
The Chinese language state-sponsored hacking group Salt Storm has been noticed using a brand new “GhostSpider” backdoor in assaults towards telecommunication service suppliers.
The backdoor was found by Pattern Micro, which has been monitoring Salt Storm’s assaults towards important infrastructure and authorities organizations worldwide.
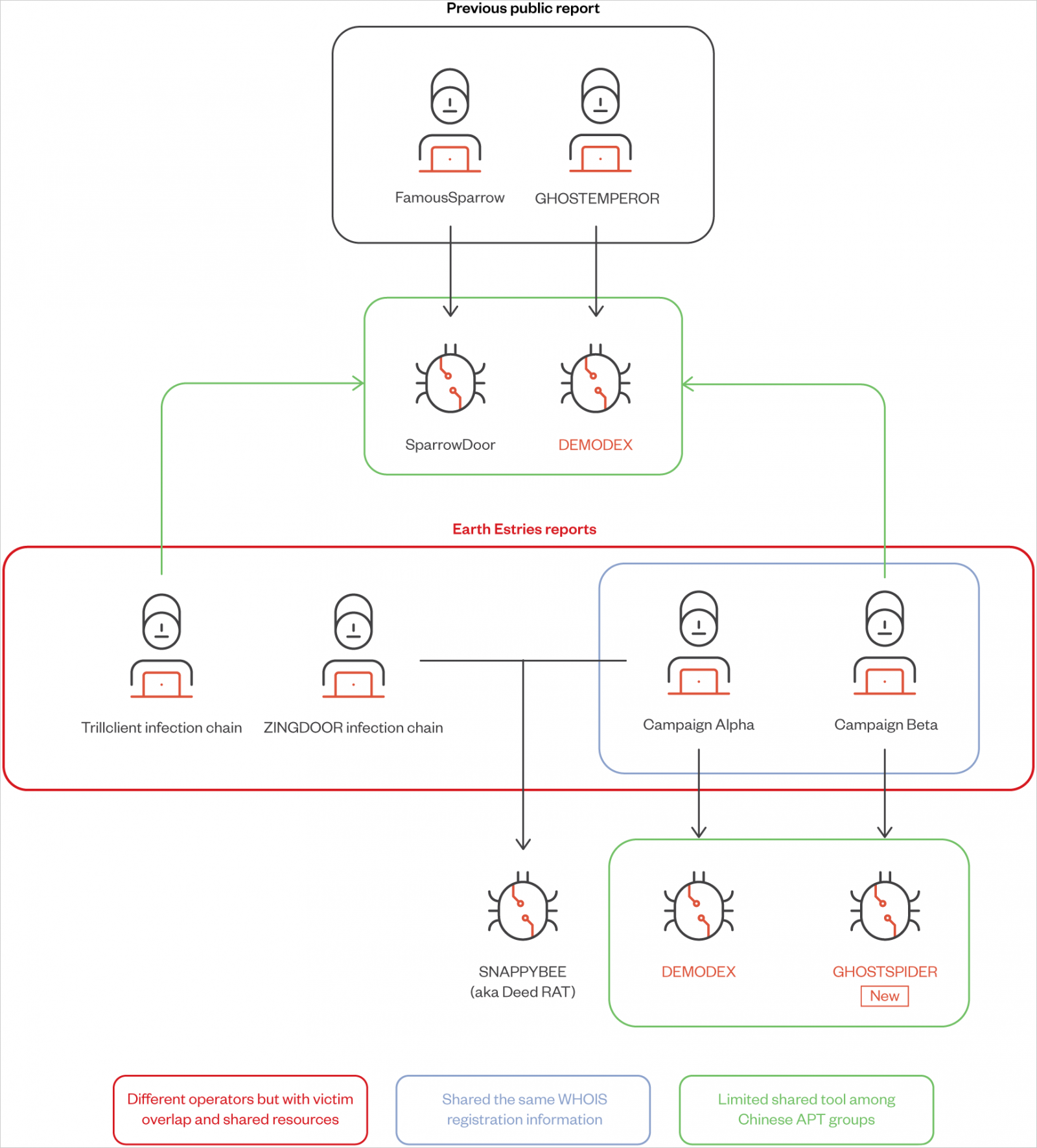
Together with GhostSpider, Pattern Micro found that the menace group additionally makes use of a beforehand documented Linux backdoor named ‘Masol RAT,’ a rootkit named ‘Demodex,’ and a modular backdoor shared amongst Chinese language APT teams named ‘SnappyBee.’
Supply: Pattern Micro
Salt Storm’s international campaigns
Salt Storm (aka ‘Earth Estries’, ‘GhostEmperor’, or ‘UNC2286’) is a complicated hacking group that has been lively since at the very least 2019 and usually focuses on breaching authorities entities and telecommunications corporations.
Not too long ago, the U.S. authorities have confirmed that Salt Storm was behind a number of profitable breaches of telecommunication service suppliers within the U.S., together with Verizon, AT&T, Lumen Applied sciences, and T-Cellular.
It was later admitted that Salt Storm additionally managed to faucet into the non-public communications of some U.S. authorities officers and stole info associated to court-authorized wiretapping requests.
Earlier in the present day, the Washington Publish reported that the authorities within the U.S. notified 150 victims, primarily within the D.C. space, of the truth that Salt Storm had breached the privateness of their communications.
In line with Pattern Micro, Salt Storm has attacked telecommunications, authorities entities, expertise, consulting, chemical substances, and transportation sectors within the U.S., Asia-Pacific, Center East, South Africa, and different areas.
The safety researchers have affirmed at the very least twenty instances of Salt Storm efficiently compromising important organizations, together with, in some situations, their distributors.
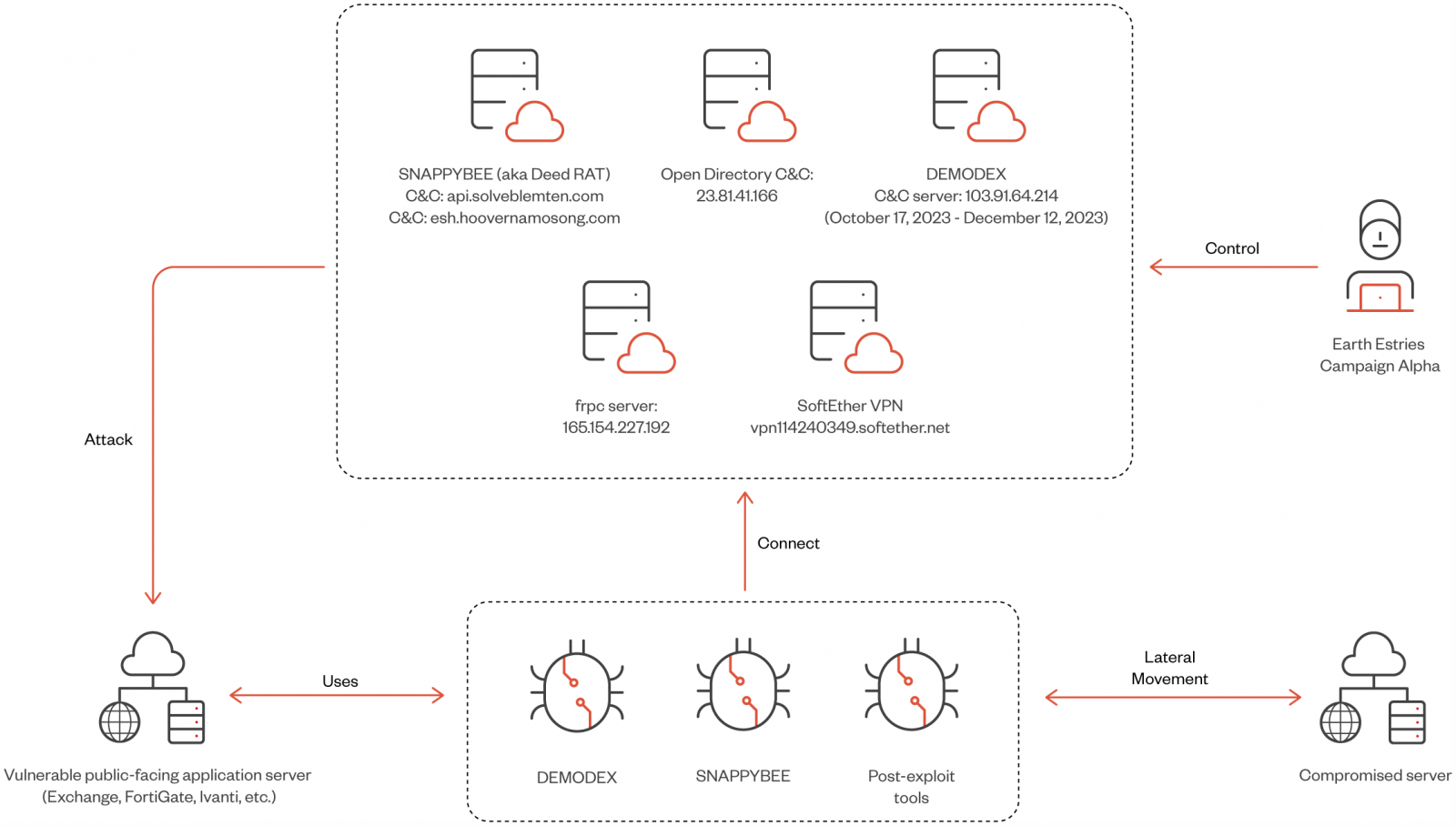
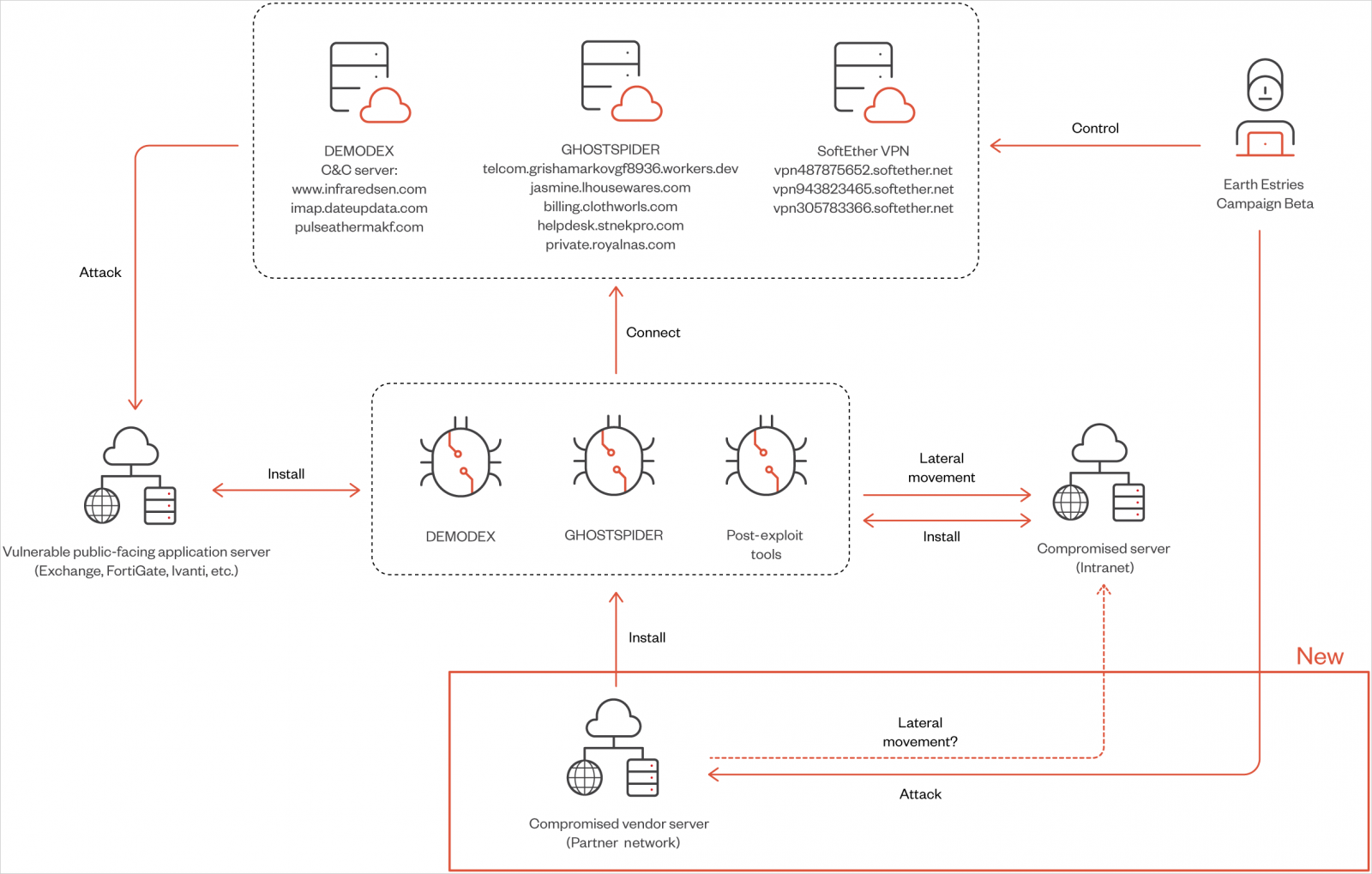
Two campaigns highlighted within the report are ‘Alpha,’ which focused the Taiwanese authorities and chemical producers utilizing Demodex and SnappyBee, and ‘Beta,’ a long-term espionage towards Southeast Asian telecommunications and authorities networks, using GhostSpider and Demodex.
Supply: Pattern Micro
Preliminary entry is achieved by means of the exploitation of weak public-facing endpoints, utilizing exploits for the next flaws:
- CVE-2023-46805, CVE-2024-21887 (Ivanti Join Safe VPN)
- CVE-2023-48788 (Fortinet FortiClient EMS)
- CVE-2022-3236 (Sophos Firewall)
- CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065 (Microsoft Alternate – ProxyLogon)
Salt Storm makes use of LOLbin instruments for intelligence gathering and lateral community motion within the post-compromise section.
Supply: Pattern Micro
GhostSpider particulars
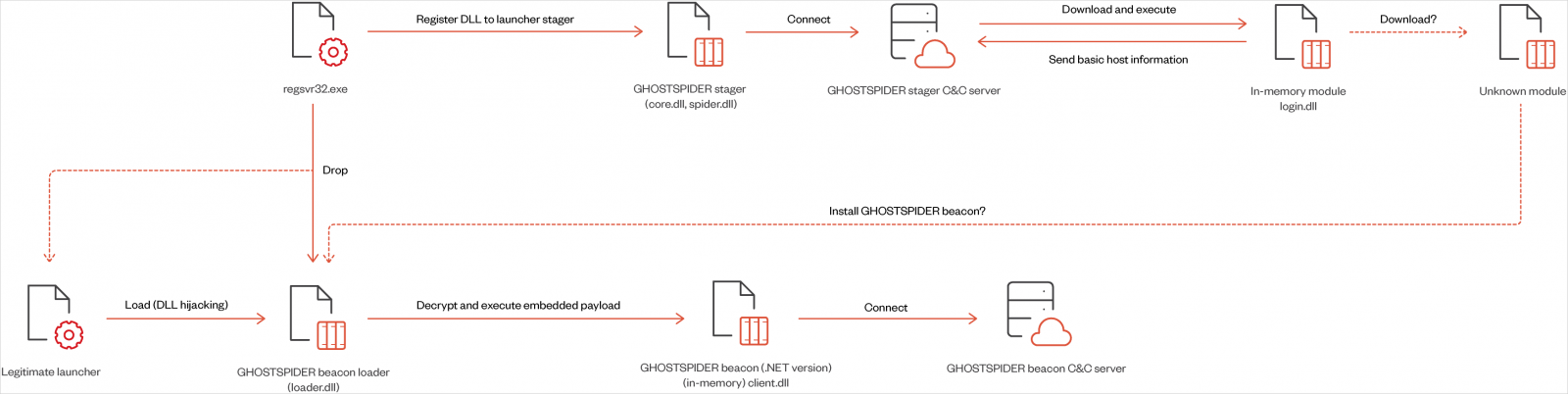
GhostSpider is a modular backdoor designed for long-term espionage operations requiring excessive ranges of stealth, achieved by means of encryption and residing solely in reminiscence.
It is loaded on the goal system utilizing DLL hijacking and registered as a service through the authentic ‘regsvr32.exe’ software, whereas a secondary module, the beacon loader, masses encrypted payloads immediately in reminiscence.
GhostSpider executes instructions obtained from the command and management (C2) server, hid inside HTTP headers or cookies to mix with authentic visitors.
The backdoor helps the next instructions:
- Add: Hundreds a malicious module into reminiscence for execution of particular attacker-controlled duties.
- Create: Prompts the loaded module by initializing obligatory sources for its operation.
- Regular: Executes the first perform of the loaded module, equivalent to information exfiltration or system manipulation.
- Shut: Removes the lively module from reminiscence to reduce traces and free system sources.
- Replace: Adjusts the malware’s habits, equivalent to communication intervals, to stay stealthy and efficient.
- Heartbeat: Maintains periodic communication with the C&C server to substantiate the system remains to be accessible.
The construction of those instructions offers the backdoor versatility and permits Salt Storm to regulate their assault as wanted relying on the sufferer’s community and defenses.
Supply: Pattern Micro
Different instruments utilized by Salt Storm
Other than GhostSpider, Salt Storm depends on a set of proprietary instruments and ones shared amongst different Chinese language menace actors that allow them to conduct advanced, multi-stage espionage operations extending from edge gadgets to cloud environments.
- SNAPPYBEE: Modular backdoor (additionally referred to as Deed RAT) used for long-term entry and espionage. It helps functionalities like information exfiltration, system monitoring, and executing attacker instructions.
- MASOL RAT: Cross-platform backdoor initially recognized focusing on Southeast Asian governments. It focuses on Linux servers, enabling distant entry and command execution.
- DEMODEX: Rootkit used to take care of persistence on compromised techniques. It leverages anti-analysis strategies and ensures the attacker stays undetected for prolonged intervals.
- SparrowDoor: Backdoor offering distant entry capabilities, used for lateral motion and establishing C&C communication.
- CrowDoor: Backdoor used for espionage, notably focusing on authorities and telecommunications entities, targeted on stealth and information exfiltration.
- ShadowPad: Malware shared amongst Chinese language APT teams, used for espionage and system management. It acts as a modular platform to deploy varied malicious plugins.
- NeoReGeorg: Tunneling software used for creating covert communication channels, permitting attackers to bypass community defenses and management compromised techniques.
- frpc: Open-source reverse proxy software used for creating safe connections to C&C servers, enabling information exfiltration and distant command execution.
- Cobalt Strike: Commercially out there penetration testing software co-opted by attackers to create beacons for lateral motion, privilege escalation, and distant management.
All in all, Salt Storm’s arsenal is in depth, together with broadly used instruments that may make attribution difficult when researchers have restricted visibility.
Pattern Micro concludes by characterizing Salt Storm as one of the crucial aggressive Chinese language APT teams, urging organizations to stay vigilant and apply multi-layered cybersecurity defenses.


