
Microsoft has found a brand new distant entry trojan (RAT) that employs “refined strategies” to keep away from detection, keep persistence, and extract delicate information.
Whereas the malware (dubbed StilachiRAT) hasn’t but reached widespread distribution, Microsoft says it determined to publicly share indicators of compromise and mitigation steerage to assist community defenders detect this menace and cut back its influence.
Because of the restricted situations of StilachiRAT being deployed within the wild, Microsoft has but to attribute this malware to a selected menace actor or affiliate it with a specific geolocation.
“In November 2024, Microsoft Incident Response researchers uncovered a novel distant entry trojan (RAT) we named StilachiRAT that demonstrates refined strategies to evade detection, persist within the goal atmosphere, and exfiltrate delicate information,” Microsoft mentioned.
“Evaluation of the StilachiRAT’s WWStartupCtrl64.dll module that accommodates the RAT capabilities revealed using numerous strategies to steal info from the goal system, reminiscent of credentials saved within the browser, digital pockets info, information saved within the clipboard, in addition to system info.
Amongst this new RAT’s options, Redmond highlighted reconnaissance capabilities like gathering system information, together with {hardware} identifiers, digital camera presence, lively Distant Desktop Protocol (RDP) periods, and working GUI-based purposes to profile focused programs.
After being deployed on compromised programs, attackers can use StilachiRAT to siphon digital pockets information by scanning the configuration info of 20 cryptocurrency pockets extensions, together with Coinbase Pockets, Phantom, Belief Pockets, Metamask, OKX Pockets, Bitget Pockets, and others.
The malware additionally extracts credentials saved within the Google Chrome native state file with the assistance of Home windows APIs and screens clipboard exercise for delicate info like passwords and cryptocurrency keys whereas monitoring lively home windows and purposes.
As soon as launched as a standalone course of or a Home windows service, the RAT beneficial properties and maintains persistence by way of the Home windows service management supervisor (SCM) and ensures it will get reinstalled routinely utilizing watchdog threads that monitor the malware’s binaries and recreate them in the event that they’re now not lively.
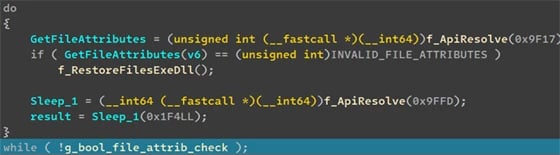
StilachiRAT can even monitor lively RDP periods by capturing info from foreground home windows and cloning safety tokens to impersonate logged-in customers, which may let the attackers transfer laterally inside a sufferer’s networks after deploying the RAT malware on RDP servers that always host administrative periods.
“The malware obtains the present session and actively launches foreground home windows in addition to enumerates all different RDP periods,” Microsoft mentioned. “For every recognized session, it’s going to entry the Home windows Explorer shell and duplicate its privileges or safety token. The malware then beneficial properties capabilities to launch purposes with these newly obtained privileges.”
The RAT’s capabilities additionally embrace in depth detection evasion and anti-forensics options, like the power to clear occasion logs and test for indicators that it is working in a sandbox to dam malware evaluation makes an attempt. Even when tricked into working in a sandbox, StilachiRAT’s Home windows API calls are encoded as “checksums which are resolved dynamically at runtime” and additional obfuscated to decelerate evaluation.
Final however not least, Microsoft says StilachiRAT permits command execution and potential SOCKS-like proxying utilizing instructions from a command-and-control (C2) server to the contaminated units, which may let the menace actors reboot the compromised system, clear logs, steal credentials, execute purposes, and manipulate system home windows.
Different instructions are designed to “droop the system, modify Home windows registry values, and enumerate open home windows.”
To scale back the assault floor this malware can use to compromise a focused system, Microsoft advises downloading software program solely from official web sites and utilizing safety software program that may block malicious domains and electronic mail attachments.



