Two males have been arrested for allegedly stealing knowledge from and extorting dozens of firms that used the cloud knowledge storage firm Snowflake, however a 3rd suspect — a prolific hacker referred to as Kiberphant0m — stays at giant and continues to publicly extort victims. Nonetheless, this individual’s id might not stay a secret for lengthy: A cautious assessment of Kiberphant0m’s day by day chats throughout a number of cybercrime personas suggests they’re a U.S. Military soldier who’s or was just lately stationed in South Korea.
Kiberphant0m’s identities on cybercrime boards and on Telegram and Discord chat channels have been promoting knowledge stolen from clients of the cloud knowledge storage firm Snowflake. On the finish of 2023, malicious hackers found that many firms had uploaded large volumes of delicate buyer knowledge to Snowflake accounts that had been protected with nothing greater than a username and password (no multi-factor authentication required).
After scouring darknet markets for stolen Snowflake account credentials, the hackers started raiding the info storage repositories for a few of the world’s largest companies. Amongst these was AT&T, which disclosed in July that cybercriminals had stolen private info, cellphone and textual content message data for roughly 110 million individuals. Wired.com reported in July that AT&T paid a hacker $370,000 to delete stolen cellphone data.
On October 30, Canadian authorities arrested Alexander Moucka, a.ok.a. Connor Riley Moucka of Kitchener, Ontario, on a provisional arrest warrant from the US, which has since indicted him on 20 legal counts related to the Snowflake breaches. One other suspect within the Snowflake hacks, John Erin Binns, is an American who’s at present incarcerated in Turkey.

A surveillance photograph of Connor Riley Moucka, a.ok.a. “Judische” and “Waifu,” dated Oct 21, 2024, 9 days earlier than Moucka’s arrest. This picture was included in an affidavit filed by an investigator with the Royal Canadian Mounted Police (RCMP).
Investigators say Moucka, who glided by the handles Judische and Waifu, had tasked Kiberphant0m with promoting knowledge stolen from Snowflake clients who refused to pay a ransom to have their info deleted. Instantly after information broke of Moucka’s arrest, Kiberphant0m was clearly livid, and posted on the hacker neighborhood BreachForums what they claimed had been the AT&T name logs for President-elect Donald J. Trump and for Vice President Kamala Harris.
“Within the occasion you don’t attain out to us @ATNT all presidential authorities name logs can be leaked,” Kiberphant0m threatened, signing their submit with a number of “#FREEWAIFU” tags. “You don’t assume we don’t have plans within the occasion of an arrest? Assume once more.”
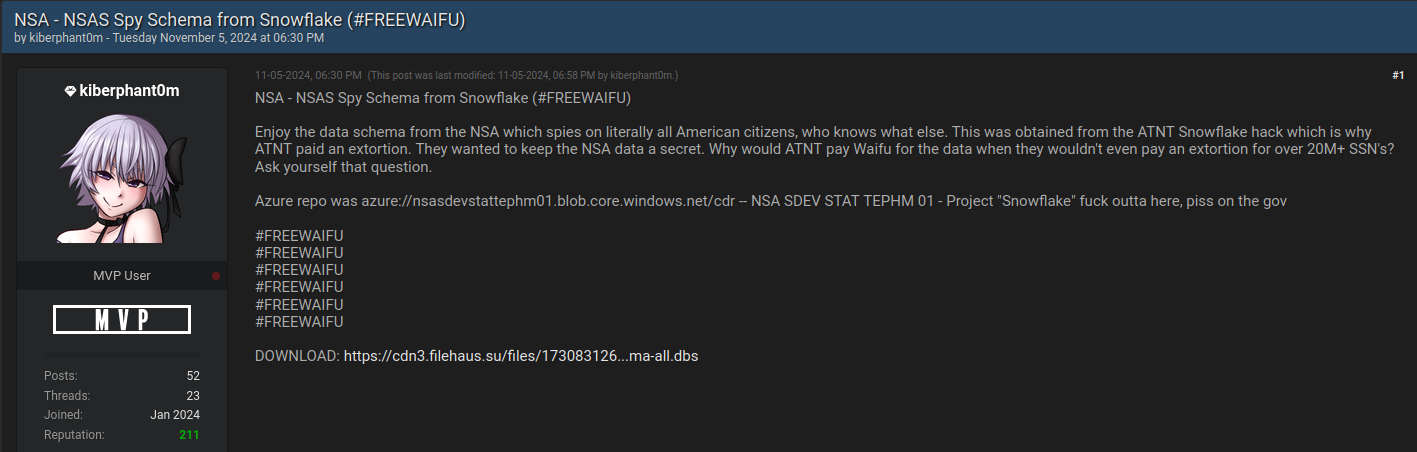
On the identical day, Kiberphant0m posted what they claimed was the “knowledge schema” from the U.S. Nationwide Safety Company.
“This was obtained from the ATNT Snowflake hack which is why ATNT paid an extortion,” Kiberphant0m wrote in a thread on BreachForums. “Why would ATNT pay Waifu for the info once they wouldn’t even pay an extortion for over 20M+ SSNs?”
Additionally on Nov. 5, Kiberphant0m provided name logs stolen from Verizon’s push-to-talk (PTT) clients — primarily U.S. authorities businesses and emergency first responders. On Nov. 9, Kiberphant0m posted a gross sales thread on BreachForums providing a “SIM-swapping” service focusing on Verizon PTT clients. In a SIM-swap, fraudsters use credentials which might be phished or stolen from cell phone firm staff to divert a goal’s cellphone calls and textual content messages to a tool they management.
MEET ‘BUTTHOLIO’
Kiberphant0m joined BreachForums in January 2024, however their public utterances on Discord and Telegram channels date again to at the least early 2022. On their first submit to BreachForums, Kiberphant0m stated they might be reached on the Telegram deal with @cyb3rph4nt0m.
A assessment of @cyb3rph4nt0m reveals this person has posted greater than 4,200 messages since January 2024. Many of those messages had been makes an attempt to recruit individuals who might be employed to deploy a bit of malware that enslaved host machines in an Web of Issues (IoT) botnet.
On BreachForums, Kiberphant0m has offered the supply code to “Shi-Bot,” a customized Linux DDoS botnet primarily based on the Mirai malware. Kiberphant0m had few gross sales threads on BreachForums previous to the Snowflake assaults changing into public in Might, and plenty of of these concerned databases stolen from firms in South Korea.
On June 5, 2024, a Telegram person by the title “Buttholio” joined the fraud-focused Telegram channel “Comgirl” and claimed to be Kiberphant0m. Buttholio made the declare after being taunted as a no one by one other denizen of Comgirl, referring to their @cyb3rph4nt0m account on Telegram and the Kiberphant0m person on cybercrime boards.
“Kind ‘kiberphant0m’ on google with the quotes,” Buttholio instructed one other person. “I’ll wait. Go forward. Over 50 articles. 15+ telecoms breached. I obtained the IMSI quantity to each single individual that’s ever registered in Verizon, Tmobile, ATNT and Verifone.”
On Sept. 17, 2023, Buttholio posted in a Discord chat room devoted to gamers of the online game Escape from Tarkov. “Come to Korea, servers there’s just about no extract camper or cheater,” Buttholio suggested.
In one other message that very same day within the gaming Discord, Buttholio instructed others they purchased the sport in the US, however that they had been enjoying it in Asia.
“USA is the place the sport was bought from, server location is precise in recreation servers u play on. I’m a u.s. soldier so i purchased it within the states however obtained on rotation so i’ve to make use of asian servers,” they shared.
‘REVERSESHELL’
The account @Kiberphant0m was assigned the Telegram ID quantity 6953392511. A assessment of this ID on the cyber intelligence platform Flashpoint reveals that on January 4, 2024 Kibertphant0m posted to the Telegram channel “Dstat,” which is populated by cybercriminals concerned in launching distributed denial-of-service (DDoS) assaults and promoting DDoS-for-hire companies [Full disclosure: Flashpoint is currently an advertiser on this website].
Instantly after Kiberphant0m logged on to the Dstat channel, one other person wrote “hello buttholio,” to which Kiberphant0m replied with an affirmative greeting “wsg,” or “what’s good.” On Nov. 1, Dstat’s web site dstat[.]cc was seized as a part of “Operation PowerOFF,” a world regulation enforcement motion towards DDoS companies.
Flashpoint’s knowledge reveals that @kiberphant0m instructed a fellow member of Dstat on April 10, 2024 that their alternate Telegram username was “@reverseshell,” and did the identical two weeks later within the Telegram chat The Jacuzzi. The Telegram ID for this account is 5408575119.
Means again on Nov. 15, 2022, @reverseshell instructed a fellow member of a Telegram channel known as Cecilio Chat that they had been a soldier within the U.S. Military. This person additionally shared the next picture of somebody pictured waist-down in navy fatigues, with a camouflaged backpack at their ft:

Kiberphant0m’s obvious alias ReverseShell posted this picture on a Telegram channel Cecilio Chat, on Nov. 15, 2022. Picture: Flashpoint.
In September 2022, Reverseshell was embroiled in an argument with one other member who had threatened to launch a DDoS assault towards Reverseshell’s Web handle. After the promised assault materialized, Reverseshell responded, “Yall simply hit navy base contracted wifi.”
In a chat from October 2022, Reverseshell was bragging concerning the pace of the servers they had been utilizing, and in reply to a different member’s query stated that they had been accessing the Web by way of South Korea Telecom.
Telegram chat logs archived by Flashpoint present that on Aug. 23, 2022, Reverseshell bragged they’d been utilizing automated instruments to seek out legitimate logins for Web servers that they resold to others.
“I’ve hit US gov servers with default creds,” Reverseshell wrote, referring to programs with easy-to-guess usernames and/or passwords. “Telecom management servers, equipment outlets, Russian ISP servers, and many others. I offered a number of large firms for like $2-3k a bit. You may promote the entry once you get an enormous SSH into company.”
On July 29, 2023, Reverseshell posted a screenshot of a login web page for a significant U.S. protection contractor, claiming that they had an aerospace firm’s credentials to promote.
PROMAN AND VARS_SECC
Flashpoint finds the Telegram ID 5408575119 has used a number of aliases since 2022, together with Reverseshell and Proman557.
A search on the username Proman557 on the cyber intelligence platform Intel 471 reveals {that a} hacker by the title “Proman554” registered on Hackforums in September 2022, and in messages to different customers Proman554 stated they are often reached on the Telegram account Buttholio.
Intel 471 additionally finds the Proman557 moniker is one among many utilized by an individual on the Russian-language hacking discussion board Exploit in 2022 who offered a wide range of Linux-based botnet malware.
Proman557 was finally banned — allegedly for scamming a fellow member out of $350 — and the Exploit moderator warned discussion board customers that Proman557 had beforehand registered underneath a number of different nicknames, together with an account known as “Vars_Secc.”
Vars_Secc’s 1000’s of feedback on Telegram over two years present this person divided their time between on-line gaming, sustaining a DDoS botnet, and selling the sale or renting of their botnets to different customers.
“I take advantage of ddos for a lot of issues not simply to be a skid,” Vars_Secc pronounced. “Why do you assume I haven’t offered my web?” They then proceeded to checklist probably the most helpful qualities of their botnet:
-I take advantage of it to hit off servers that ban me or piss me off
-I used to ddos sure video games to get my gadgets again because the knowledge reverts to when u joined
-I take advantage of it for server aspect desync RCE vulnerabilities
-I take advantage of it to generally ransom
-I take advantage of it when bored as a supply of leisure
Flashpoint reveals that in June 2023, Vars_Secc responded to taunting from a fellow member within the Telegram channel SecHub who had threatened to disclose their private particulars to the federal authorities for a reward.
“Man I’ve been doing this shit for 4 years,” Vars_Secc replied nonchalantly. “I extremely doubt the federal government goes to pay tens of millions of {dollars} for knowledge on some random dude working a pointless ddos botnet and discovering a number of vulnerabilities right here and there.”
For a number of months in 2023, Vars_Secc additionally was an lively member of the Russian-language crime discussion board XSS, the place they offered entry to a U.S. authorities server for $2,000. Nonetheless, Vars_Secc can be banned from XSS after trying to promote entry to the Russian telecommunications big Rostelecom. [In this, Vars_Secc violated the Number One Rule for operating on a Russia-based crime forum: Never offer to hack or sell data stolen from Russian entities or citizens].
On June 20, 2023, Vars_Secc posted a gross sales thread on the cybercrime discussion board Ramp 2.0 titled, “Promoting US Gov Monetary Entry.”
“Server inside the community, doable to pivot,” Vars_Secc’s sparse gross sales submit learn. “Has 3-5 subroutes related to it. Worth $1,250. Telegram: Vars_Secc.”
Vars_Secc additionally used Ramp in June 2023 to promote entry to a “Vietnam authorities Web Community Data Heart.”
“Promoting entry server allotted inside the community,” Vars_Secc wrote. “Has some knowledge on it. $500.”
BUG BOUNTIES
The Vars_Secc id claimed on Telegram in Might 2023 that they made cash by submitting reviews about software program flaws to HackerOne, an organization that helps expertise companies discipline reviews about safety vulnerabilities of their services and products. Particularly, Vars_Secc stated that they had earned monetary rewards or “bug bounties” from reddit.com, the U.S. Division of Protection, and Coinbase, amongst 30 others.
“I make cash off bug bounties, it’s fairly easy,” Vars_Secc stated when requested what they do for a dwelling. “That’s why I’ve over 30 bug bounty reviews on HackerOne.”
A month earlier than that, Vars_Secc stated they’d discovered a vulnerability in reddit.com.
“I poisoned Reddit’s cache,” they defined. “I’m going to use it additional, then report it to reddit.”
KrebsOnSecurity sought remark from HackerOne, which stated it might examine the claims. This story can be up to date in the event that they reply.
The Vars_Secc telegram deal with additionally has claimed possession of the BreachForums member “Boxfan,” and Intel 471 reveals Boxfan’s early posts on the discussion board had the Vars_Secc Telegram account of their signature. Of their most up-to-date submit to BreachForums in January 2024, Boxfan disclosed a safety vulnerability they present in Naver, the most well-liked search engine in South Korea (in response to statista.com). Boxfan’s feedback recommend they’ve robust damaging emotions about South Korean tradition.
“Have enjoyable exploiting this vulnerability,” Boxfan wrote on BreachForums, after pasting an extended string of laptop code meant to exhibit the flaw. “Fuck you South Korea and your discriminatory views. No person likes ur shit kpop you evil fucks. Whoever can dump this DB [database] congrats. I don’t really feel like doing it so I’ll submit it to the discussion board.”
The numerous identities tied to Kiberphant0m strongly recommend they’re or till just lately had been a U.S. Military soldier stationed in South Korea. Kiberphant0m’s alter egos by no means talked about their navy rank, regiment, or specialization.
Nonetheless, it’s possible that Kiberphant0m’s facility with computer systems and networking was observed by the Military. In keeping with the U.S. Military’s web site, the majority of its forces in South Korea reside inside the Eighth Military, which has a devoted cyber operations unit centered on defending towards cyber threats.
On April 1, 2023, Vars_Secc posted to a public Telegram chat channel a screenshot of the Nationwide Safety Company’s web site. The picture indicated the customer had simply utilized for some kind of job on the NSA.

A screenshot posted by Vars_Secc on Telegram on April 1, 2023, suggesting they only utilized for a job on the Nationwide Safety Company.
The NSA has not but responded to requests for remark.
Reached by way of Telegram, Kiberphant0m acknowledged that KrebsOnSecurity managed to unearth their outdated handles.
“I see you discovered the IP behind it no method,” Kiberphant0m replied. “I see you managed to seek out my outdated aliases LOL.”
Kiberphant0m denied being within the U.S. Military or ever being in South Korea, and stated all of that was a prolonged ruse designed to create a fictitious persona. “Epic opsec troll,” they claimed.
Requested in the event that they had been in any respect involved about getting busted, Kiberphant0m known as that an impossibility.
“I actually can’t get caught,” Kiberphant0m stated, declining an invite to elucidate why. “I don’t even stay within the USA Mr. Krebs.”
Under is a thoughts map that hopefully helps illustrate a few of the connections between and amongst Kiberphant0m’s obvious alter egos.
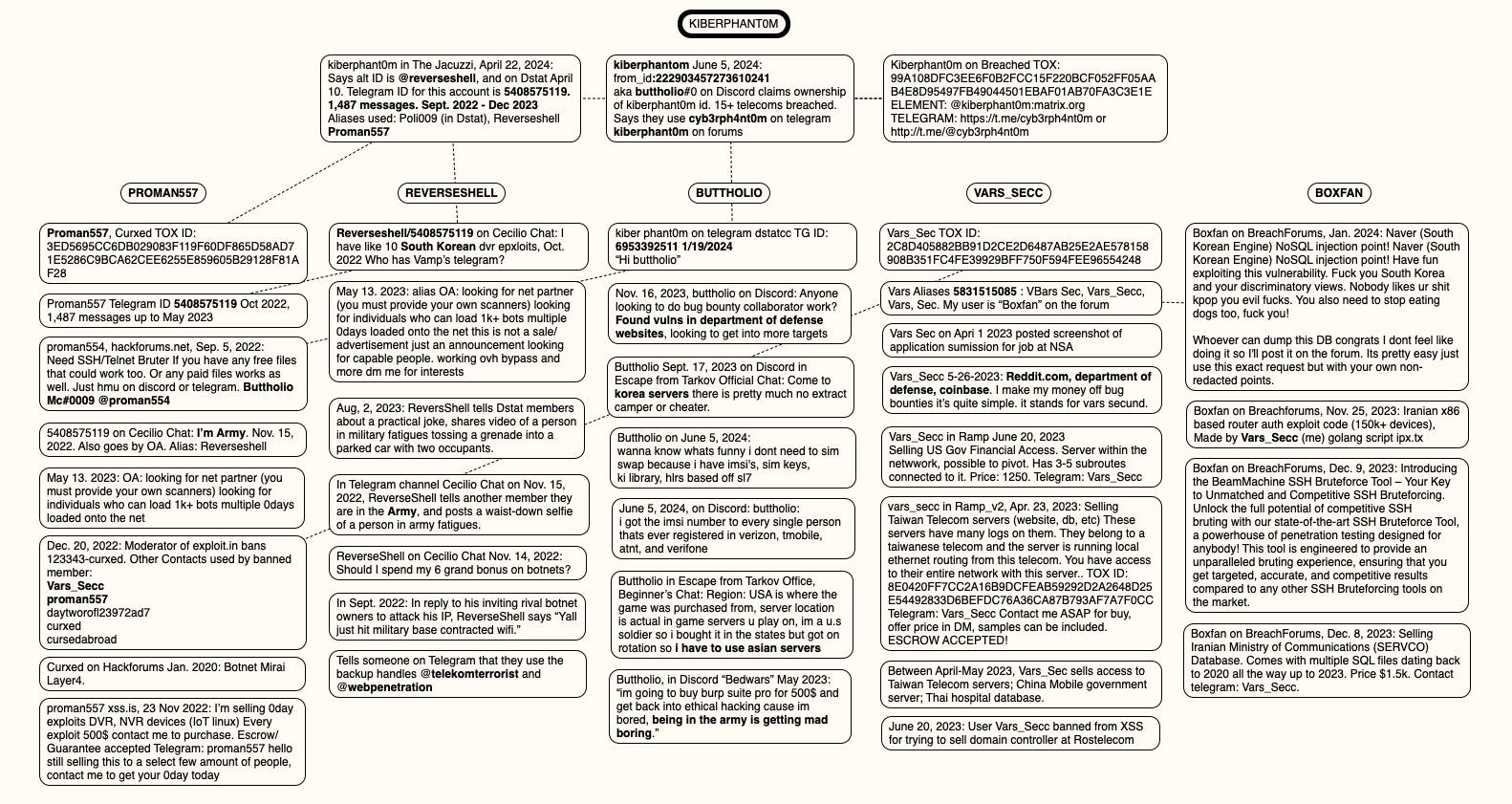
A thoughts map of the connections between and among the many identities apparently utilized by Kiberphant0m. Click on to enlarge.
KrebsOnSecurity wish to prolong a particular observe of due to the New York Metropolis primarily based safety intelligence agency Unit 221B for his or her help in serving to to piece collectively key components of Kiberphant0m’s totally different identities.