Cyber protection safeguards info methods, networks, and knowledge from cyber threats by means of proactive safety measures. It includes deploying methods and applied sciences to guard towards evolving threats that will trigger hurt to enterprise continuity and popularity. These methods embrace threat evaluation and administration, menace detection and incident response planning, and catastrophe restoration.
Risk Intelligence (TI) performs a vital function in cyber protection by offering beneficial insights from analyzing indicators of compromise (IoCs) comparable to domains, IP addresses, and file hash values associated to potential and lively safety threats. These IoCs allow organizations to determine menace actors’ ways, strategies, and procedures, enhancing their means to defend towards potential assault vectors.
Advantages of menace intelligence
Risk intelligence helps safety groups flip uncooked knowledge into actionable insights, offering a deeper understanding of cyberattacks and enabling them to remain forward of latest threats. Some advantages of using menace intelligence in a corporation embrace:
- Simpler safety: Risk Intelligence helps organizations prioritize safety by understanding probably the most prevalent threats and their impression on their IT environments. This permits for efficient useful resource allocation of personnel, know-how, and funds.
- Improved safety posture: By understanding the evolving menace panorama, organizations can determine and deal with vulnerabilities of their methods earlier than attackers can exploit them. This strategy ensures steady monitoring of present threats whereas anticipating and making ready for future threats.
- Enhanced incident response: Risk intelligence offers beneficial context about potential threats, permitting safety groups to reply sooner and extra successfully. This helps organizations decrease downtime and doable injury to their digital belongings.
- Value effectivity: Organizations can get monetary savings by stopping cyberattacks and knowledge breaches by means of menace intelligence. An information breach can lead to vital prices, comparable to repairing system injury, diminished productiveness, and fines resulting from regulatory violations.
Wazuh integration with menace intelligence options
Wazuh is a free, open supply safety answer that provides unified SIEM and XDR safety throughout a number of platforms. It offers capabilities like menace detection and response, file integrity monitoring, vulnerability detection, safety configuration evaluation, and others. These capabilities assist safety groups swiftly detect and reply to threats of their info methods.
Wazuh offers out-of-the-box assist for menace intelligence sources like VirusTotal, YARA, Maltiverse, AbuseIPDB, and CDB lists to determine recognized malicious IP addresses, domains, URLs, and file hashes. By mapping safety occasions to the MITRE ATT&CK framework, Wazuh helps safety groups perceive how threats align with frequent assault strategies and prioritize and reply to them successfully. Moreover, customers can carry out customized integrations with different platforms, permitting for a extra tailor-made strategy to their menace intelligence program.
The part beneath exhibits examples of Wazuh integrations with third-party menace intelligence options.
MITRE ATT&CK integration
The MITRE ATT&CK framework, an out-of-the-box integration with Wazuh, is a continually up to date database that categorizes cybercriminals’ ways, strategies, and procedures (TTPs) all through an assault lifecycle. Wazuh maps ways and strategies with guidelines to prioritize and detect cyber threats. Customers can create customized guidelines and map them to the suitable MITRE ATT&CK ways and strategies. When occasions involving these TTPs happen on monitored endpoints, alerts are triggered on the Wazuh dashboard, enabling safety groups to reply swiftly and effectively.
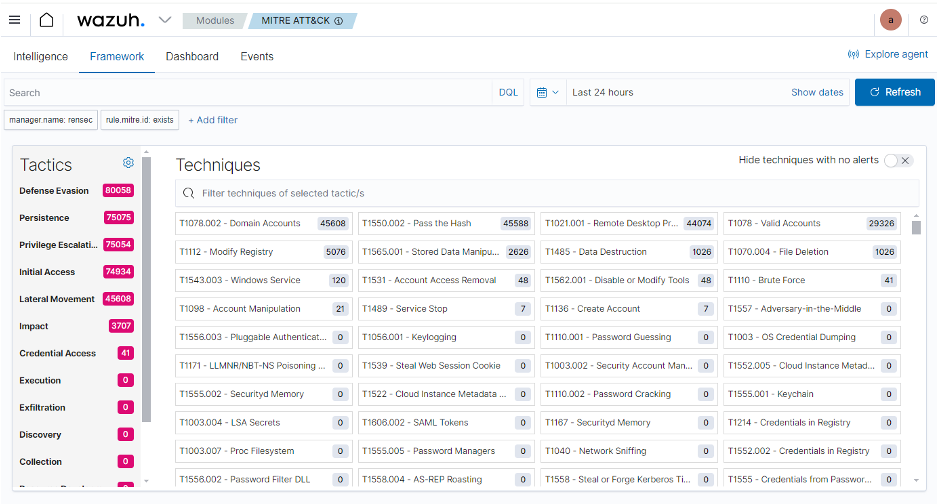
Determine 1: MITRE ATT&CK ways and strategies on the Wazuh dashboard
The out-of-the-box rule beneath detects when there may be an try and log in to a server utilizing SSH with a non-existent consumer.
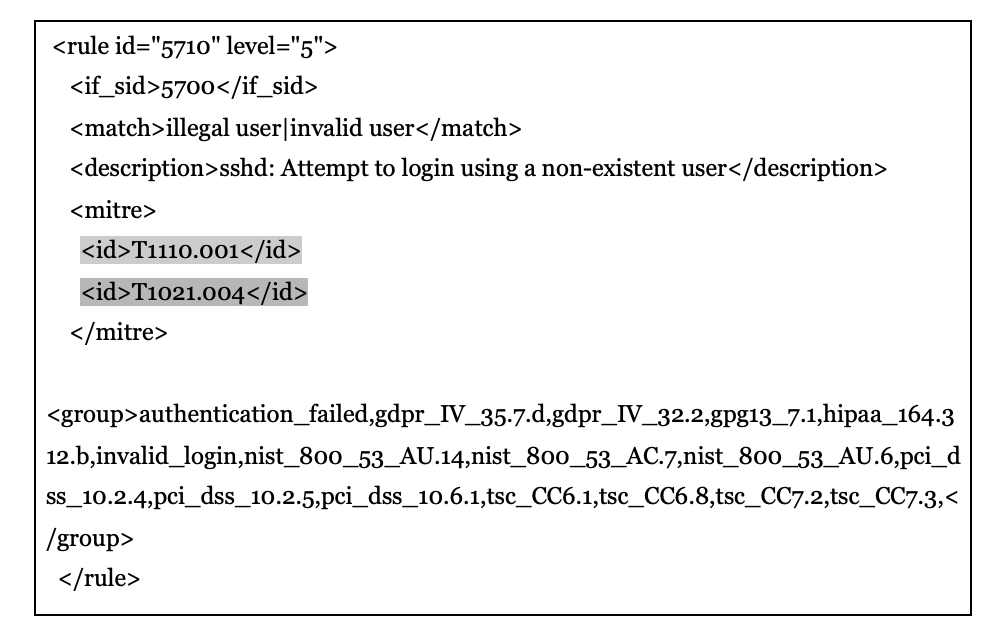
The place:
- T1110.001 refers back to the MITRE ATT&CK ways of brute forcing or password guessing.
- T1021.004 refers back to the MITRE ATT&CK ways of lateral motion utilizing distant companies like SSH
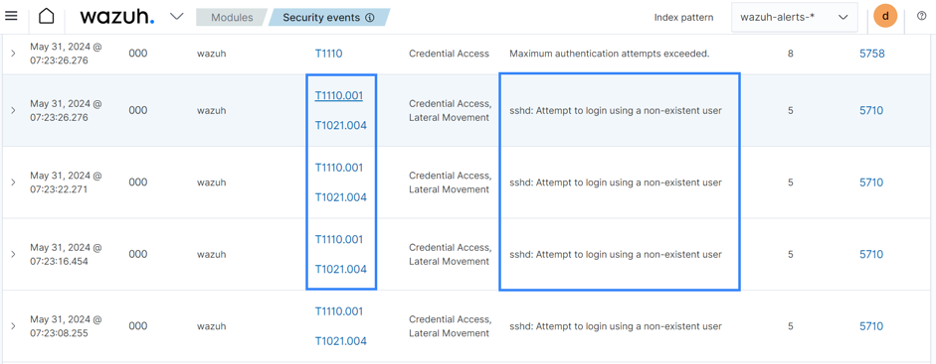
Determine 2: Alerts on the Wazuh dashboard exhibiting MITRE ATT&CK strategies and ways
YARA integration
YARA is an open supply instrument for sample matching and figuring out malware signatures. Wazuh integrates with YARA to boost menace detection by figuring out patterns and signatures related to malicious information. YARA makes use of the Wazuh FIM module to scan monitored endpoints for malicious information.
The effectiveness of the YARA integration is demonstrated in how Wazuh responds to Kuiper ransomware on an contaminated Home windows endpoint.
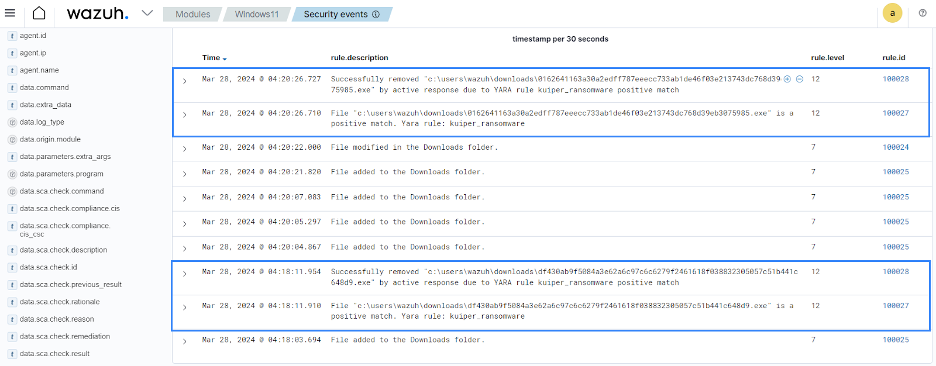
Determine 3: Kuiper ransomware detection utilizing Wazuh and YARA integration.
VirusTotal integration
VirusTotal is a safety platform for aggregating malware signatures and different menace intelligence artifacts. Wazuh integrates with the VirusTotal API to determine recognized indicators of compromise, enhancing the pace and accuracy of menace detection.
For instance, the Wazuh proof of idea information exhibits the best way to detect and take away malware utilizing VirusTotal integration.
The beneath block within the Wazuh configuration file /var/ossec/and so on/ossec.conf detects modifications to information and queries their hashes towards the VirusTotal API.
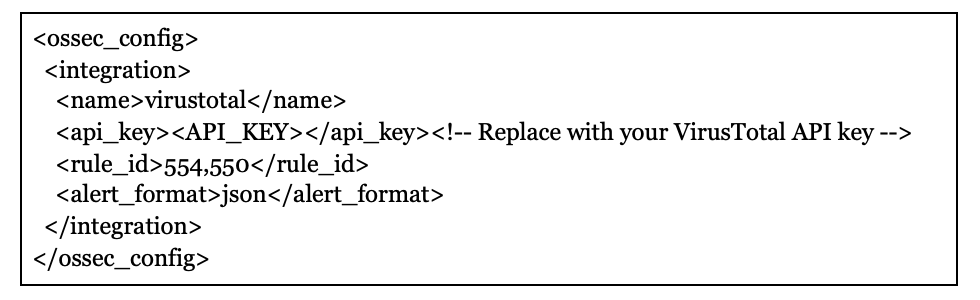
Additionally, the Wazuh command monitoring configuration within the Wazuh server configuration file /var/ossec/and so on/ossec.conf triggers the remove-threat.sh executable to take away the malicious file from the monitored endpoint when there’s a constructive VirusTotal match.

The determine beneath exhibits the detection and response alerts on the Wazuh dashboard.
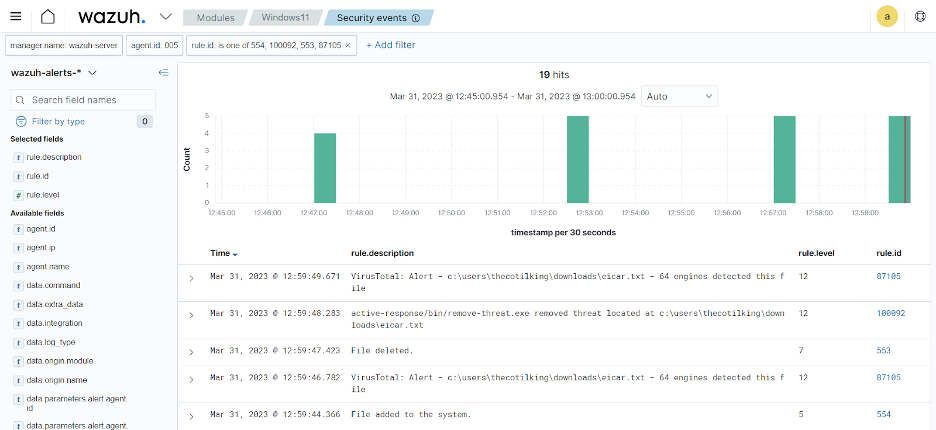
Determine 3: VirusTotal alert on the Wazuh dashboard
Conclusion
Wazuh is a free and open supply SIEM and XDR platform with many out-of-the-box capabilities that present safety throughout workloads in cloud and on-premises environments. Integrating Wazuh with menace intelligence feeds and platforms comparable to YARA, VirusTotal, and Maltiverse enhances its menace detection and response capabilities.
Be taught extra about Wazuh by exploring our documentation and becoming a member of our skilled neighborhood.


