Microsoft on Tuesday launched 89 patches affecting 14 product households. Two of the addressed points, each touching Home windows, are thought of by Microsoft to be of important severity. At patch time, two of the problems addressed are recognized to be beneath exploit within the wild, with eight extra CVEs extra prone to be exploited within the subsequent 30 days by the corporate’s estimation. 4 of this month’s points are amenable to detection by Sophos protections, and we embrace data on these in a desk under.
Along with these patches, the discharge consists of advisory data on two Edge-related CVEs, and one associated to Azure, CBL Mariner, and Defender (extra on that advisory under). We’re as at all times together with on the finish of this publish extra appendices itemizing all Microsoft’s patches, sorted by severity, by predicted exploitability, and by product household.
By the numbers
- Complete CVEs: 89
- Publicly disclosed: 3
- Exploit detected: 2
- Severity
- Crucial: 3
- Necessary: 85
- Reasonable: 3
- Impression
- Distant Code Execution: 52
- Elevation of Privilege: 27
- Denial of Service: 4
- Spoofing: 3
- Safety Characteristic Bypass: 2
- Info Disclosure: 1
- CVSS base rating 9.0 or better: 4
- CVSS base rating 8.0 or better: 42
Determine 1: RCE vulnerabilities, bolstered by a powerful exhibiting among the many 31 SQL Server points patched, represent the vast majority of November’s updates
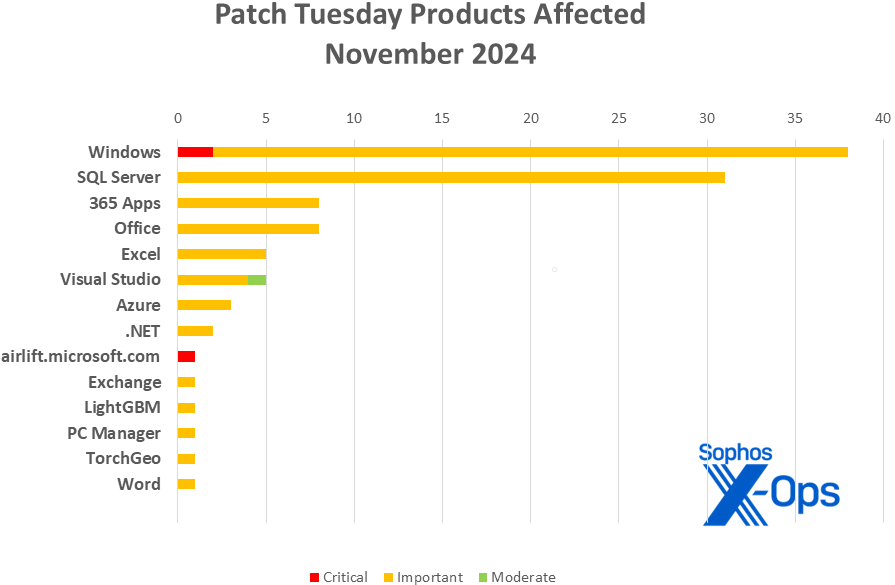
Merchandise
- Home windows: 37
- SQL Server: 31
- 365 Apps: 8
- Workplace: 8
- Excel: 5
- Visible Studio: 5
- Azure: 3
- .NET: 2
- airlift.microsoft.com: 1
- Change: 1
- LightGBM: 1
- PC Supervisor: 1
- TorchGeo: 1
- Phrase: 1
As is our customized for this record, CVEs that apply to multiple product household are counted as soon as for every household they have an effect on.
Determine 2: The number of affected product households rivals final month’s, however Home windows and SQL Server took the overwhelming majority of November’s patches
Notable November updates
Along with the problems mentioned above, various particular gadgets advantage consideration.
31 CVEs – Server 2025 points
As reported in The Register final week, a KB error led to fairly various cases of Server 2019 and 2022 receiving shock upgrades to Server 2025. Although Microsoft ultimately acknowledged and labored to mitigate the issue, as of this writing that course of seems to nonetheless be underway. In the meantime, this month’s Patch Tuesday’s set provides directors yet another excellent purpose to prioritize checking out any surprising Server 2025 presence on their techniques, as over a 3rd of the month’s patches have an effect on the not-yet-official new model. We’ve got listed these CVEs in Appendix E on the finish of this writeup.
CVE-2024-5535 — OpenSSL: CVE-2024-5535 SSL_select_next_proto buffer overread
It’s relegated to the record of advisories, however this RCE, which carries a hefty 9.1 CVSS base rating, deserves a glance. The knowledge out there can be noteworthy (although, as an OpenSSL-assigned CVE, it’s barely totally different to the standard information Microsoft presents on its patches) – the out there data advises that, in a worst-case state of affairs of assault by way of e mail, RCE might be achieved even when the consumer doesn’t open, learn, or click on on a obtained hyperlink. The difficulty impacts model 3.0 of Azure Linux, model 2.0 of CBL Mariner, and Defender for Endpoint on Android, iOS, and Home windows. That mentioned, Microsoft judges it much less prone to be exploited within the subsequent 30 days.
CVE-2024-49039 — Home windows Activity Scheduler Elevation of Privilege Vulnerability
CVE-2024-43451 — NTLM Hash Disclosure Spoofing Vulnerability
These are the 2 CVEs that Microsoft has discovered to be already beneath exploit within the wild. The primary is the extra severe of the 2 – an EoP with a CVSS base rating of 8.8. Each require that the goal system run a malicious software. The spoofing situation, which weighs in at a comparatively much less alarming 6.5 CVSS base, consists of a further shock – IE Cumulative updates for customers of Server 2008, 2008 R2, and 2012 R2 nonetheless taking Safety Solely updates.
CVE-2024-49040 — Microsoft Change Server Spoofing Vulnerability
This Necessary-severity spoofing vulnerability, which Microsoft believes to be extra prone to be exploited throughout the subsequent 30 days, has a moderately particular set of post-installation directions, which might be seen on the corporate’s website.
CVE-2024-49056 — airlift.microsoft.com Elevation of Privilege Vulnerability
An uncommon CVE in opposition to a Microsoft micro-site, this Crucial-severity EoP has already been patched. In line with the data supplied, “Authentication bypass by assumed-immutable information on airlift.microsoft.com enable[ed] a licensed attacker to raise privileges over a community.”
Determine 3: With a month left to go within the 12 months, and after remarkably low CVE counts within the first three months, 2024 has now formally exceeded the patch depend for all of final 12 months – 942 patches to this point in 2024, versus 931 for all of 2023
Sophos protections
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2024-43623 | Exp/2443623-A | Exp/2443623-A |
| CVE-2024-43630 | Exp/2443630-A | Exp/2443630-A |
| CVE-2024-49039 | Exp/2449039-A | Exp/2449039-A |
| CVE-2024-49033 | sid:2310318 | sid:2310318 |
As you may each month, for those who don’t wish to wait on your system to tug down Microsoft’s updates itself, you may obtain them manually from the Home windows Replace Catalog web site. Run the winver.exe software to find out which construct of Home windows 10 or 11 you’re operating, then obtain the Cumulative Replace package deal on your particular system’s structure and construct quantity.
Appendix A: Vulnerability Impression and Severity
It is a record of November patches sorted by influence, then sub-sorted by severity. Every record is additional organized by CVE.
Distant Code Execution (52 CVEs)
| Crucial severity | |
| CVE-2024-43639 | Home windows Kerberos Distant Code Execution Vulnerability |
| Necessary severity | |
| CVE-2024-38255 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-43447 | Home windows SMBv3 Server Distant Code Execution Vulnerability |
| CVE-2024-43459 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-43462 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-43498 | .NET and Visible Studio Distant Code Execution Vulnerability |
| CVE-2024-43598 | LightGBM Distant Code Execution Vulnerability |
| CVE-2024-43602 | Azure CycleCloud Distant Code Execution Vulnerability |
| CVE-2024-43620 | Home windows Telephony Server Distant Code Execution Vulnerability |
| CVE-2024-43621 | Home windows Telephony Server Distant Code Execution Vulnerability |
| CVE-2024-43622 | Home windows Telephony Server Distant Code Execution Vulnerability |
| CVE-2024-43627 | Home windows Telephony Server Distant Code Execution Vulnerability |
| CVE-2024-43628 | Home windows Telephony Server Distant Code Execution Vulnerability |
| CVE-2024-43635 | Home windows Telephony Server Distant Code Execution Vulnerability |
| CVE-2024-43640 | Home windows Kernel-Mode Driver Distant Code Execution Vulnerability |
| CVE-2024-48993 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-48994 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-48995 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-48996 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-48997 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-48998 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-48999 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49000 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49001 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49002 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49003 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49004 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49005 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49006 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49007 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49008 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49009 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49010 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49011 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49012 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49013 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49014 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49015 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49016 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49017 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49018 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49021 | Microsoft SQL Server Distant Code Execution Vulnerability |
| CVE-2024-49026 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49027 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49028 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49029 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49030 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49031 | Microsoft Workplace Graphics Distant Code Execution Vulnerability |
| CVE-2024-49032 | Microsoft Workplace Graphics Distant Code Execution Vulnerability |
| CVE-2024-49043 | Microsoft.SqlServer.XEvent.Configuration.dll Distant Code Execution Vulnerability |
| CVE-2024-49048 | TorchGeo Distant Code Execution Vulnerability |
| CVE-2024-49050 | Visible Studio Code Python Extension Distant Code Execution Vulnerability |
Elevation of Privilege (27 CVEs)
| Crucial severity | |
| CVE-2024-43625 | Microsoft Home windows VMSwitch Elevation of Privilege Vulnerability |
| CVE-2024-49056 | Airlift.microsoft.com Elevation of Privilege Vulnerability |
| Necessary severity | |
| CVE-2024-43449 | Home windows USB Video Class System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43452 | Home windows Registry Elevation of Privilege Vulnerability |
| CVE-2024-43530 | Home windows Replace Stack Elevation of Privilege Vulnerability |
| CVE-2024-43613 | Azure Database for PostgreSQL Versatile Server Extension Elevation of Privilege Vulnerability |
| CVE-2024-43623 | Home windows NT OS Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43624 | Home windows Hyper-V Shared Digital Disk Elevation of Privilege Vulnerability |
| CVE-2024-43626 | Home windows Telephony Server Elevation of Privilege Vulnerability |
| CVE-2024-43629 | Home windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-43630 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43631 | Home windows Safe Kernel Mode Elevation of Privilege Vulnerability |
| CVE-2024-43634 | Home windows USB Video Class System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43636 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-43637 | Home windows USB Video Class System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43638 | Home windows USB Video Class System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43641 | Home windows Registry Elevation of Privilege Vulnerability |
| CVE-2024-43643 | Home windows USB Video Class System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43644 | Home windows Consumer-Aspect Caching Elevation of Privilege Vulnerability |
| CVE-2024-43646 | Home windows Safe Kernel Mode Elevation of Privilege Vulnerability |
| CVE-2024-49019 | Lively Listing Certificates Providers Elevation of Privilege Vulnerability |
| CVE-2024-49039 | Home windows Activity Scheduler Elevation of Privilege Vulnerability |
| CVE-2024-49042 | Azure Database for PostgreSQL Versatile Server Extension Elevation of Privilege Vulnerability |
| CVE-2024-49044 | Visible Studio Elevation of Privilege Vulnerability |
| CVE-2024-49046 | Home windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability |
| CVE-2024-49051 | Microsoft PC Supervisor Elevation of Privilege Vulnerability |
| Reasonable severity | |
| CVE-2024-49049 | Visible Studio Code Distant Extension Elevation of Privilege Vulnerability |
Denial of Service (4 CVEs)
| Necessary severity | |
| CVE-2024-38264 | Microsoft Digital Exhausting Disk (VHDX) Denial of Service Vulnerability |
| CVE-2024-43499 | .NET and Visible Studio Denial of Service Vulnerability |
| CVE-2024-43633 | Home windows Hyper-V Denial of Service Vulnerability |
| CVE-2024-43642 | Home windows SMB Denial of Service Vulnerability |
Spoofing (3 CVEs)
| Necessary severity | |
| CVE-2024-43450 | Home windows DNS Spoofing Vulnerability |
| CVE-2024-43451 | NTLM Hash Disclosure Spoofing Vulnerability |
| CVE-2024-49040 | Microsoft Change Server Spoofing Vulnerability |
Safety Characteristic Bypass (2 CVEs)
| Necessary severity | |
| CVE-2024-43645 | Home windows Defender Utility Management (WDAC) Safety Characteristic Bypass Vulnerability |
| CVE-2024-49033 | Microsoft Phrase Safety Characteristic Bypass Vulnerability |
Info Disclosure (1 CVE)
| Necessary severity | |
| CVE-2024-43500 | Home windows Resilient File System (ReFS) Info Disclosure Vulnerability |
Appendix B: Exploitability
It is a record of the November CVEs judged by Microsoft to be both beneath exploitation within the wild or extra prone to be exploited within the wild throughout the first 30 days post-release. The record is organized by CVE.
| Exploitation detected | |
| CVE-2024-43451 | NTLM Hash Disclosure Spoofing Vulnerability |
| CVE-2024-49039 | Home windows Activity Scheduler Elevation of Privilege Vulnerability |
| Exploitation extra seemingly throughout the subsequent 30 days | |
| CVE-2024-43623 | Home windows NT OS Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43629 | Home windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-43630 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43636 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-43642 | Home windows SMB Denial of Service Vulnerability |
| CVE-2024-49019 | Lively Listing Certificates Providers Elevation of Privilege Vulnerability |
| CVE-2024-49033 | Microsoft Phrase Safety Characteristic Bypass Vulnerability |
| CVE-2024-49040 | Microsoft Change Server Spoofing Vulnerability |
Appendix C: Merchandise Affected
It is a record of November’s patches sorted by product household, then sub-sorted by severity. Every record is additional organized by CVE. Patches which are shared amongst a number of product households are listed a number of occasions, as soon as for every product household.
Home windows (37 CVEs)
| Crucial severity | |
| CVE-2024-43625 | Microsoft Home windows VMSwitch Elevation of Privilege Vulnerability |
| CVE-2024-43639 | Home windows Kerberos Distant Code Execution Vulnerability |
| Necessary severity | |
| CVE-2024-38203 | Home windows Bundle Library Supervisor Info Disclosure Vulnerability |
| CVE-2024-38264 | Microsoft Digital Exhausting Disk (VHDX) Denial of Service Vulnerability |
| CVE-2024-43447 | Home windows SMBv3 Server Distant Code Execution Vulnerability |
| CVE-2024-43449 | Home windows USB Video Class System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43450 | Home windows DNS Spoofing Vulnerability |
| CVE-2024-43452 | Home windows Registry Elevation of Privilege Vulnerability |
| CVE-2024-43530 | Home windows Replace Stack Elevation of Privilege Vulnerability |
| CVE-2024-43620 | Home windows Telephony Server Distant Code Execution Vulnerability |
| CVE-2024-43621 | Home windows Telephony Server Distant Code Execution Vulnerability |
| CVE-2024-43622 | Home windows Telephony Server Distant Code Execution Vulnerability |
| CVE-2024-43623 | Home windows NT OS Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43624 | Home windows Hyper-V Shared Digital Disk Elevation of Privilege Vulnerability |
| CVE-2024-43626 | Home windows Telephony Server Elevation of Privilege Vulnerability |
| CVE-2024-43627 | Home windows Telephony Server Distant Code Execution Vulnerability |
| CVE-2024-43628 | Home windows Telephony Server Distant Code Execution Vulnerability |
| CVE-2024-43629 | Home windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-43630 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43631 | Home windows Safe Kernel Mode Elevation of Privilege Vulnerability |
| CVE-2024-43633 | Home windows Hyper-V Denial of Service Vulnerability |
| CVE-2024-43634 | Home windows USB Video Class System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43635 | Home windows Telephony Server Distant Code Execution Vulnerability |
| CVE-2024-43636 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-43637 | Home windows USB Video Class System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43638 | Home windows USB Video Class System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43640 | Home windows Kernel-Mode Driver Distant Code Execution Vulnerability |
| CVE-2024-43641 | Home windows Registry Elevation of Privilege Vulnerability |
| CVE-2024-43642 | Home windows SMB Denial of Service Vulnerability |
| CVE-2024-43643 | Home windows USB Video Class System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43644 | Home windows Consumer-Aspect Caching Elevation of Privilege Vulnerability |
| CVE-2024-43645 | Home windows Defender Utility Management (WDAC) Safety Characteristic Bypass Vulnerability |
| CVE-2024-43646 | Home windows Safe Kernel Mode Elevation of Privilege Vulnerability |
| CVE-2024-49019 | Lively Listing Certificates Providers Elevation of Privilege Vulnerability |
| CVE-2024-49039 | Home windows Activity Scheduler Elevation of Privilege Vulnerability |
| CVE-2024-49046 | Home windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability |
| CVE-2024-43451 | NTLM Hash Disclosure Spoofing Vulnerability |
SQL Server (31 CVEs)
| Necessary severity | |
| CVE-2024-38255 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-43459 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-43462 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-48993 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-48994 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-48995 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-48996 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-48997 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-48998 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-48999 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49000 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49001 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49002 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49003 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49004 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49005 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49006 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49007 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49008 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49009 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49010 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49011 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49012 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49013 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49014 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49015 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49016 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49017 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49018 | SQL Server Native Consumer Distant Code Execution Vulnerability |
| CVE-2024-49021 | Microsoft SQL Server Distant Code Execution Vulnerability |
| CVE-2024-49043 | Microsoft.SqlServer.XEvent.Configuration.dll Distant Code Execution Vulnerability |
365 Apps (8 CVEs)
| Necessary severity | |
| CVE-2024-49026 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49027 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49028 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49029 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49030 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49031 | Microsoft Workplace Graphics Distant Code Execution Vulnerability |
| CVE-2024-49032 | Microsoft Workplace Graphics Distant Code Execution Vulnerability |
| CVE-2024-49033 | Microsoft Phrase Safety Characteristic Bypass Vulnerability |
Workplace (8 CVEs)
| Necessary severity | |
| CVE-2024-49026 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49027 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49028 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49029 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49030 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49031 | Microsoft Workplace Graphics Distant Code Execution Vulnerability |
| CVE-2024-49032 | Microsoft Workplace Graphics Distant Code Execution Vulnerability |
| CVE-2024-49033 | Microsoft Phrase Safety Characteristic Bypass Vulnerability |
Excel (5 CVEs)
| Necessary severity | |
| CVE-2024-49026 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49027 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49028 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49029 | Microsoft Excel Distant Code Execution Vulnerability |
| CVE-2024-49030 | Microsoft Excel Distant Code Execution Vulnerability |
Visible Studio (5 CVEs)
| Necessary severity | |
| CVE-2024-43498 | .NET and Visible Studio Distant Code Execution Vulnerability |
| CVE-2024-43499 | .NET and Visible Studio Denial of Service Vulnerability |
| CVE-2024-49044 | Visible Studio Elevation of Privilege Vulnerability |
| CVE-2024-49050 | Visible Studio Code Python Extension Distant Code Execution Vulnerability |
| Reasonable severity | |
| CVE-2024-49049 | Visible Studio Code Distant Extension Elevation of Privilege Vulnerability |
Azure (3 CVEs)
| Necessary severity | |
| CVE-2024-43602 | Azure CycleCloud Distant Code Execution Vulnerability |
| CVE-2024-43613 | Azure Database for PostgreSQL Versatile Server Extension Elevation of Privilege Vulnerability |
| CVE-2024-49042 | Azure Database for PostgreSQL Versatile Server Extension Elevation of Privilege Vulnerability |
.NET (2 CVEs)
| Necessary severity | |
| CVE-2024-43498 | .NET and Visible Studio Distant Code Execution Vulnerability |
| CVE-2024-43499 | .NET and Visible Studio Denial of Service Vulnerability |
airlift.microsoft.com (1 CVE)
| Necessary severity | |
| CVE-2024-49056 | Airlift.microsoft.com Elevation of Privilege Vulnerability |
Change (1 CVE)
| Necessary severity | |
| CVE-2024-49040 | Microsoft Change Server Spoofing Vulnerability |
LightGBM (1 CVE)
| Necessary severity | |
| CVE-2024-43598 | LightGBM Distant Code Execution Vulnerability |
PC Supervisor (1 CVE)
| Necessary severity | |
| CVE-2024-49051 | Microsoft PC Supervisor Elevation of Privilege Vulnerability |
TorchGeo (1 CVE)
| Necessary severity | |
| CVE-2024-49048 | TorchGeo Distant Code Execution Vulnerability |
Phrase (1 CVE)
| Necessary severity | |
| CVE-2024-49033 | Microsoft Phrase Safety Characteristic Bypass Vulnerability |
Appendix D: Advisories and Different Merchandise
It is a record of advisories and knowledge on different related CVEs within the November launch.
| CVE-2024-5535 | Azure, CBL Mariner, Defender | OpenSSL: CVE-2024-5535 SSL_select_next_proto buffer overread |
| CVE-2024-10826 | Edge | Chromium: CVE-2024-10826 Use after free in Household Experiences |
| CVE-2024-10827 | Edge | Chromium: CVE-2024-10827 Use after free in Serial |
Appendix E: Server 2025
It is a record of CVEs affecting Server 2025, which some customers could have inadvertently obtained final week.
| CVE-2024-38203 | CVE-2024-43625 | CVE-2024-43639 |
| CVE-2024-38264 | CVE-2024-43626 | CVE-2024-43641 |
| CVE-2024-43449 | CVE-2024-43627 | CVE-2024-43642 |
| CVE-2024-43450 | CVE-2024-43628 | CVE-2024-43643 |
| CVE-2024-43451 | CVE-2024-43629 | CVE-2024-43644 |
| CVE-2024-43452 | CVE-2024-43630 | CVE-2024-43646 |
| CVE-2024-43620 | CVE-2024-43631 | CVE-2024-49019 |
| CVE-2024-43621 | CVE-2024-43635 | CVE-2024-49039 |
| CVE-2024-43622 | CVE-2024-43636 | CVE-2024-49046 |
| CVE-2024-43623 | CVE-2024-43637 | |
| CVE-2024-43624 | CVE-2024-43638 |