The rising reputation of on-line marketplaces has attracted fraudsters preying on unsuspecting patrons and sellers, seeking to rating fee card info quite than to strike a cut price. ESET researchers have discovered that one such organized scammer community – which makes use of Telekopye, a toolkit found by ESET Analysis in 2023 – has expanded its operations to focus on customers of common lodging reserving platforms.
Final yr, we printed a two-part blogpost sequence on Telekopye, a Telegram-based toolkit cybercriminals use to rip-off folks on on-line marketplaces. The first half targeted on Telekopye’s key options, whereas the second half examined the interior workings of the affiliated rip-off teams. On this blogpost, we comply with up on what has modified in Telekopye operations since our final publication, based mostly on our continued monitoring. We glance into how these scammer teams have branched out to concentrating on Reserving.com and Airbnb, in addition to their numerous different efforts to optimize their operations and maximize monetary achieve. Final however not least, we offer steerage on the right way to keep protected against these scams.
We offered our up to date findings on Telekopye on the Virus Bulletin convention on October 2nd, 2024, and in our white paper, which you’ll be able to learn in full right here. The paper was additionally printed on the Virus Bulletin web site.
Key factors of this blogpost:
- ESET Analysis shares up to date findings on Telekopye, a rip-off toolkit designed to assist cybercriminals defraud folks on on-line marketplaces.
- Whereas our earlier analysis explored the technical and organizational background of Telekopye scams, our newest analysis describes the scammers’ numerous efforts to maximise their monetary features – increasing their sufferer pool, benefiting from seasonal alternatives, and bettering their instruments and operations.
- Most notably, Telekopye teams have expanded their concentrating on to common lodging reserving platforms, akin to Reserving.com and Airbnb.
- This new rip-off state of affairs comes with a concentrating on twist, using compromised accounts of authentic motels and lodging suppliers.
- These scams had been particularly prevalent in the summertime vacation season within the focused areas, surpassing Telekopye market scams, in response to ESET telemetry.
Telekopye overview
Telekopye is a toolkit that operates as a Telegram bot, primarily serving as a Swiss Military knife for turning on-line market scams into an organized illicit enterprise. It’s utilized by dozens of rip-off teams, with as much as hundreds of members, to steal hundreds of thousands from Mammoths, as they name the focused patrons and sellers. Neanderthals, as we name the scammers, require little to no technical information – Telekopye takes care of every thing in a matter of seconds.
Found by ESET Analysis in 2023, Telekopye has been in use since a minimum of 2016, with victims everywhere in the world. A number of leads level to Russia because the nation of origin of the bot’s creator(s) and in addition the scammers utilizing it. Telekopye is designed to focus on a big number of on-line companies in Europe and North America, akin to OLX, Vinted, eBay, Wallapop, and others. On the time of writing, we now have counted roughly 90 totally different companies being focused by the scams.
Neanderthals – members of any Telegram group using Telekopye – achieve entry to the bot’s UI, which permits easy technology of phishing emails, SMS messages, net pages, and different options.
Telekopye teams have a business-like operation, with a transparent hierarchy, outlined roles, inside practices – together with admission and mentoring processes for newcomers – mounted working hours, and fee payouts for Telekopye directors. The Staff performing the scams should flip over any delicate info stolen, and don’t really steal any cash – that’s managed by different roles within the group. Every group retains a clear chat of all transactions, seen to all members.
Neanderthals make the most of two principal situations for concentrating on on-line marketplaces – one the place they pose as sellers and one other, rather more frequent, the place they pose as patrons. Each situations finish with the sufferer/Mammoth coming into fee card info or on-line banking credentials right into a phishing net web page mimicking a fee gateway.
Not too long ago, Telekopye teams have expanded their concentrating on by including help for scamming customers of common on-line platforms for reserving lodging, which we cowl within the following part.
Branching out to lodging reserving platforms
In 2024, Telekopye teams have expanded their scamming playbook with schemes concentrating on customers of common on-line platforms for resort and residence reservations, akin to Reserving.com and Airbnb. They’ve additionally elevated the sophistication of their sufferer choice and concentrating on.
Concentrating on with a twist
On this new rip-off state of affairs, Neanderthals contact a focused consumer of one in every of these platforms, claiming that there’s a difficulty with the consumer’s reserving fee. The message comprises a hyperlink to a well-crafted, legitimate-looking net web page mimicking the abused platform.
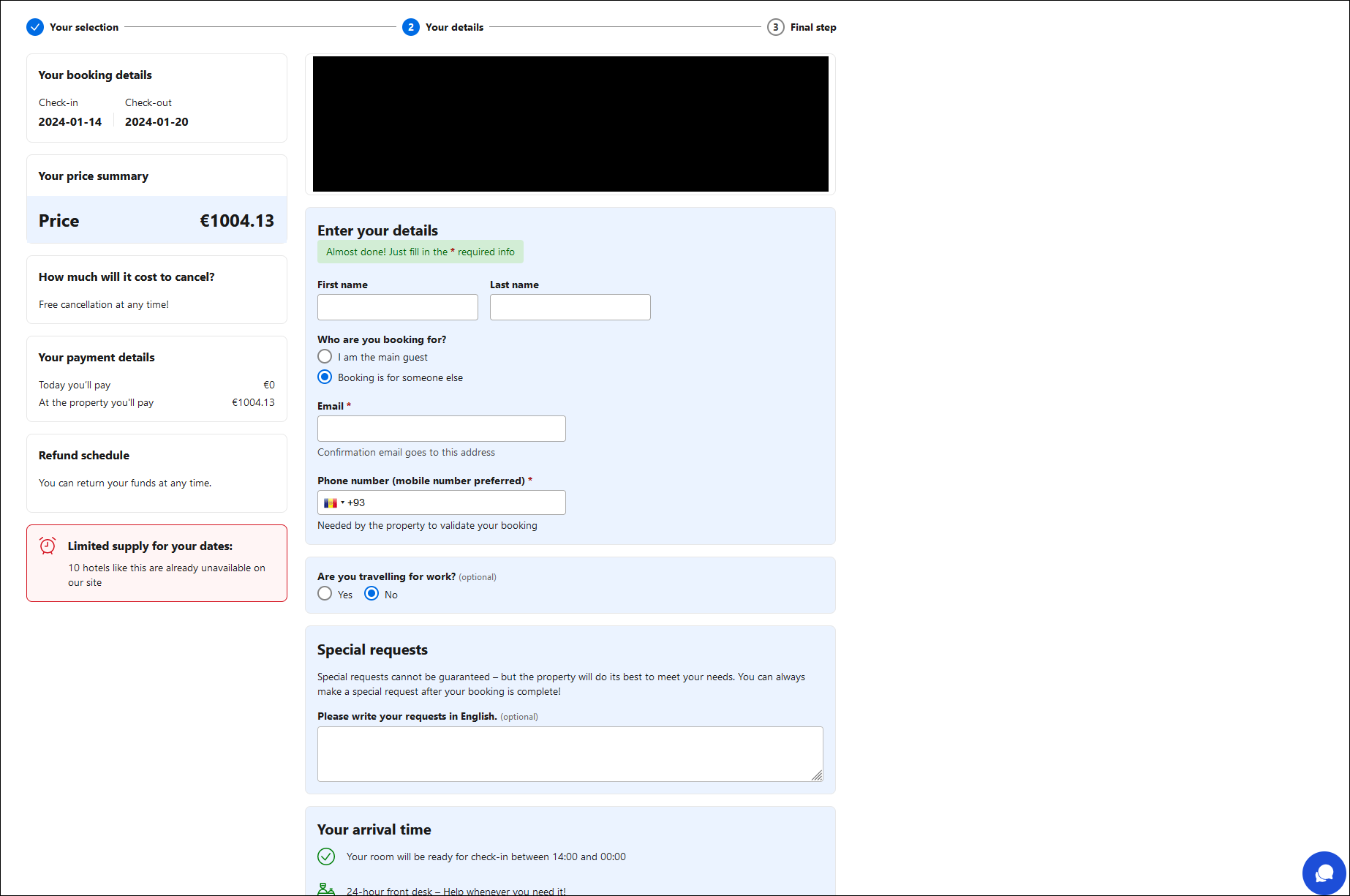
The web page comprises prefilled details about a reserving, such because the check-in and checkout dates, value, and placement. This comes with a troubling twist: the information supplied on the fraudulent pages matches actual bookings made by the focused customers.
The Neanderthals obtain this by using compromised accounts of authentic motels and lodging suppliers on the platforms, which they most definitely entry through stolen credentials bought on cybercriminal boards. Utilizing their entry to those accounts, scammers single out customers who not too long ago booked a keep and haven’t paid but – or paid very not too long ago – and call them through in-platform chat. Relying on the platform and the Mammoth’s settings, this results in the Mammoth receiving an electronic mail or SMS from the reserving platform.
This makes the rip-off a lot tougher to identify, as the data supplied is personally related to the victims, arrives through the anticipated communication channel, and the linked, pretend web sites look as anticipated. The one seen signal of one thing being amiss are the web sites’ URLs, which don’t match these of the impersonated, authentic web sites. Neanderthals may use their very own electronic mail addresses for the preliminary communication (quite than the compromised accounts), during which case the emails is likely to be extra simply acknowledged as malicious.
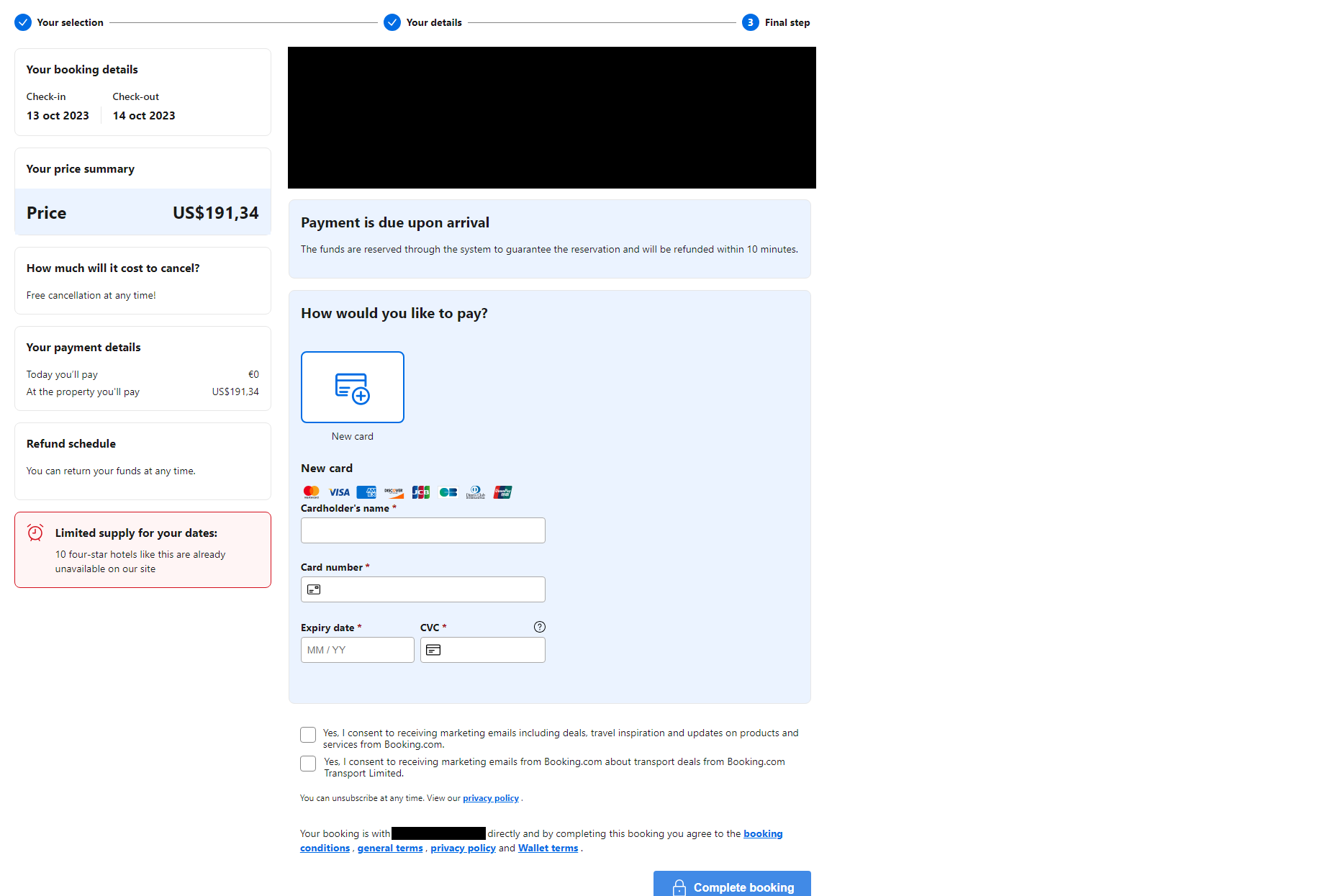
As soon as the goal fills out the shape on the phishing web page (Determine 1), they’re dropped at the ultimate step of the “reserving” – a type requesting fee card info (Determine 2). As within the market scams, card particulars entered into the shape are harvested by the Neanderthals and used to steal cash from the Mammoth’s card.
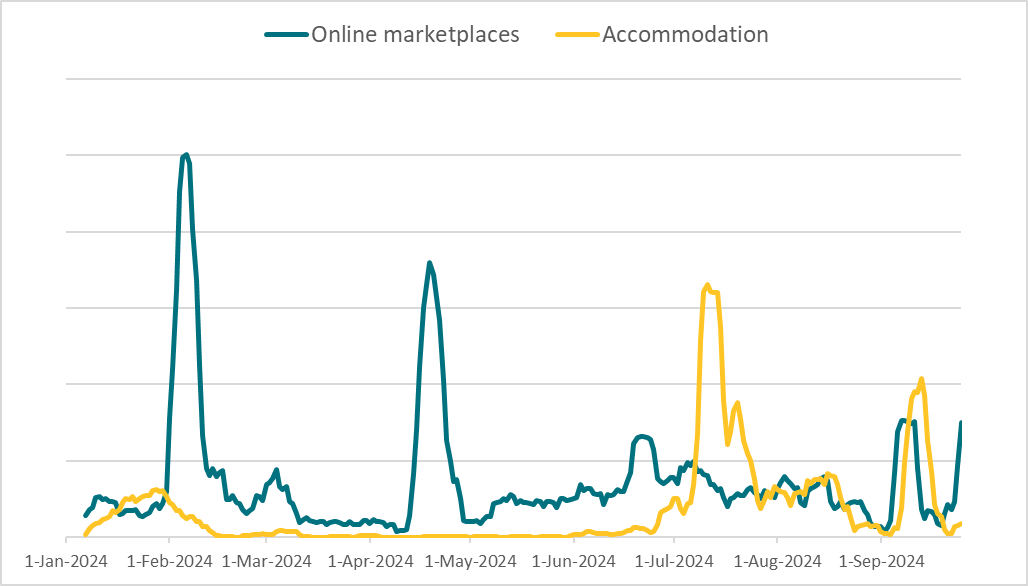
In response to ESET telemetry, the sort of rip-off began gaining traction in 2024. As seen in Determine 3, the accommodation-themed scams noticed a pointy uptick in July, surpassing the unique Telekopye market scams for the primary time, with greater than double the detections throughout that month. In August and September, the detection ranges for the 2 classes evened out.
As this improve coincides with the summer time vacation season within the focused areas – prime time for benefiting from folks reserving stays – it stays to be seen whether or not this development will proceed. Trying on the total 2024 information, we will see that these newer scams have amassed roughly half of the detection numbers of {the marketplace} variants. That is noteworthy contemplating that the newer scams concentrate on two platforms solely, in comparison with the wide range of on-line marketplaces focused by Telekopye.
Superior Telekopye options
Moreover diversifying their goal portfolio, Neanderthals have additionally improved their instruments and operations to extend their monetary returns.
All through our monitoring of Telekopye, we’ve noticed that totally different Telegram teams implement their very own superior options into the toolkit, aimed toward dashing up the rip-off course of, bettering communication with targets, defending phishing web sites in opposition to disruption by rivals, and different targets.
Automated phishing web page technology
To hurry up the method of making rip-off supplies for posing as patrons on marketplaces, Neanderthals carried out net scrapers for common focused platforms. With these, solely the URL to the product is required, as an alternative of getting to manually fill out a questionnaire in regards to the focused Mammoth and product in query. Telekopye parses the net web page and extracts all mandatory info robotically, offering a major speedup for the scammers.
Interactive chatbot with on-the-fly translation
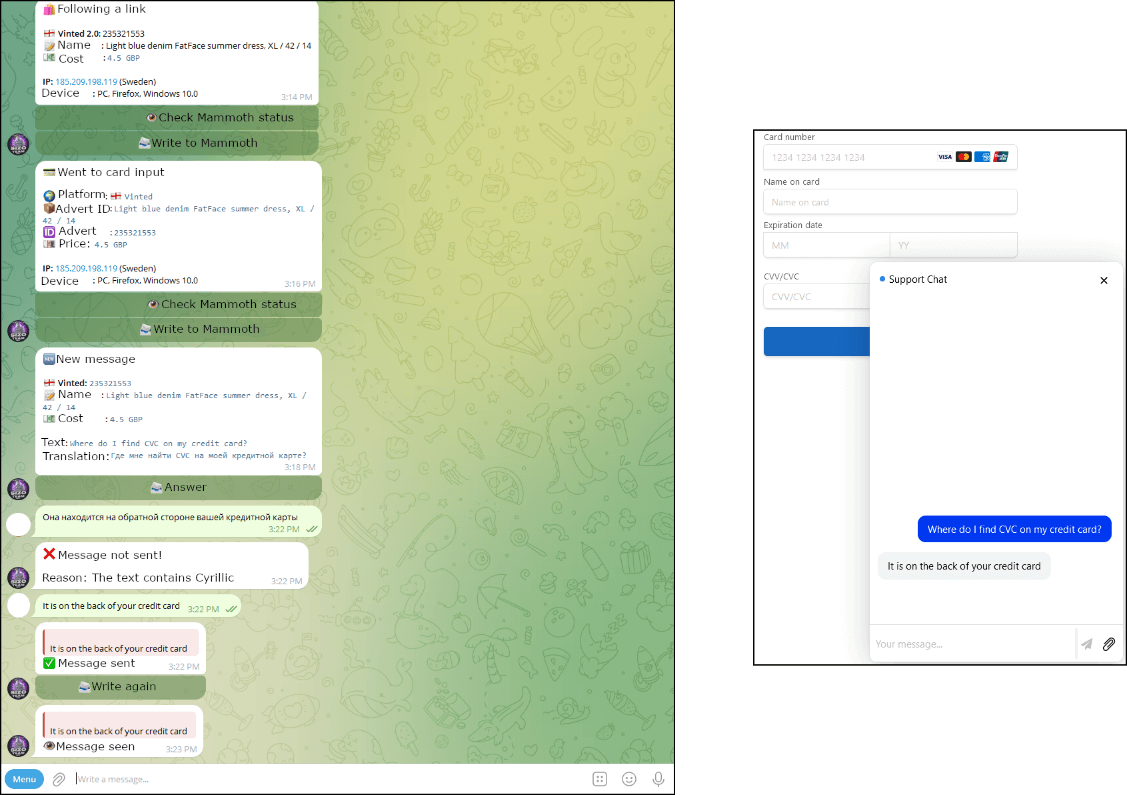
Neanderthals keep a big assortment of predefined solutions to questions generally requested by Mammoths. These are translated into numerous languages and saved as a part of inside documentation, with the translations perfected over time.
Neanderthals usually use these predefined phrases to attempt to direct the Mammoth to the phishing web site, which comes with a chatbot within the decrease proper nook. Any message the Mammoth enters into the chat is forwarded to the Neanderthal’s Telegram chat, the place it’s robotically translated. Automated translation of Neanderthals’ messages isn’t supported – Neanderthals translate their messages manually, normally utilizing DeepL. Determine 3 reveals how such an interplay seems to be from the Neanderthal’s and Mammoth’s factors of view.
Anti-DDoS measures
The overwhelming majority of the phishing web sites are serviced by Cloudflare, counting on that service’s added safety, primarily in opposition to crawlers and computerized evaluation. Apparently, among the Telekopye phishing web sites additionally include DDoS safety included. In response to the Neanderthals’ information base, which we obtained by infiltrating their ranks, this characteristic goals to guard in opposition to assaults by rival teams. These are typically launched as a method to disrupt a competitor’s operations for a brief interval.
Regulation enforcement operations
In late 2023, after ESET Analysis had printed its two-part sequence on Telekopye, Czech and Ukrainian police arrested tens of cybercriminals using Telekopye, together with the important thing gamers, in two joint operations. Each operations had been aimed in opposition to an unspecified variety of Telekopye teams, which had amassed a minimum of €5 million (roughly US$5.5 million) since 2021, based mostly on police estimates.
Moreover the plain success in disrupting such legal actions, the arrests supplied new insights into the teams’ workings, most notably recruitment and employment practices. The teams in query had been managed, from devoted workspaces, by middle-aged males from Japanese Europe and West and Central Asia. They recruited folks in troublesome life conditions, by job portal postings promising “simple cash”, in addition to by concentrating on technically expert international college students at universities.
Some perpetrators confessed that in addition they participated in one other rip-off group, just like the Telekopye ones, that utilized name facilities. The police realized that the recruits in that operation had been usually stripped of their passports and private IDs to make quitting very troublesome. Additional, the managers typically went as far as to threaten the workers and their relations. This chilling growth places these operations into a totally totally different mild.
Suggestions
One of the best ways to remain protected in opposition to scams pushed by Telekopye is being conscious of Neanderthals’ techniques and exercising warning on the affected platforms. Moreover understanding what purple flags to concentrate to, we strongly advocate utilizing a good antimalware answer in your system to step in should you do find yourself being lured to a phishing web site.
On-line market scams
- All the time confirm the individual you might be speaking with, primarily their historical past on the platform, age of their account, ranking, and placement – a location too distant, a contemporary account with no historical past, or a foul ranking is likely to be indicators of a scammer.
- With the enhancements in machine translation, messages from a scammer may not elevate any purple flags when it comes to grammar. Slightly than specializing in the language, concentrate on the dialog itself – overly keen or assertive communication ought to elevate some issues.
- Hold the communication on the platform, even when the individual you’re speaking to suggests in any other case. Their unwillingness to remain on the platform must be a significant purple flag.
- In case you are a purchaser, use safe interfaces inside the platform all through the entire shopping for course of, each time obtainable. In any other case, insist on in-person alternate of products and cash, or prepare on your selection of dependable supply companies with the choice to pay on supply.
- In case you are a vendor, use safe interfaces inside the platform all through the entire promoting course of, each time obtainable. In any other case, handle supply choices your self and don’t conform to these supplied by the customer.
- When you get to a degree the place you do go to a hyperlink despatched by the individual you might be speaking to, remember to rigorously examine the URL, content material, and certificates properties of the web site earlier than participating with it.
Lodging reserving scams
- Earlier than filling out any kinds associated to your reserving, all the time ensure you haven’t left the official web site or app of the platform in query. Being directed to an exterior URL to proceed along with your reserving and fee is an indicator of a attainable rip-off.
- As a result of this rip-off makes use of compromised accounts of lodging suppliers, contacting the suppliers instantly isn’t a dependable approach of verifying the legitimacy of fee requests. When unsure, contact the official buyer help of the platform (Reserving.com, Airbnb) or report a safety subject (Reserving.com, Airbnb).
- To guard your account from compromise, whether or not you’re reserving lodging or renting one out, use a powerful password and allow two-factor authentication wherever obtainable.
Conclusion
Our analysis into Telekopye actions has given us distinctive insights into these scams: we had been in a position to perceive the technical means behind the scope of the operations, the enterprise facet of Telekopye teams, and even study Neanderthals themselves.
We’ve got described the teams’ numerous efforts to maximise their monetary features, together with increasing their sufferer pool, benefiting from seasonal alternatives, and bettering their instruments and operations. Most notably, we now have detailed the Neanderthals’ latest method of concentrating on lodging reserving platforms, which additionally comes with extra refined concentrating on.
It’s value noting that we now have communicated with a number of platforms focused by Telekopye all through our analysis; they’re totally conscious of those scams and confirmed they’ve employed a number of techniques to fight them. Nonetheless, warning remains to be suggested for customers because of the variety of the scams and their steady evolution.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis provides personal APT intelligence experiences and information feeds. For any inquiries about this service, go to the ESET Risk Intelligence web page.
IoCs
Information
| SHA-1 | Filename | Detection | Description |
| E815A879F7F30FB492D4 |
rip-off.php | PHP/HackTool.Telekopye.B | Telekopye bot. |
| 378699D285325E905375 |
rip-off.php | PHP/HackTool.Telekopye.B | Telekopye bot. |
| 242CE4AF01E24DB05407 |
123.php | PHP/HackTool.Telekopye.A | Telekopye bot. |
| 9D1EE6043A8B6D81C328 |
mell.php | PHP/HackTool.Telekopye.B | Telekopye bot. |
| B0189F20983A891D0B9B |
neddoss.php | PHP/HackTool.Telekopye.A | Telekopye bot. |
| E39A30AD22C327BBBD2B |
nscode.php | PHP/HackTool.Telekopye.A | Telekopye bot. |
| 285E0573EF667C6FB7AE |
tinkoff.php | PHP/HackTool.Telekopye.A | Telekopye bot. |
Community
| IP | Area | Internet hosting supplier | First seen | Particulars |
| N/A | 3-dsecurepay[.]com | Cloudflare, Inc. | 2024-05-30 | Telekopye phishing area. |
| N/A | approveine[.]com | Cloudflare, Inc. | 2024-06-28 | Telekopye phishing area. |
| N/A | audittravelerbookdetails[.]com | Cloudflare, Inc. | 2024-06-01 | Telekopye phishing area. |
| N/A | btsdostavka-uz[.]ru | TIMEWEB-RU | 2024-01-02 | Telekopye phishing area. |
| N/A | burdchoureserdoc[.]com | Cloudflare, Inc. | 2024-05-31 | Telekopye phishing area. |
| N/A | check-629807-id[.]high | Cloudflare, Inc. | 2024-05-30 | Telekopye phishing area. |
| N/A | contact-click2399[.]com | Cloudflare, Inc. | 2024-05-26 | Telekopye phishing area. |
| N/A | contact-click7773[.]com | Cloudflare, Inc. | 2024-05-30 | Telekopye phishing area. |
| N/A | get3ds-safe[.]information | Cloudflare, Inc. | 2024-05-31 | Telekopye phishing area. |
| N/A | hostelguest[.]com | Cloudflare, Inc. | 2024-05-30 | Telekopye phishing area. |
| N/A | order-9362[.]click on | Cloudflare, Inc. | 2024-05-29 | Telekopye phishing area. |
| N/A | shiptakes[.]information | Cloudflare, Inc. | 2024-05-29 | Telekopye phishing area. |
| N/A | quickroombook[.]com | Cloudflare, Inc. | 2024-06-02 | Telekopye phishing area. |
| N/A | validation-confi[.]information | Cloudflare, Inc. | 2024-05-29 | Telekopye phishing area. |
MITRE ATT&CK strategies
This desk was constructed utilizing model 15 of the MITRE ATT&CK framework.
| Tactic | ID | Identify | Description |
| Reconnaissance | T1589 | Collect Sufferer Identification Data | Telekopye is used to assemble fee card particulars, cellphone numbers, electronic mail addresses, and so on. through phishing net pages. |
| Useful resource Growth | T1583.001 | Purchase Infrastructure: Domains | Telekopye operators register their very own domains. |
| T1585 | Set up Accounts | Telekopye operators set up accounts at on-line marketplaces. | |
| T1585.002 | Set up Accounts: E mail Accounts | Telekopye operators arrange electronic mail addresses related to the domains they register. | |
| T1586.002 | Compromise Accounts: E mail Accounts | Telekopye operators use compromised electronic mail accounts to extend their stealthiness. | |
| T1587.001 | Develop Capabilities: Malware | Telekopye is customized malware. | |
| T1588.002 | Receive Capabilities: Device | Telekopye operators use extra bots to launder cash, scrape market analysis, and implement DDoS safety. | |
| Preliminary Entry | T1566.002 | Phishing: Spearphishing Hyperlink | Telekopye sends electronic mail or SMS messages that comprise hyperlinks to phishing web sites. |
| Assortment | T1056.003 | Enter Seize: Internet Portal Seize | Internet pages created by Telekopye seize delicate info and report it to the operators. |



