
Hackers delivered malware to Home windows and Mac customers by compromising their Web service supplier after which tampering with software program updates delivered over unsecure connections, researchers stated.
The assault, researchers from safety agency Volexity stated, labored by hacking routers or related forms of machine infrastructure of an unnamed ISP. The attackers then used their management of the gadgets to poison area title system responses for reliable hostnames offering updates for at the very least six totally different apps written for Home windows or macOS. The apps affected have been the 5KPlayer, Fast Heal, Rainmeter, Partition Wizard, and people from Corel and Sogou.
These aren’t the replace servers you’re on the lookout for
As a result of the replace mechanisms didn’t use TLS or cryptographic signatures to authenticate the connections or downloaded software program, the menace actors have been ready to make use of their management of the ISP infrastructure to efficiently carry out machine-in-the-middle (MitM) assaults that directed focused customers to hostile servers relatively than those operated by the affected software program makers. These redirections labored even when customers employed non-encrypted public DNS providers equivalent to Google’s 8.8.8.8 or Cloudflare’s 1.1.1.1 relatively than the authoritative DNS server offered by the ISP.
“That’s the enjoyable/scary half—this was not the hack of the ISPs DNS servers,” Volexity CEO Steven Adair wrote in a web-based interview. “This was a compromise of community infrastructure for Web visitors. The DNS queries, for instance, would go to Google’s DNS servers destined for 8.8.8.8. The visitors was being intercepted to reply to the DNS queries with the IP tackle of the attacker’s servers.”
In different phrases, the DNS responses returned by any DNS server could be modified as soon as it reached the infrastructure of the hacked ISP. The one means an finish person might have thwarted the assault was to make use of DNS over HTTPS or DNS over TLS to make sure lookup outcomes haven’t been tampered with or to keep away from all use of apps that ship unsigned updates over unencrypted connections.
Volexity offered the next diagram illustrating the circulation of the assault:
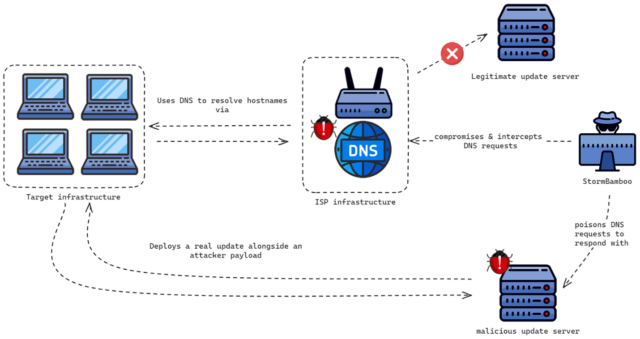
Volexity
For example, the 5KPlayer app makes use of an unsecure HTTP connection relatively than an encrypted HTTPS one to verify if an replace is offered and, if that’s the case, to obtain a configuration file named Youtube.config. StormBamboo, the title used within the trade to trace the hacking group accountable, used DNS poisoning to ship a malicious model of the Youtube.config file from a malicious server. This file, in flip, downloaded a next-stage payload that was disguised as a PNG picture. In truth, it was an executable file that put in malware tracked beneath the names MACMA for macOS gadgets or POCOSTICK for Home windows gadgets.
MACMA first got here to gentle in 2021 put up printed by Google’s Menace Evaluation Group, a crew that tracks malware and cyberattacks backed by nation-states. The backdoor was written for macOS and iOS gadgets and offered a full suite of capabilities together with machine fingerprinting, display screen seize, file downloading and importing, execution of terminal instructions, audio recording, and keylogging.
POCOSTICK, in the meantime, has been in use since at the very least 2014. Final yr, safety agency ESET stated the malware, which it tracked beneath the title MGBot, was used solely by a Chinese language-speaking menace group tracked as Evasive Panda.
ESET researchers decided that the malware was put in by way of reliable updates of benign software program, however they weren’t certain how that occurred. One risk, the researchers stated on the time, was by way of a supply-chain assault that changed the reliable updates with malicious ones on the very supply. The opposite potential situation was by way of a MitM assault on the servers delivering the updates. Volexity’s findings now affirm that the latter clarification is the right one.
In at the very least one case in the newest assaults, StormBamboo pressured a macOS machine to put in a browser plugin Volexity tracks beneath the title RELOADEXT. The extension masquerades as one which hundreds webpages to be suitable with Web Explorer. In truth, Volexity stated, it copies browser cookies and sends them to a Google Drive account managed by the attackers. The info was base64 encoded and encrypted utilizing the Superior Encryption Commonplace. Regardless of the care taken by the hackers, they nonetheless uncovered the client_id, client_secret, and refresh_token within the malicious extension.
One different method Volexity noticed was StormBamboo’s use of DNS poisoning to hijack www.msftconnecttest.com , a site Microsoft makes use of to find out if Home windows gadgets are actively linked to the Web. By changing the reliable DNS decision with an IP tackle pointing to a malicious web site operated by the menace actors, they may intercept HTTP requests destined for any host.
Adair declined to determine the hacked ISP aside from to say it’s “not an enormous big one or one you’d possible know.”
“In our case the incident is contained however we see different servers which might be actively serving malicious updates however we have no idea the place they’re being served from,” he stated. “We suspect there are different energetic assaults all over the world we would not have purview into. This might be from an ISP compromise or a localized compromise to a company equivalent to on their firewall.”
As famous earlier, there are various choices for stopping these kinds of assaults past (1) eschewing all software program that updates unsecurely or (2) utilizing DNS over HTTPS or DNS over TLS. The primary methodology is probably going the very best, though it possible means having to cease utilizing a most well-liked app in at the very least some circumstances. The choice DNS configurations are viable, however in the meanwhile are provided by solely a handful of DNS suppliers, with 8.8.8.8 and 1.1.1.1 being the very best identified.


