluation and design and we weren’t capable of take it to the subsequent step
and validate our assumptions finish to finish, aside from operating Spikes to
be sure that a CDC software and the File switch service might be
employed to ship information out and in of the Mainframe, within the required
format. The time required to construct the required scaffolding across the
Mainframe, and reverse engineer the as-is pipelines to collect the
necessities was appreciable and past the timeframe of the primary
part of the programme.
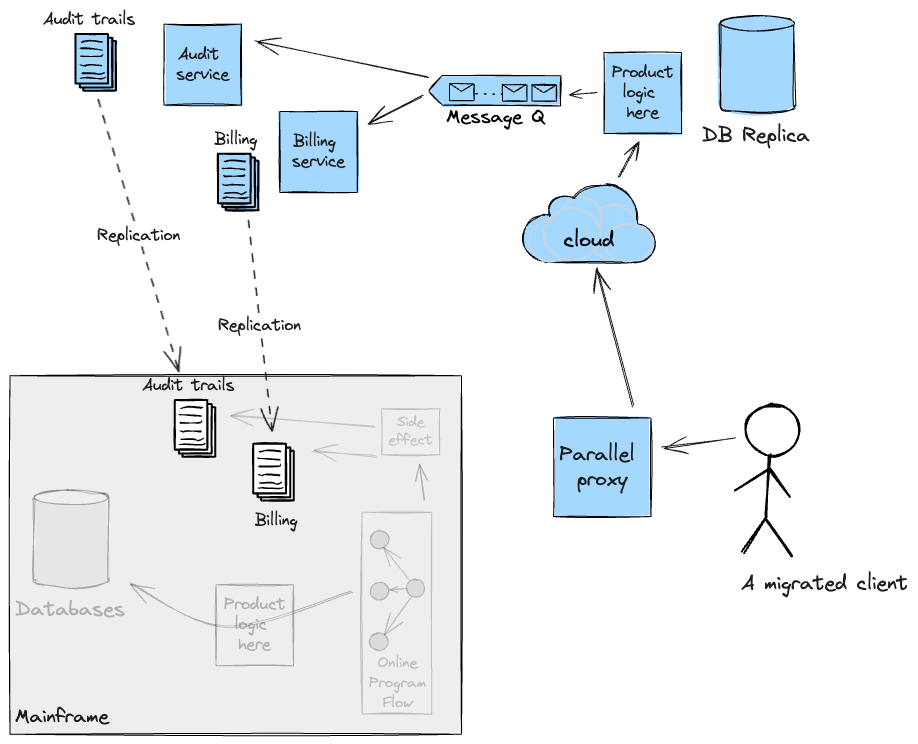
Granular Seam: Downstream processing handoff
Just like the method employed for upstream pipelines to feed
downstream batch workloads, Legacy Mimic Adapters have been employed for
the migration of the On-line movement. Within the current system, a buyer
API name triggers a collection of packages producing side-effects, equivalent to
billing and audit trails, which get persevered in applicable
datastores (principally Journals) on the Mainframe.
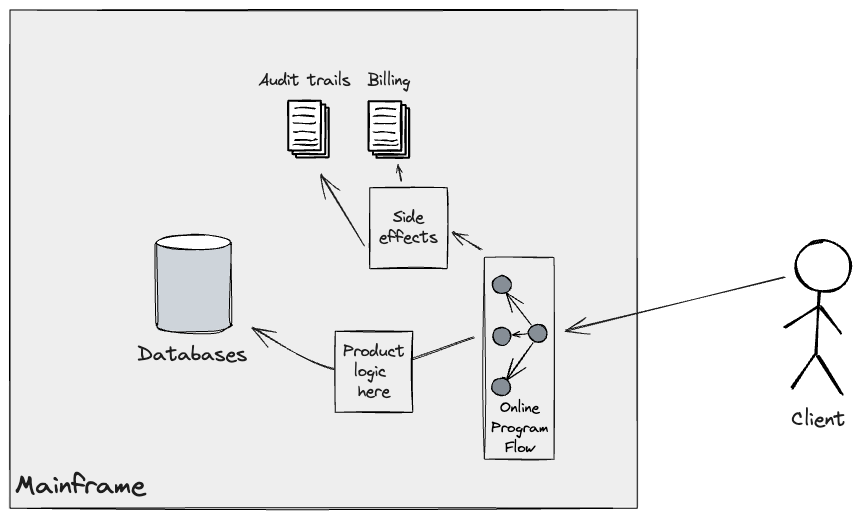
To efficiently transition incrementally the web movement to the
Cloud, we wanted to make sure these side-effects would both be dealt with
by the brand new system straight, thus rising scope on the Cloud, or
present adapters again to the Mainframe to execute and orchestrate the
underlying program flows chargeable for them. In our case, we opted
for the latter utilizing CICS net companies. The answer we constructed was
examined for practical necessities; cross-functional ones (equivalent to
Latency and Efficiency) couldn’t be validated because it proved
difficult to get production-like Mainframe take a look at environments within the
first part. The next diagram exhibits, based on the
implementation of our Adapter, what the movement for a migrated buyer
would appear to be.
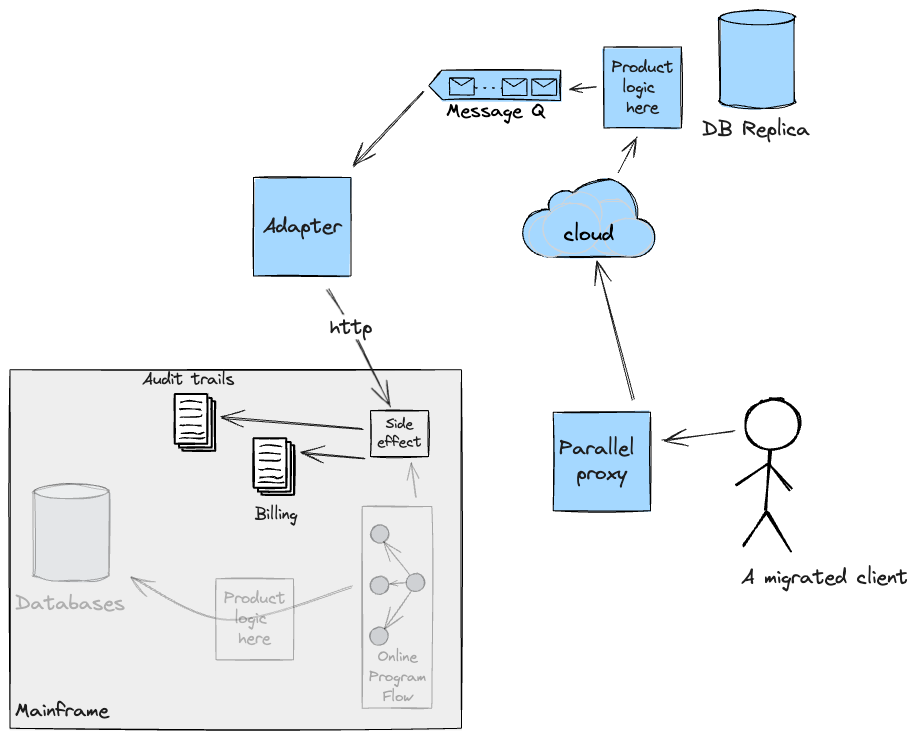
It’s value noting that Adapters have been deliberate to be non permanent
scaffolding. They might not have served a sound function when the Cloud
was capable of deal with these side-effects by itself after which level we
deliberate to duplicate the info again to the Mainframe for so long as
required for continuity.
Knowledge Replication to allow new product growth
Constructing on the incremental method above, organisations could have
product concepts which are based mostly totally on analytical or aggregated information
from the core information held on the Mainframe. These are usually the place there
is much less of a necessity for up-to-date info, equivalent to reporting use circumstances
or summarising information over trailing durations. In these conditions, it’s
doable to unlock enterprise advantages earlier via the even handed use of
information replication.
When carried out effectively, this could allow new product growth via a
comparatively smaller funding earlier which in flip brings momentum to the
modernisation effort.
In our latest undertaking, our shopper had already departed on this journey,
utilizing a CDC software to duplicate core tables from DB2 to the Cloud.
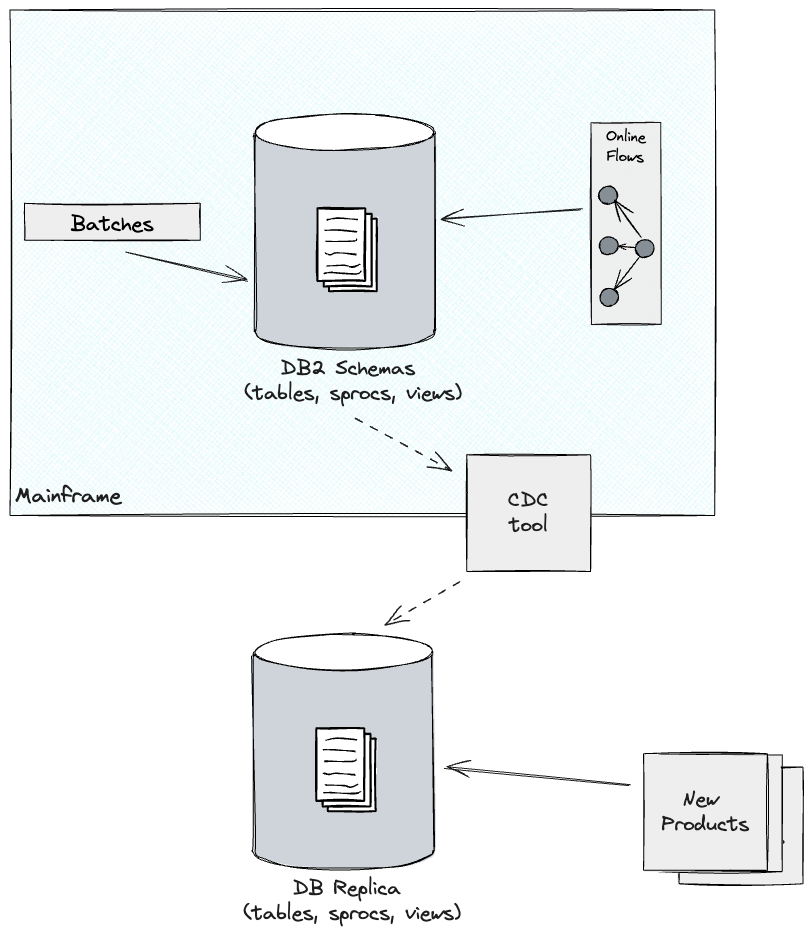
Whereas this was nice when it comes to enabling new merchandise to be launched,
it wasn’t with out its downsides.
Until you’re taking steps to summary the schema when replicating a
database, then your new cloud merchandise shall be coupled to the legacy
schema as quickly as they’re constructed. This may possible hamper any subsequent
innovation that you could be want to do in your goal surroundings as you’ve
now obtained a further drag issue on altering the core of the applying;
however this time it’s worse as you gained’t need to make investments once more in altering the
new product you’ve simply funded. Due to this fact, our proposed design consisted
of additional projections from the duplicate database into optimised shops and
schemas, upon which new merchandise can be constructed.
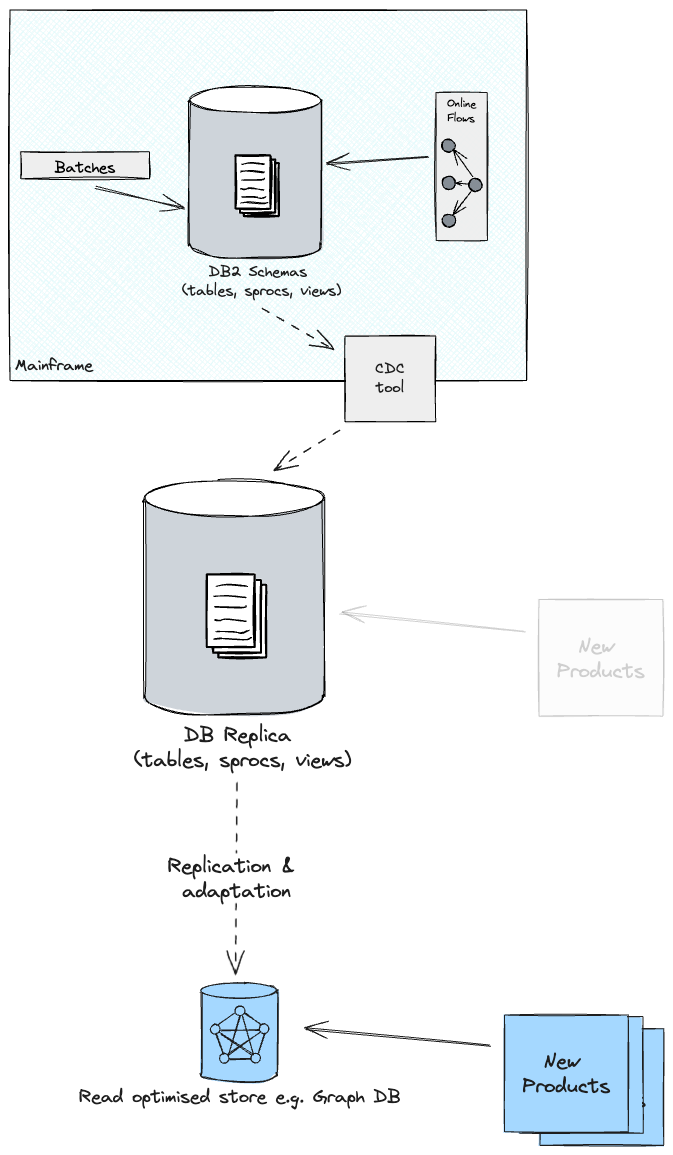
This is able to give us the chance to refactor the Schema, and at occasions
transfer components of the info mannequin into non-relational shops, which might
higher deal with the question patterns noticed with the SMEs.
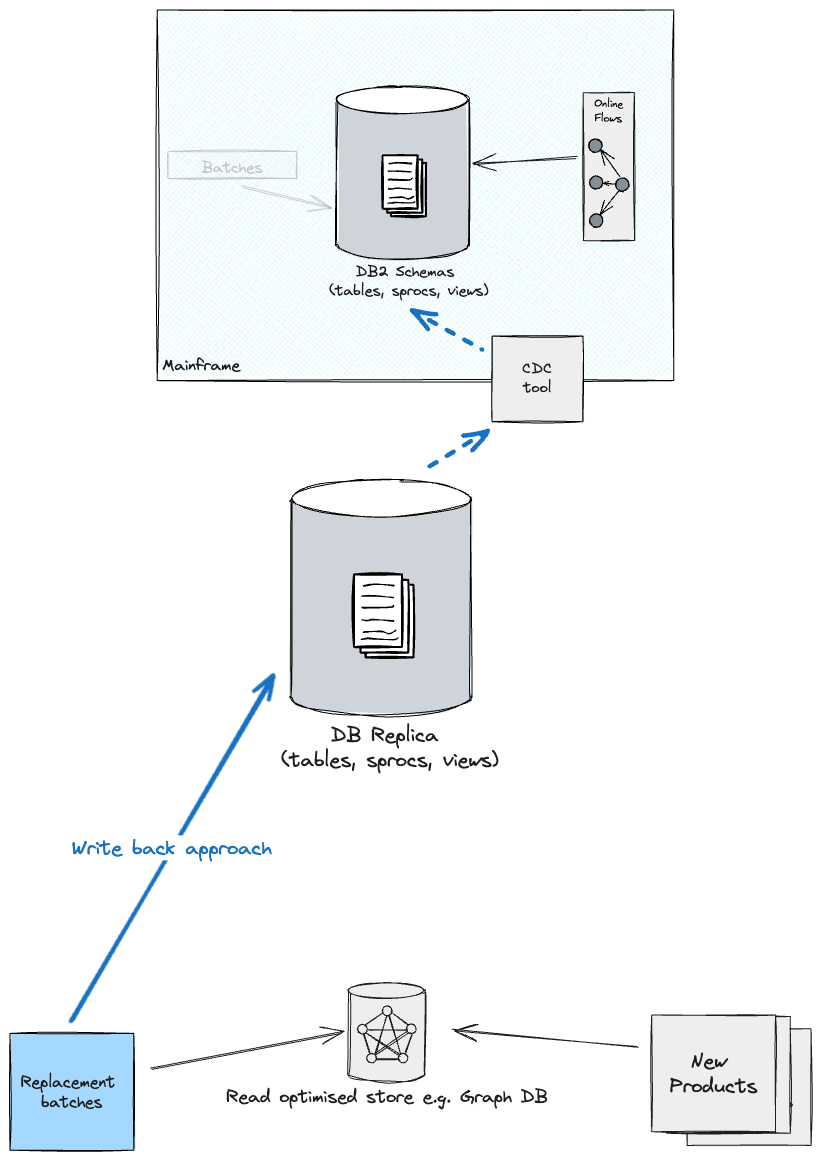
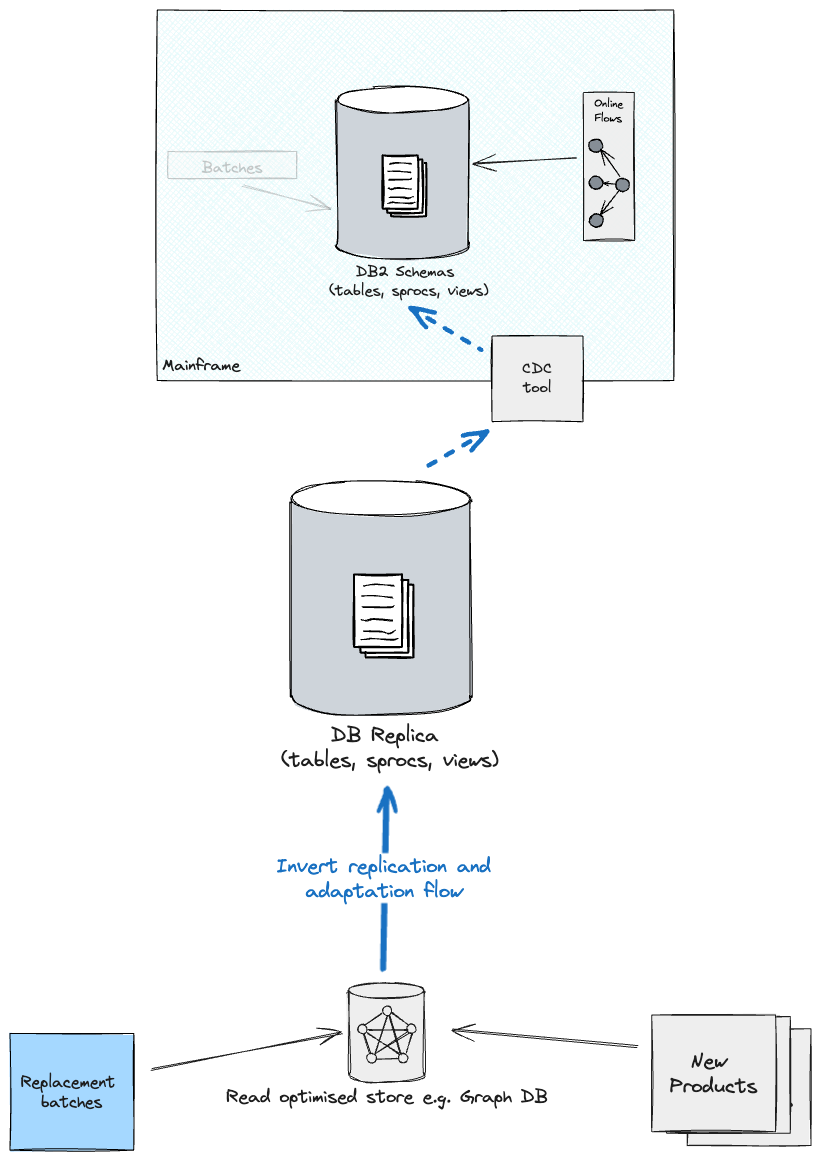
Upon
migration of batch workloads, so as to maintain all shops in sync, it’s possible you’ll
need to contemplate both a write again technique to the brand new Main straight
(what was beforehand often known as the Reproduction), which in flip feeds again DB2
on the Mainframe (although there shall be larger coupling from the batches to
the previous schema), or revert the CDC & Adaptation layer route from the
Optimised retailer as a supply and the brand new Main as a goal (you’ll
possible have to handle replication individually for every information section i.e.
one information section replicates from Reproduction to Optimised retailer, one other
section the opposite approach round).
Conclusion
There are a number of issues to contemplate when offloading from the
mainframe. Relying on the dimensions of the system that you just want to migrate
off the mainframe, this work can take a substantial period of time, and
Incremental Twin Run prices are non-negligible. How a lot this may value
is dependent upon varied components, however you can not count on to save lots of on prices through
twin operating two methods in parallel. Thus, the enterprise ought to have a look at
producing worth early to get buy-in from stakeholders, and fund a
multi-year modernisation programme. We see Incremental Twin Run as an
enabler for groups to reply quick to the demand of the enterprise, going
hand in hand with Agile and Steady Supply practices.
Firstly, you must perceive the general system panorama and what
the entry factors to your system are. These interfaces play a vital
function, permitting for the migration of exterior customers/functions to the brand new
system you’re constructing. You’re free to revamp your exterior contracts
all through this migration, however it should require an adaptation layer between
the Mainframe and Cloud.
Secondly, you must determine the enterprise capabilities the Mainframe
system provides, and determine the seams between the underlying packages
implementing them. Being capability-driven helps guarantee that you’re not
constructing one other tangled system, and retains duties and considerations
separate at their applicable layers. One can find your self constructing a
collection of Adapters that may both expose APIs, eat occasions, or
replicate information again to the Mainframe. This ensures that different methods
operating on the Mainframe can maintain functioning as is. It’s best apply
to construct these adapters as reusable parts, as you’ll be able to make use of them in
a number of areas of the system, based on the particular necessities you
have.
Thirdly, assuming the aptitude you are attempting emigrate is stateful, you’ll possible require a duplicate of the
information that the Mainframe has entry to. A CDC software to duplicate information might be employed right here. It is very important
perceive the CFRs (Cross Practical Necessities) for information replication, some information might have a quick replication
lane to the Cloud and your chosen software ought to present this, ideally. There are actually a number of instruments and frameworks
to contemplate and examine to your particular situation. There are a plethora of CDC instruments that may be assessed,
as an illustration we checked out Qlik Replicate for DB2 tables and Exactly Join extra particularly for VSAM shops.
Cloud Service Suppliers are additionally launching new choices on this space;
as an illustration, Twin Run by Google Cloud just lately launched its personal
proprietary information replication method.
For a extra holistic view on mobilising a group of groups to ship a
programme of labor of this scale, please seek advice from the article “Consuming the Elephant” by our colleague, Sophie
Holden.
Finally, there are different issues to contemplate which have been briefly
talked about as a part of this text. Amongst these, the testing technique
will play a task of paramount significance to make sure you are constructing the
new system proper. Automated testing shortens the suggestions loop for
supply groups constructing the goal system. Comparability testing ensures each
methods exhibit the identical behaviour from a technical perspective. These
methods, used together with Artificial information technology and
Manufacturing information obfuscation methods, give finer management over the
situations you propose to set off and validate their outcomes. Final however not
least, manufacturing comparability testing ensures the system operating in Twin
Run, over time, produces the identical final result because the legacy one by itself.
When wanted, outcomes are in contrast from an exterior observer’s level of
view at the least, equivalent to a buyer interacting with the system.
Moreover, we are able to examine middleman system outcomes.
Hopefully, this text brings to life what you would want to contemplate
when embarking on a Mainframe offloading journey. Our involvement was on the very first few months of a
multi-year programme and a number of the options we have now mentioned have been at a really early stage of inception.
However, we learnt an excellent deal from this work and we discover these concepts value sharing. Breaking down your
journey into viable precious steps will at all times require context, however we
hope our learnings and approaches may also help you getting began so you’ll be able to
take this the additional mile, into manufacturing, and allow your personal
roadmap.


