As expertise advances, guaranteeing the safety of laptop methods, networks, and purposes turns into more and more vital. One of many methods through which safety professionals can assess the safety posture of a whole digital ecosystem is by finishing up penetration testing, or pen testing for brief.
Penetration testing is the licensed simulation of a real-world cyber-attack. This enables organizations to guage how robust their safety methods are and determine what weaknesses or vulnerabilities are current, if any.
In response to analysis by SNS Insider, the penetration testing market is predicted to achieve $6.98 billion in worth by 2032, largely as a result of continued development of cybersecurity threats. As a elementary apply for assessing a company’s safety posture, pentests contain each the experience of skilled safety professionals and using highly effective penetration testing instruments.
Given the proliferation of those instruments, I’ve give you a listing of the highest penetration testing instruments out there with their options, advantages, and disadvantages.
Penetration testing software program comparability desk
Here’s a characteristic comparability of our shortlisted pen testing instruments and the way they stack up in opposition to one another.
| Compliance checks | Variety of assessments lined | Open-source / web-based | Reporting and documentation | Beginning value | |
|---|---|---|---|---|---|
| Astra | Sure | 8,000+ | Internet | Sure | $1,999 per 12 months, one goal |
| Acunetix | No | 7,000+ | Internet | Sure | Contact for quote. |
| Intruder | Sure | Not specified | Internet | Sure | $157 monthly, one utility |
| Metasploit | Sure | 1,500+ | Each | No | Contact for quote. |
| Core Impression | Sure | Not specified | Internet | Sure | $9,450 per consumer, consumer per 12 months. |
| Kali Linux | Sure | Not specified | Open-source | Sure | Fully free |
| Wire Shark | No | Not specified | Open-source | Sure | Fully free |
| SQL Map | No | Not specified | Open-source | Sure | Fully free |
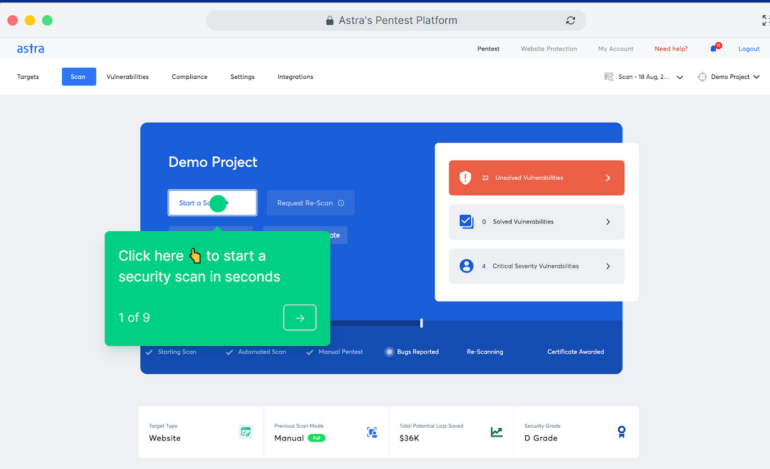
Astra: Greatest for numerous infrastructure

Astra is a penetration testing instrument resolution with a number of automated testing options that mix guide with automated penetration testing options for purposes, networks, API, and blockchain. With over 8,000 assessments supported, this instrument can assist safety professionals examine vulnerabilities inside a system. Astra covers various kinds of penetration testing, together with net app pentest, cloud safety pentest, and cellular app pentest.
As a complete penetration testing resolution, Astra covers many assessments that may assist organizations meet compliance requirements. A few of the compliance requirements that Astra can examine embody SOC2, GDPR, and ISO 27001. The Astra instrument additionally integrates with GitLab, Jira, and Slack and infuses safety right into a steady integration/steady deployment (CI/CD) pipeline.
Why I picked Astra
I picked Astra for its Enterprise Internet App subscription, which accommodates completely different infrastructures. Particularly, it may be used on net, cellular, cloud, and community infrastructures, providing a number of targets throughout varied asset varieties. That is on prime of Astra’s 8,000+ out there assessments and its big selection of integrations with different common software program.
Pricing
Astra’s pricing is categorized into net app, cellular app, and AWS cloud safety, every with completely different pricing.
- Internet app: Scanner – $1,999/12 months, Pentest – $5,999/12 months, Enterprise – $9,999/12 months.
- Cell: Pentest – $2,499/12 months and Enterprise – $3,999/12 months.
- AWS cloud safety: Below this are the Fundamental and Elite plans, and each require customers to talk to the gross sales group for a quote.
Options
- Covers 8,000+ assessments scanning.
- Covers all assessments required for ISO 27001, HIPAA, SOC2, and GDPR.
- Integration with GitLab, GitHub, Slack, and Jira.
- PWA/SPAs apps scanning assist.
- Help via Slack and Microsoft Groups.
Integrations
- Slack workspaces.
- Jira.
- GitHub.
- GitLab.
- Azure.
- CircleCI.
Astra execs and cons
| Execs | Cons |
|---|---|
| Helps publicly verifiable pentest certificates, which will be shared with customers. | What is meant to be a free trial is charged at $1 per day. |
| Presents one of many widest testing coverages (over 8,000). | Help through Slack and MS Groups is just out there on the Enterprise plan. |
| Checks are automated with AI/ML. | |
| Help through Slack or Microsoft Groups. |
Acunetix: Greatest for pentest automation

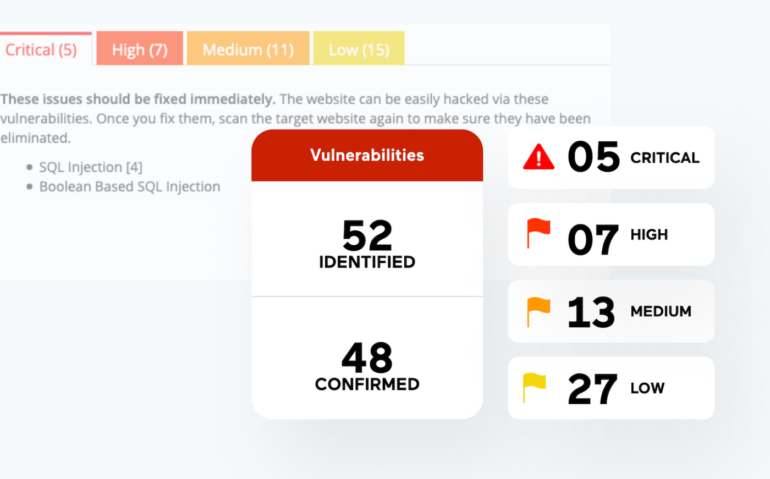
Acunetix by Invicti is a strong pen-testing instrument for net purposes. The answer is filled with scanning utilities that may assist penetration take a look at groups shortly get an perception into over 7,000 net utility vulnerabilities and supply an in depth report masking the scope of vulnerability.
A few of the notable vulnerabilities Acunetix can detect embody XSS, SQL injections, uncovered databases, out-of-band vulnerabilities, and misconfigurations.
Acunetix comes with a dashboard that may type vulnerabilities into lessons, reminiscent of vital, excessive, medium, and low. The instrument is written in C++ and might run on Microsoft Home windows, Linux, macOS, and the cloud.
Why I picked Acunetix
For companies particularly searching for automated pentesting, I like Acunetix. It gives scheduled or recurring utility scans, contains over 7,000 vulnerability assessments, and generates helpful insights earlier than a scan is midway via. I think about it to be a fantastic resolution for organizations that need a no-nonsense pentest instrument that saves them time with out sacrificing general safety.
Pricing
Contact Acunetix for a quote.
Options
- Vulnerability categorization into an order of severity.
- Over 7,000 net app vulnerabilities are supported.
- Covers the OWASP Prime 10 customary for builders and net utility safety.
- Scan scheduling performance.
- Compatibility with issue-tracking instruments like Jira and GitLab.
Integrations
- Jira.
- Azure DevOps.
- GitHub.
- GitLab.
- Bugzilla.
- Mantis.
Acunetix execs and cons
| Execs | Cons |
|---|---|
| Detected vulnerabilities are categorised in accordance with their severity degree. | No pricing particulars for customers. |
| Helps reporting and documentation. | Absence of a free trial. |
| Over 7,000 vulnerability assessments are a broad protection. | |
| Customers can schedule one-time or recurring scans. | |
| Helps concurrent scanning of a number of environments. |
Options
- Cloud vulnerability scanning.
- Internet vulnerability scanning.
- API vulnerability scanning.
- Compliance and reporting options.
- Inner and exterior vulnerability scanning.
Integrations
- Amazon Internet Companies (AWS).
- Drata.
- Jira.
- GitHub.
- GitLab.
- Google Cloud.
Intruder execs and cons
| Execs | Cons |
|---|---|
| Presents a 14-day free trial. | Doesn’t specify the variety of assessments lined. |
| The supply of a demo makes it simpler for first-time customers to get began with the instrument. | The 14-day free trial is just out there beneath the Professional plan. |
| Auto-generates reviews for compliance. |
Options
- Integrations through Distant API.
- Automated credentials brute forcing.
- Automated reporting capabilities.
- Job chains for automated customized workflows.
Integrations
- InsightVM.
- Python.
- Core Impression.
- Burp Suite.
- Challenge Sonar.
- Nexpose.
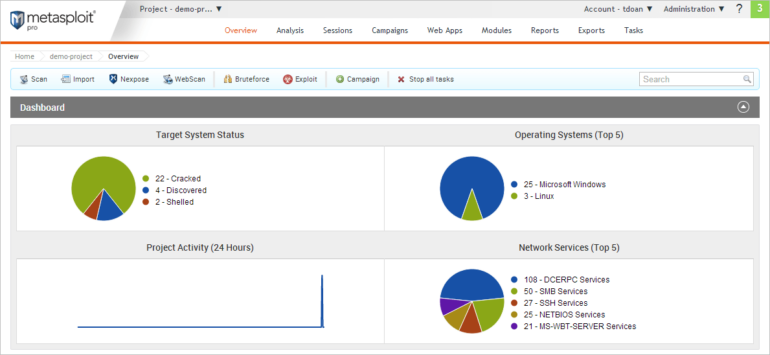
Metasploit execs and cons
| Execs | Cons |
|---|---|
| Presents a 30-day free trial. | The Framework model is proscribed in performance. |
| Makes use of a easy net interface. | The Github obtain and setup methodology is likely to be troublesome for brand new customers. |
| Has a free version for builders and researchers. | |
| Accessible as open-source and business software program. |
Core Impression: Greatest for collaboration

Core Impression, now part of Fortra, ranks as one of many oldest penetration testing instruments which have developed alongside the present calls for of a testing setting. The software program can facilitate the method of assault replication throughout endpoints, community infrastructures, the net, and purposes to disclose exploited vulnerabilities and supply recommendations for remediation.
Core Impression reduces the necessity for guide configuration throughout set up and testing. Customers can simply outline take a look at scope and set testing parameters, and Core Impression does the remaining. As well as, this instrument can generate an assault map, giving customers a real-time report of assault actions throughout testing.
Why I picked Core Impression
I chosen Core Impression for its robust concentrate on group testing. It permits plenty of safety testers to work together with every in the identical session. This enables testing groups to simply share findings and knowledge, in addition to smoother delegation of testing duties. With Core Impression’s emphasis on shared workspaces, testing turns into extra environment friendly and holistic in consequence.
Pricing
Core Impression has three pricing plans:
- Fundamental: Begins at $9,450/consumer per 12 months.
- Professional: Begins at $12,600/consumer per 12 months.
- Enterprise: Request a quote.
Options
- Automated Speedy Penetration Checks (RPTs).
- Multi-vector testing functionality that features community, consumer and net.
- Vulnerability validation of third-party scanner outcomes.
- Centralizes pen testing, from data gathering to reporting.
- Pen testing covers community safety, net utility, IoT safety, and cloud safety.
Integrations
- Metasploit.
- Cobalt Strike.
- PowerShell.
- Empire.
- PlexTrac.
Core Impression execs and cons
| Execs | Cons |
|---|---|
| Makes use of automation wizards to find, take a look at and report. | Pricing could be very costly. |
| Free trial out there. | Free trial doesn’t state how lengthy the trial interval lasts. |
| Presents broader cybersecurity providers. | |
| New customers can be taught concerning the instrument through a demo. |
Kali Linux: Greatest for technical customers

Kali Linux is an open-source pen testing resolution that runs on the Debian-based Linux distribution. The instrument has superior multi-platform options that may assist cellular, desktop, Docker, subsystems, digital machines, and naked steel testing.
As an open-source instrument, professionals can simply customise it to match their testing conditions. There’s detailed documentation on utilizing Kali’s meta packages to generate software program variations for particular testing functions. Kali additionally saves customers the time to manually arrange instruments by including an automatic configuration system that optimizes the instrument in accordance with completely different use circumstances.
Why I picked Kali Linux
Kali Linux is my decide for technical and skilled pentesters searching for a strong testing resolution. It was designed with skilled penetration testers in thoughts, providing a extremely customizable structure that lets pen testers construct their very own software program model tailor-made to their wants.
I significantly admire how Kali Linux is upfront in saying that it’s made for veteran pentesters and skilled Linux customers, not on a regular basis customers. This enables their instrument to be pretty much as good as it may be for his or her chosen user-base as a substitute of making an attempt to accommodate all customers, which can reduce general high quality.
Pricing
It’s out there utterly freed from cost.
Options
- Metapackages can be utilized for particular duties.
- Presents Dwell USB Boot for straightforward booting from a USB gadget.
- Helps over 600 penetration testing utilities.
- Open-source improvement mannequin will be accessed on GitHub.

Integrations
- AWS.
- Azure.
- Digital Ocean.
- Linode.
Kali Linux execs and cons
| Execs | Cons |
|---|---|
| Helps a wide selection of variations. | Largely excellent for superior Linux customers. |
| Accessible without spending a dime. | |
| Programs and documentation can be found for brand new customers. | |
| Multi-language assist. |
Wireshark: Greatest for Unix OS

The Wireshark instrument can analyze and take a look at a company’s community protocol for threats. The instrument is a multi-platform penetration testing utility with helpful options reminiscent of dwell seize, offline, and VoIP evaluation.
As an open-source instrument, Wireshark gives plenty of assist for its customers via documentation, webinars, and video tutorials. The instrument additionally gives decryption options for arrays of protocols reminiscent of Kerberos, SSL/TLS, and WEP.
Why I picked Wireshark
I selected Wireshark for being an excellent decide for Unix OS customers. As a very free and open-source instrument, Wireshark permits customers to check community protocols and see what’s occurring in each broad and advantageous element. Whereas it may be technically intimidating, I just like the in-depth documentation it gives to customers enthusiastic about utilizing Wireshark for his or her particular testing wants.
Pricing
It’s out there without spending a dime.
Options
- Accessible for UNIX and Home windows.
- Seize dwell packet knowledge from a community interface.
- Show filters for sorting via and analyzing visitors streams.
- Helps offline and VoIP evaluation.
Integrations
- AirPcap.
- YR20 community seize {hardware}.
- Inside Merchandise.
- C5 SIGMA.
Wireshark execs and cons
| Execs | Cons |
|---|---|
| It’s out there without spending a dime and is open supply. | Setup is likely to be too technical for brand new customers. |
| There’s an export objects operate for exporting take a look at outcomes. | Restricted automated functionalities. |
| It may be used for decryption throughout a variety of protocols. | |
| High quality documentation for brand new customers. |
SQLMap: Greatest for detecting SQL injection assaults

For open-source lovers, SQLMap is a superb penetration testing instrument for detecting and exploiting SQL injections in purposes. Penetration testers make the most of the instrument to hack databases and perceive the depth of vulnerabilities.
As well as, SQLMap has a testing engine that may run a number of SQL injection assaults concurrently, lowering the time spent working the take a look at. Some notable servers supported on the platform are Microsoft Entry, IBM DB2, SQLite, and MySQL.
Additionally it is a cross-platform instrument, supporting macOS, Linux, and Home windows working methods.
Why I picked SQLMap
For companies trying to shield in opposition to SQL injection assaults, I strongly suggest having SQLMap in your record. It’s a high-quality pentest instrument that’s designed to detect SQL injections mechanically in all forms of purposes. It covers many injection assaults and strategies and has in depth assist for quite a few database administration methods. SQLMap is free and has an excellent quantity of documentation out there on-line.
Pricing
Accessible without spending a dime.
Options
- Helps a number of SQL injection strategies.
- Automated recognition of password hash codecs.
- Help for cracking passwords utilizing a dictionary-based assault.
- Can execute arbitrary instructions and retrieve their customary output.
Integrations
- Burp Suite.
- Metasploit.
- Nmap.
SQLMap execs and cons
| Execs | Cons |
|---|---|
| Covers a broad vary of SQL injection strategies. | Solely appropriate for command-line customers. |
| Appropriate with a number of database administration methods like MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Entry, IBM DB2, and extra. | |
| Accessible without spending a dime. | |
| Has good documentation. |
Key options to search for in penetration testing instruments
Penetration testing options provide a number of options and use circumstances relying on the consumer’s goal. Under are the important thing options of penetration testing options.
Vulnerability scanning
Vulnerability scanning refers back to the technique of trying to find weaknesses and loopholes in software program purposes, networks, and methods. A typical method utilized in pentesting, these scans can detect potential vulnerabilities, reminiscent of outdated software program variations, misconfigurations, and recognized safety flaws.
Community mapping and reconnaissance
Community mapping and reconnaissance discuss with the method of gathering data and creating a visible illustration of a community’s infrastructure and its linked gadgets. Earlier than launching an assault, hackers sometimes collect details about their goal.
Equally, penetration testing instruments help with reconnaissance actions by mapping networks, figuring out lively hosts, and amassing details about the goal infrastructure. This characteristic aids safety professionals in understanding the group’s digital footprint and potential entry factors for attackers.
Visitors evaluation and sniffing
Some penetration testing instruments can analyze community visitors and seize packets. This functionality permits safety professionals to watch and examine community communication, determine potential vulnerabilities, and detect any suspicious or malicious actions. By analyzing community visitors, organizations can acquire worthwhile insights into the safety posture of their methods.
Reporting and documentation
Efficient communication of vulnerabilities and really useful mitigation methods is important within the penetration testing course of. Penetration testing instruments provide reporting and documentation options to generate complete reviews detailing recognized vulnerabilities, steps taken throughout testing, and suggestions for remediation. These reviews support within the prioritization and implementation of safety measures and compliance verification processes.
Customization options
Completely different organizations have distinctive safety necessities. These instruments typically provide customization choices and extensibility options, permitting safety professionals to tailor the testing course of to their particular wants. Customization empowers organizations to concentrate on their most crucial belongings and assess vulnerabilities which are particular to their setting.
Continuously requested questions on penetration testing
What’s the distinction between vulnerability scanning and penetration testing?
Vulnerability scanning appears for weaknesses or holes in your group’s laptop community and reviews it to the group. Penetration testing, alternatively, identifies system vulnerabilities and tries to take advantage of them. This evaluates how a company’s safety measures react throughout an assault.
Performed by moral hackers and DevOps engineers, pen assessments simulate an actual cyber assault in opposition to your group’s safety posture. In the meantime, IT departments sometimes conduct vulnerability scanning to determine safety gaps and supply actionable insights afterward.
As the 2 ideas overlap and diverge in varied areas, different points like scope, aim, and price have to be thought-about. Nevertheless, the outline above is a fast overview of the 2 cybersecurity methods side-by-side.
If you happen to’re enthusiastic about a extra in-depth comparability, you’ll be able to take a look at our Vulnerability Scanning vs Penetration Testing characteristic.
How can penetration testing instruments be used to evaluate community safety?
Moral hackers can do a “community pen take a look at,” a kind of penetration testing particularly focusing on your group’s community infrastructure. With using pen take a look at instruments, organizations can get a first-hand glimpse of how their community safety methods both efficiently or unsuccessfully defend in opposition to malicious actors making an attempt to launch an assault.
Pen take a look at instruments may spotlight gaps or vulnerabilities inside the community itself, which may contain firewall misconfigurations, outdated or buggy software program, and unauthorized entry, amongst others.
What are the constraints of penetration testing?
Whereas pen assessments can produce worthwhile insights relating to your group’s safety posture, they do have limitations. Listed here are just a few:
- Outcomes are restricted by the scope of the pen take a look at, which may depart some areas excluded from the analysis.
- Actual attackers don’t have time constraints, whereas pen assessments are time-bound.
- They are often pricey and resource-intensive, which will be vital limitations to smaller organizations with restricted sources.
- As people, pen testers could make errors or miss vulnerabilities, resulting in incomplete findings.
How do I select the most effective penetration testing software program for my enterprise?
Given the avalanche of pen-testing instruments out there to safety professionals, selecting the best software program is commonly difficult. Listed here are key issues that can assist you select the most effective penetration testing software program in your particular enterprise wants.
Establish your pen testing targets
Earlier than beginning the choice course of, clearly outline your targets for conducting penetration testing. Decide what you purpose to attain via the testing course of, reminiscent of figuring out vulnerabilities in your methods, assessing the effectiveness of your safety controls, or assembly regulatory compliance necessities.
Understanding your targets will enable you to slim down the software program choices that align together with your particular necessities. Our comparability desk exhibits that a few of the instruments are higher than others for various eventualities.
Clearly outline scope and finances for pen testing
Typically you suppose it’s excellent to check your total system setting; nevertheless, defining the price of testing your total software program ecosystem could persuade you in any other case. Each group has excessive and low vulnerability factors. Excessive-risk factors are the areas that malicious actors can simply exploit. They will embody utility code base, configuration information, and working methods.
Figuring out the scope of the take a look at beforehand is a superb means to assist the group plan a penetration testing finances and decide which pen take a look at software program needs to be used.
Account for testing methodologies for use
Penetration testing will be carried out utilizing completely different methodologies, reminiscent of black field, white field, or grey field testing. Consider the software program’s functionality to assist the specified testing methodology. Some instruments could focus on particular forms of testing, so remember to examine that the software program aligns together with your most well-liked strategy. Flexibility in supporting varied testing methodologies will be helpful for those who require completely different approaches for various methods or eventualities.
Take into consideration ease of use and consumer interface
It is best to take into account the software program’s user-friendliness and its consumer interface’s intuitiveness. Penetration testing entails advanced processes, so it’s essential to decide on a instrument that’s simple to navigate and perceive. A well-designed consumer interface and clear documentation can considerably improve your expertise with the software program and enhance productiveness. Whereas a few of the penetration testing instruments I shortlisted provide each GUI and command-line interfaces, some solely assist the command-line interface. Though each interfaces result in the identical consequence, superior customers could also be extra snug with the command-line interface than common customers.
Think about compatibility and integration choices
Assess the compatibility of the software program together with your current IT infrastructure. Make sure that the instrument can seamlessly combine together with your methods, networks, and purposes with out inflicting disruptions. As well as, do consider different compatibility issues because it pertains to working methods, databases, and programming languages supported by the software program.
Moreover, confirm whether or not the instrument can combine together with your present safety options, reminiscent of vulnerability administration platforms or safety data and occasion administration methods.
SEE: SMB Safety Pack (TechRepublic Premium)
Embrace distant sources in testing
Your group’s penetration testing plans ought to embody your distant sources and staff. Organizations that assist distant roles typically present distant entry to worthwhile sources, which will be an entry level for hackers because of poor safety monitoring. Distant sources with restricted safety monitoring methods needs to be lined in any penetration assessments carried out. Excluding distant staff and sources out of your pentests defeat the aim of analyzing your IT infrastructure’s safety posture as a complete.
Methodology
To curate our record of the most effective penetration testing instruments, I researched extensively by extracting data from official web sites, product documentation, case research, and consumer suggestions from dependable third-party overview websites. The standards that knowledgeable our selection embody the important thing options and functionalities lined by the pen testing resolution, the software program’s neighborhood, the software program’s consumer base/reputation, ease of use, and the standard of documentation supplied. All these components knowledgeable our choice course of for this overview.
Luis Millares up to date this text.


