
Replace 3/9/25: After receiving considerations about using the time period ‘backdoor’ to refer to those undocumented instructions, now we have up to date our title and story. Our authentic story will be discovered right here.
The ever present ESP32 microchip made by Chinese language producer Espressif and utilized by over 1 billion models as of 2023 accommodates undocumented instructions that could possibly be leveraged for assaults.
The undocumented instructions enable spoofing of trusted units, unauthorized information entry, pivoting to different units on the community, and doubtlessly establishing long-term persistence.
This was found by Spanish researchers Miguel Tarascó Acuña and Antonio Vázquez Blanco of Tarlogic Safety, who offered their findings yesterday at RootedCON in Madrid.
“Tarlogic Safety has detected a backdoor within the ESP32, a microcontroller that permits WiFi and Bluetooth connection and is current in tens of millions of mass-market IoT units,” reads a Tarlogic announcement shared with BleepingComputer.
“Exploitation of this backdoor would enable hostile actors to conduct impersonation assaults and completely infect delicate units similar to cell phones, computer systems, good locks or medical gear by bypassing code audit controls.”
The researchers warned that ESP32 is without doubt one of the world’s most generally used chips for Wi-Fi + Bluetooth connectivity in IoT (Web of Issues) units, so the chance is important.
Supply: Tarlogic
Discovering undocumented instructions in ESP32
Of their RootedCON presentation, the Tarlogic researchers defined that curiosity in Bluetooth safety analysis has waned however not as a result of the protocol or its implementation has turn into safer.
As an alternative, most assaults offered final yr did not have working instruments, did not work with generic {hardware}, and used outdated/unmaintained instruments largely incompatible with fashionable techniques.
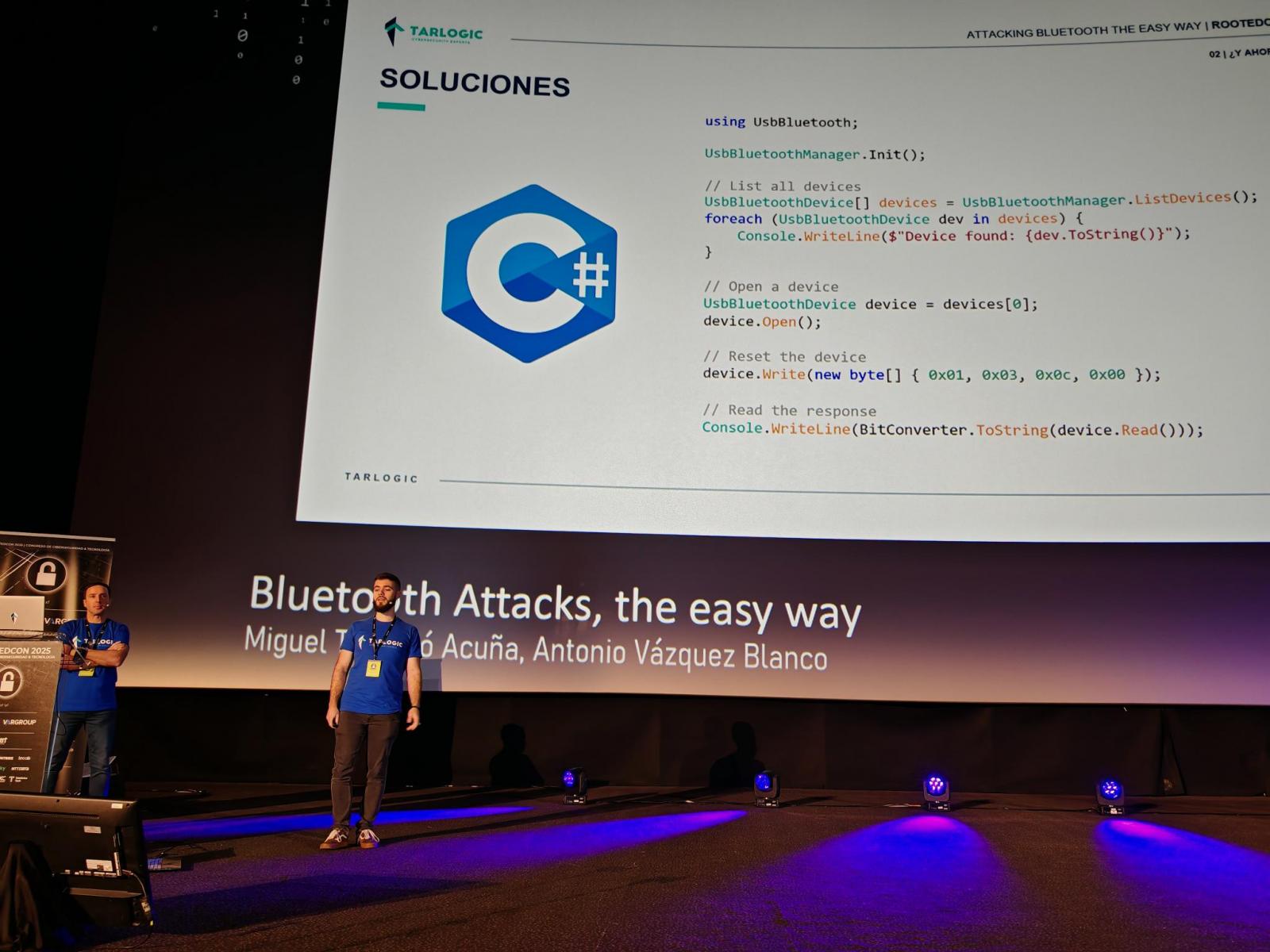
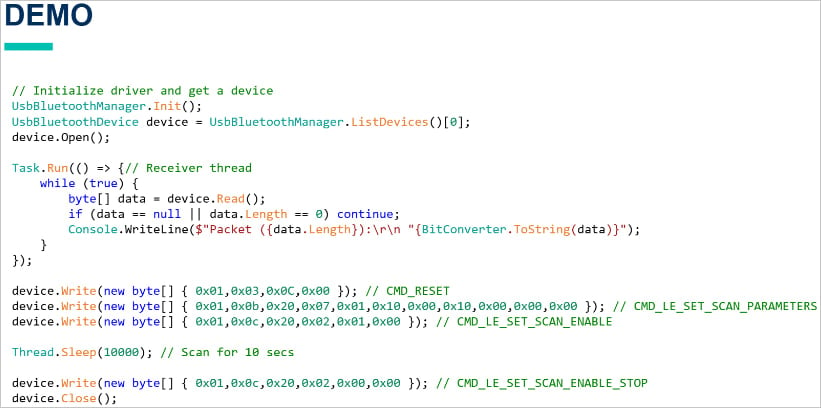
Tarlogic developed a brand new C-based USB Bluetooth driver that’s hardware-independent and cross-platform, permitting direct entry to the {hardware} with out counting on OS-specific APIs.
Armed with this new instrument, which permits uncooked entry to Bluetooth site visitors, Tarlogic found hidden vendor-specific instructions (Opcode 0x3F) within the ESP32 Bluetooth firmware that enable low-level management over Bluetooth features.
Supply: Tarlogic
In complete, they discovered 29 undocumented instructions, collectively characterised as a “backdoor,” that could possibly be used for reminiscence manipulation (learn/write RAM and Flash), MAC deal with spoofing (machine impersonation), and LMP/LLCP packet injection.
Espressif has not publicly documented these instructions, so both they weren’t meant to be accessible, or they had been left in by mistake. The difficulty is now tracked below CVE-2025-27840.
Supply: Tarlogic
The dangers arising from these instructions embrace malicious implementations on the OEM stage and provide chain assaults.
Relying on how Bluetooth stacks deal with HCI instructions on the machine, distant exploitation of the instructions could be doable by way of malicious firmware or rogue Bluetooth connections.
That is particularly the case if an attacker already has root entry, planted malware, or pushed a malicious replace on the machine that opens up low-level entry.
On the whole, although, bodily entry to the machine’s USB or UART interface can be far riskier and a extra practical assault situation.
“In a context the place you possibly can compromise an IOT machine with as ESP32 it is possible for you to to cover an APT contained in the ESP reminiscence and carry out Bluetooth (or Wi-Fi) assaults towards different units, whereas controlling the machine over Wi-Fi/Bluetooth,” defined the researchers to BleepingComputer.
“Our findings would enable to completely take management over the ESP32 chips and to achieve persistence within the chip by way of instructions that enable for RAM and Flash modification.”
“Additionally, with persistence within the chip, it could be doable to unfold to different units as a result of the ESP32 permits for the execution of superior Bluetooth assaults.”
BleepingComputer has contacted Espressif for a press release on the researchers’ findings, however a remark wasn’t instantly obtainable.
Replace 3/8/25: Added assertion from Tarlogic.
Replace 3/9/25: Added CVE-ID


